Securing the wlan, 3 securing the wlan – AASTRA SIP-DECT (Release 2.1)- OM System Manual - Installation, Administration and Maintenance EN User Manual
Page 157
SIP – DECT OM System Manual Release 2.1
7 Configuration und Administration Aspects
depl-1230/1.3
Page: 157 (196)
lowers the clients power consumption slightly. Not all programs can manage the increase in
response times, however.
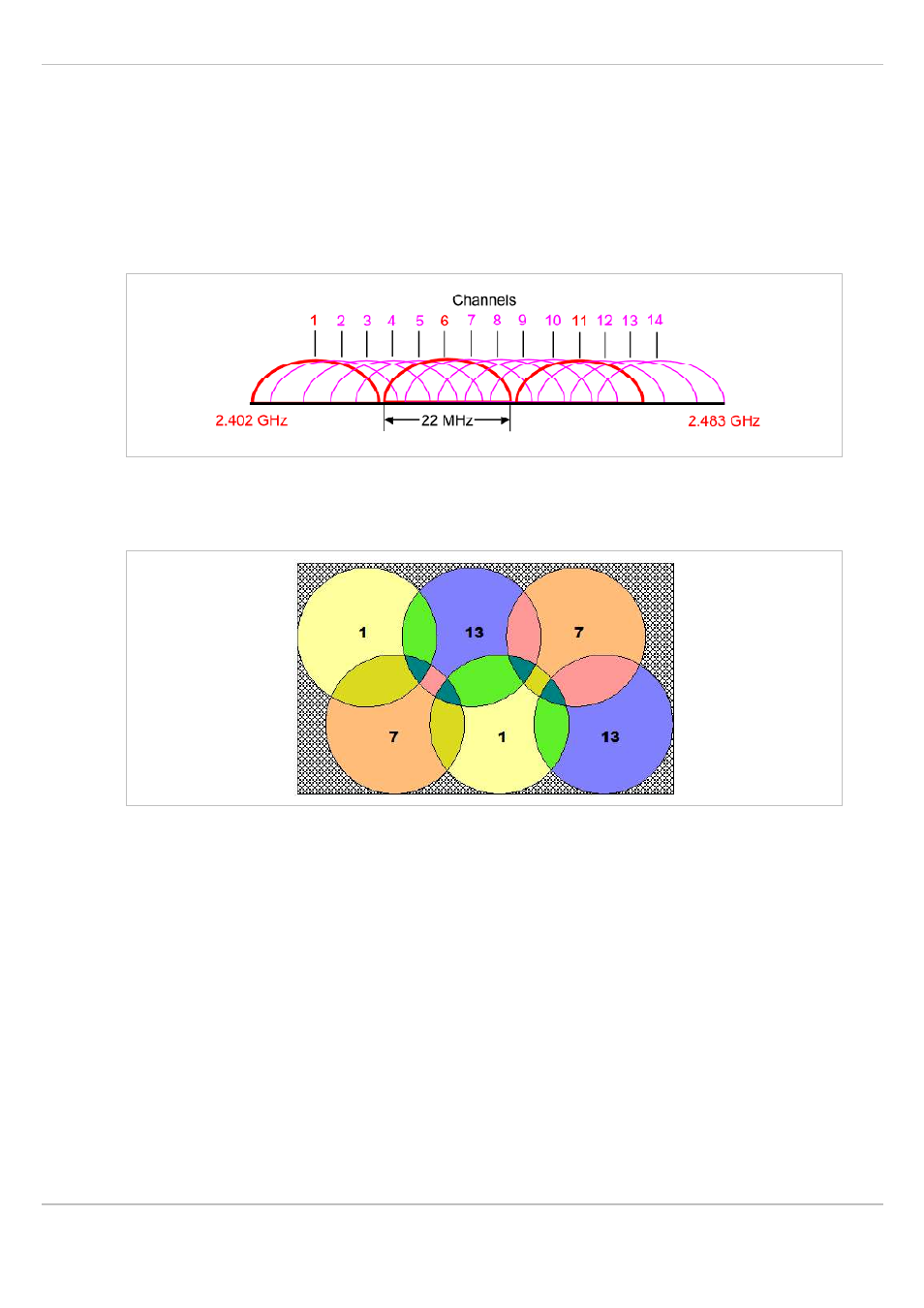
Channel Allocation
Every WLAN RFP must be configured to a channel. You should ensure that the channel
settings do not overlap. WLAN RFPs within range of each other should be configured at least
five channels apart. When the radio field is planned, the WLAN RFPs of foreign WLANs that
may be operating in the vicinity must be taken into account.
When planning the radio coverage for a two-dimensional area, please bear in mind that the
distance between any two base stations operating on the same frequency must be at least
twice their range. The range can be adjusted by lowering the output power level.
7.13.3 Securing the WLAN
In order to ensure that communication in the WLAN network is secure, several measures
need to be taken. Firstly, data packets transmitted via the openly visible radio interface must
be encrypted, and secondly, all WLAN components that provide services should have to
authenticate themselves.
There are different encryption methods available which you configure within the WLAN
profile (see chapter 5.8.1). However, only the recent WiFi protected access (WPA)
encryption offers sufficient security against possible intruders. You should not use the (older)
WEP encryption for your company LAN.
Especially with larger WLAN installations, the single shared secret offered by WPA-personal
may not be sufficient for your security requirements, because any person that connects to
the WLAN needs to know the same shared secret. For this reason, you should also setup
RADIUS authentication that is supported by all RFP 42/L42 devices.
