Tier 2: time-based, web authentication – 8e6 Technologies Enterprise Filter Authentication R3000 User Manual
Page 223
A
PPENDIX
A: A
UTHENTICATION
O
PERATIONS
T
IER
2: T
IME
-
BASED
, W
EB
A
UTHENTICATION
8
E
6 T
ECHNOLOGIES
, R3000 I
NTERNET
F
ILTER
A
UTHENTICATION
U
SER
G
UIDE
209
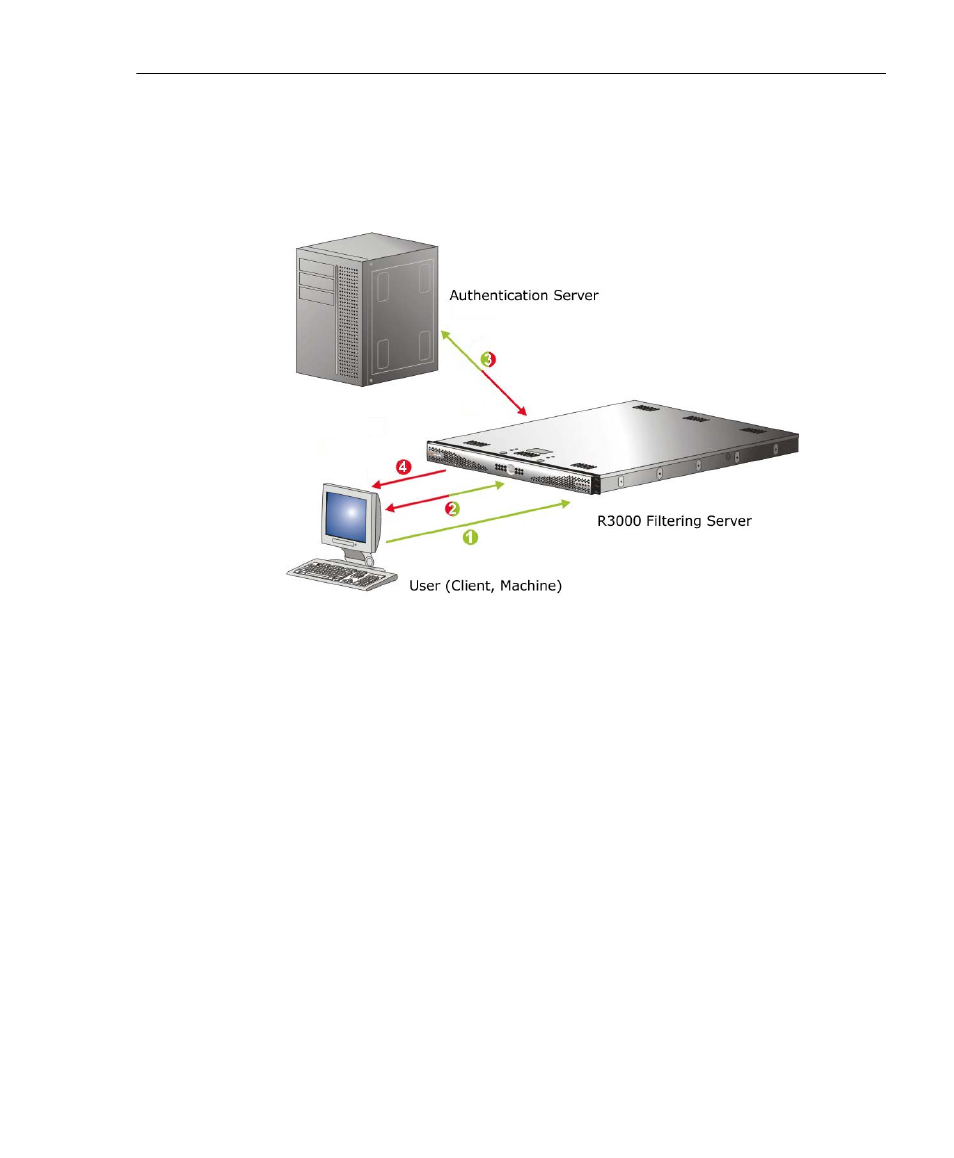
Tier 2: Time-based, Web Authentication
The following diagram and steps describe the operations of
the time-based authentication process:
Fig. A-2 Web-based authentication module diagram
1. The user makes a Web request by entering a URL in his/
her browser window.
2. The R3000 intercepts this request and sends the user
the Authentication Request Form, requesting the user to
log in with his/her login ID and password.
3. The R3000 verifies the user’s information with the
authentication server (Domain Controller, Active Direc-
tory, LDAP, etc.).
4. The authenticated user is allowed to access the
requested URL for the time period specified by the
administrator.
