Idm usage strategies, Understanding the idm model – HP Identity Driven Manager Software Series User Manual
Page 22
2-6
Getting Started
Before You Begin
7. If Active Directory synchronization is not used, assign Users to the appropriate
Access Policy Group. (See page 3-49).
8. If automatic deployment is disabled, deploy the configuration policies to the
IDM Agent on the RADIUS server. (See page 3-66)
9. Configure Auto-allow OUIs for the devices that will perform MAC authentica-
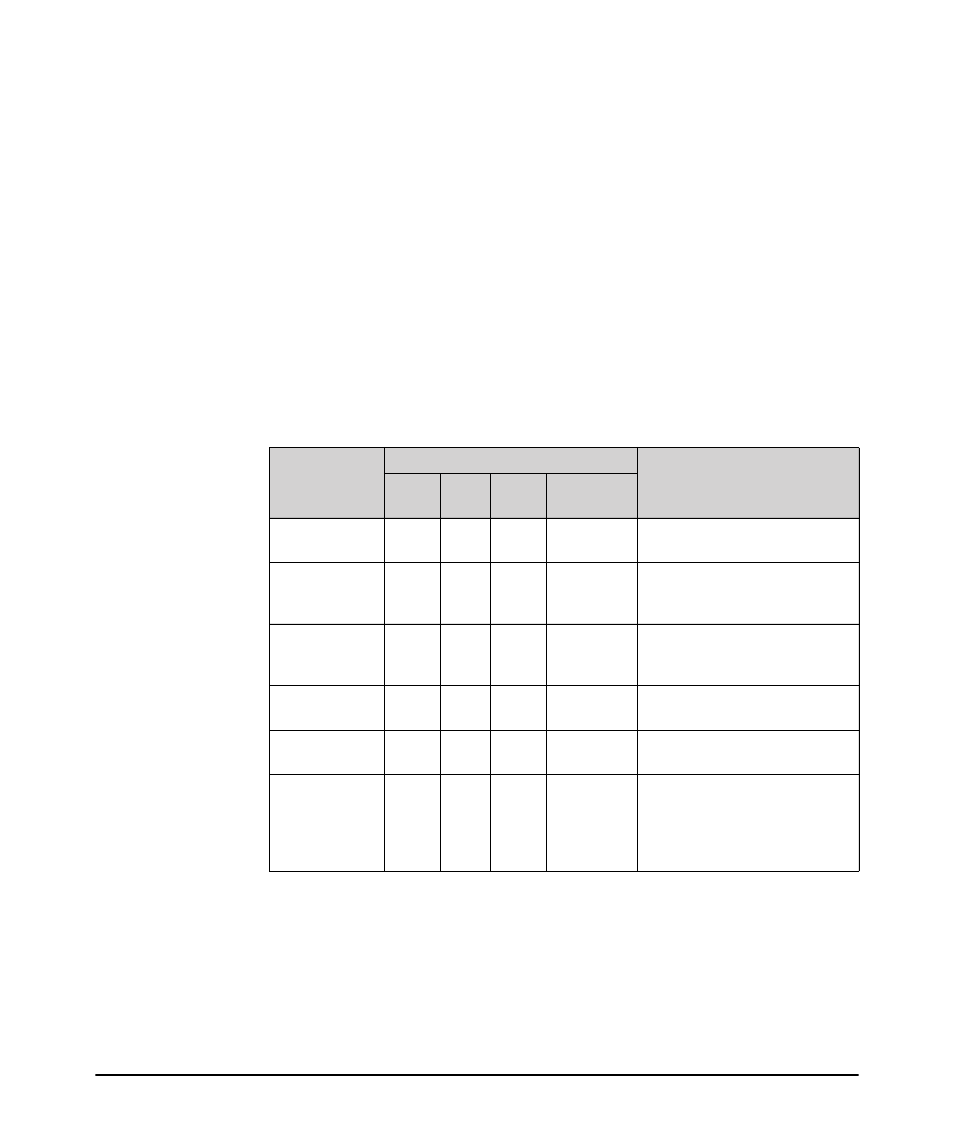
IDM Usage Strategies
You can use IDM to simply monitor user activity on the network, or to apply user
authentication rules to improve network security and performance. The following
table identifies the IDM configuration for various deployment and usage strategies
for IDM.
Understanding the IDM Model
The first thing to understand is that IDM works within the general concept of
“domains.” Basically, domains are very large organizational units; every user belongs
to one, and only one, domain. While it is possible to have multiple domains, most
organizations have only one, for example, hp.com or csuchico.edu.
Table 2-1.
IDM Deployment and Usage Strategies
Authenticate
Authorize
Strategy Description
VLAN
QoS
Rate-
Limit
Network
Resources
Monitors and reports user
activity.
x
Enhances normal RADIUS
authentication with Location,
Time, and System rules
x
x
Provides rudimentary VLAN
segregation (Unknown Users,
Guests, Visitors, Contractors)
x
x
Provides complete VLAN
placement for all Users
x
x
x
Provides QoS and Rate-limits per
User
x
x
x
x
x
Provides VLAN, QoS, and Rate-
limit attributes, and accessibility
of defined Network Resources for
all users, based on Location, Time,
and System
