Fip snooping on ethernet bridges – Dell PowerEdge FX2/FX2s User Manual
Page 70
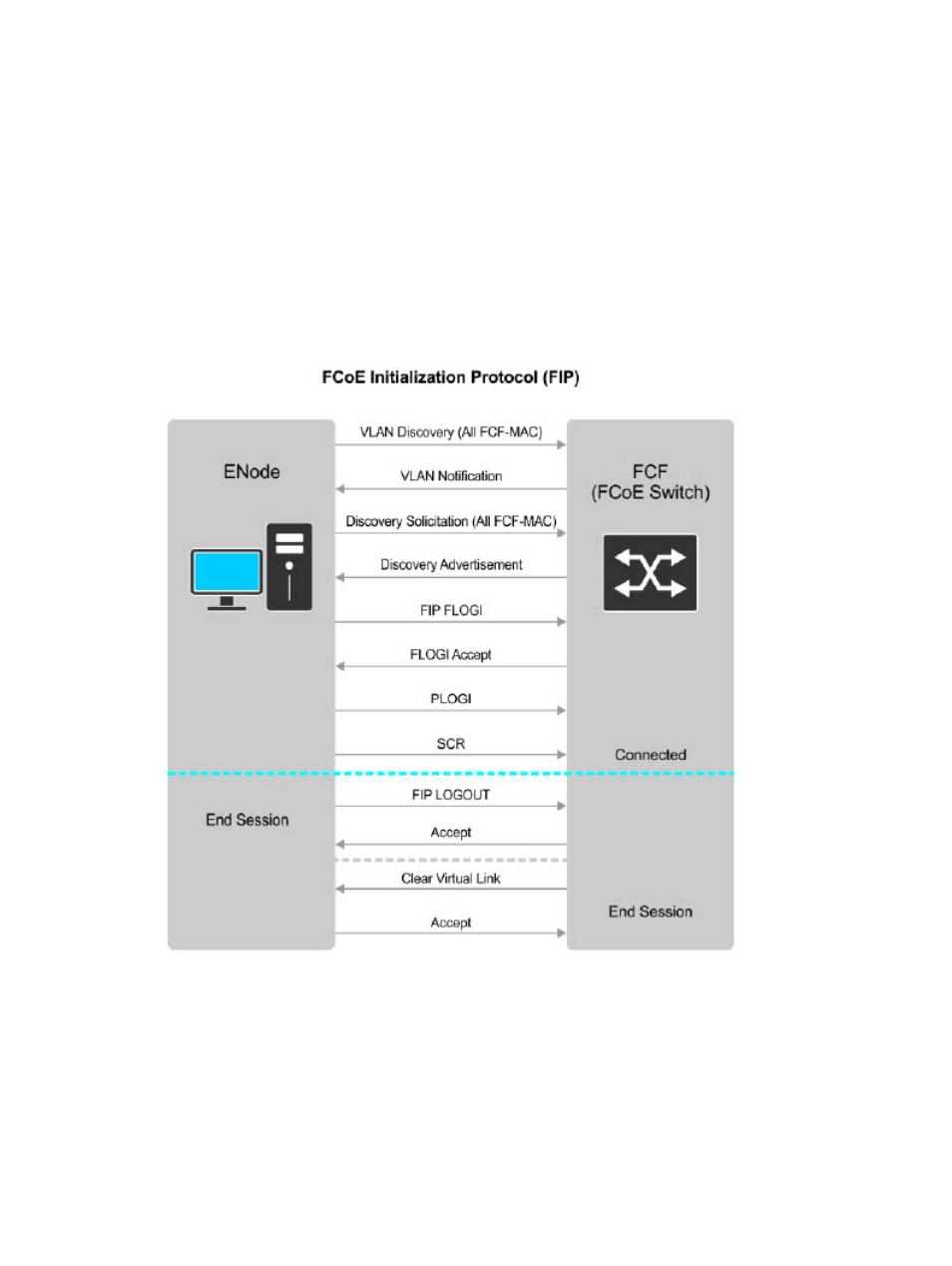
FIP provides a functionality for discovering and logging in to an FCF. After discovering and logging in, FIP
allows FCoE traffic to be sent and received between FCoE end-devices (ENodes) and the FCF. FIP uses its
own EtherType and frame format. The below illustration about FIP discovery, depicts the communication
that occurs between an ENode server and an FCoE switch (FCF).
FIP performs the following functions:
• FIP virtual local area network (VLAN) discovery: FCoE devices (Enodes) discover the FCoE VLANs on
which to transmit and receive FIP and FCoE traffic.
• FIP discovery: FCoE end-devices and FCFs are automatically discovered.
• Initialization: FCoE devices perform fabric login (FLOGI) and fabric discovery (FDISC) to create a virtual
link with an FCoE switch.
• Maintenance: A valid virtual link between an FCoE device and an FCoE switch is maintained and the
link termination logout (LOGO) functions properly.
Figure 7. FIP discovery and login between an ENode and an FCF
FIP Snooping on Ethernet Bridges
In a converged Ethernet network, intermediate Ethernet bridges can snoop on FIP packets during the
login process on an FCF. Then, using ACLs, a transit bridge can permit only authorized FCoE traffic to be
70
FIP Snooping
