Net use based authentication process, Tier 1: single sign-on authentication – 8e6 Technologies Enterprise Filter Authentication R3000 User Manual
Page 215
A
PPENDIX
A: A
UTHENTICATION
O
PERATIONS
T
IER
1: S
INGLE
S
IGN
-O
N
A
UTHENTICATION
8
E
6 T
ECHNOLOGIES
, R3000 I
NTERNET
F
ILTER
A
UTHENTICATION
U
SER
G
UIDE
201
Tier 1: Single Sign-On Authentication
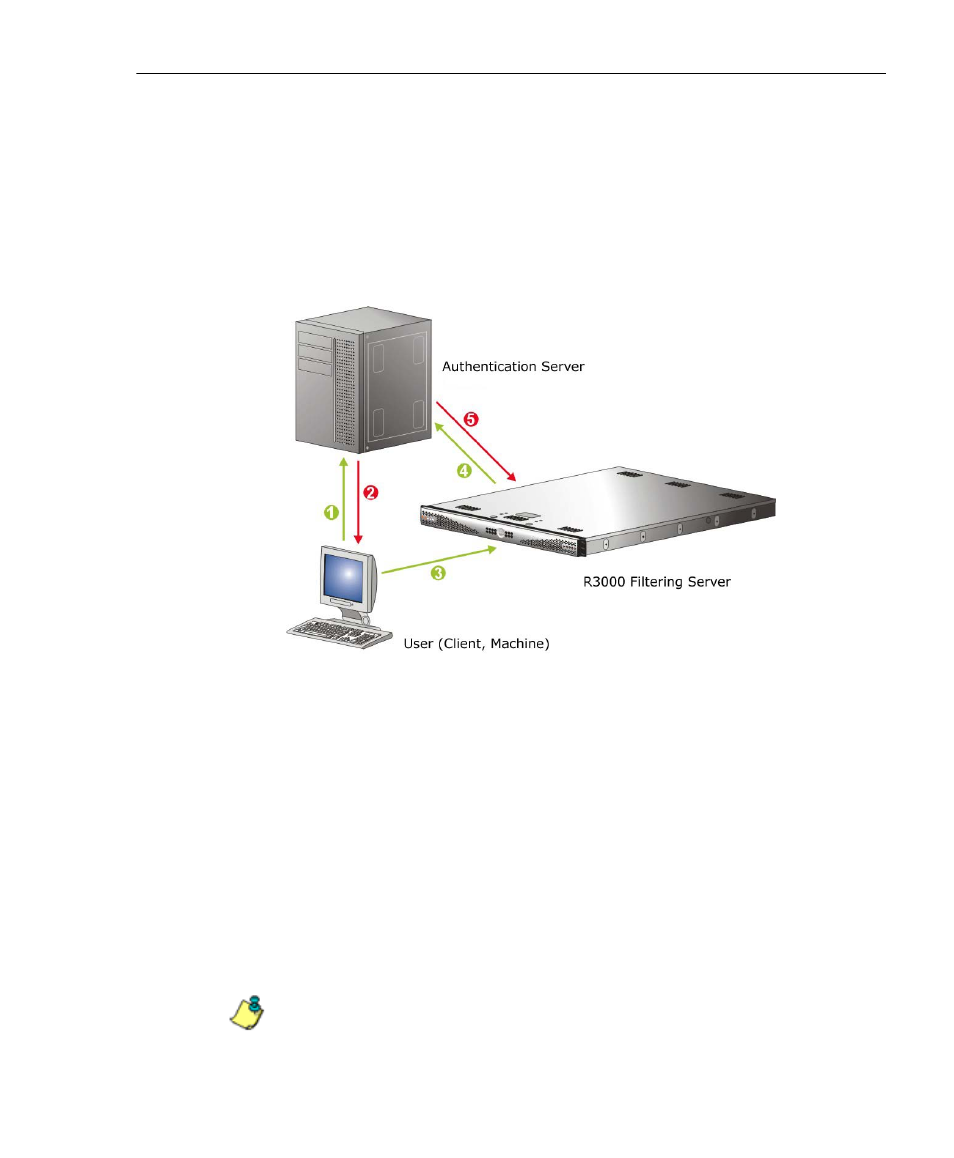
Net use based authentication process
The following diagram and steps describe the operations of
the net use based user authentication process:
Fig. A-1 Net use based authentication module diagram
1. The user logs on the network from a Windows worksta-
tion (also known as “client” or “machine”).
2. The authentication server on the network sends the
user’s workstation a login script containing a net use
command.
3. The execution of this net use command causes the
Windows workstation to create an “IPC share”
(command exchange) with the R3000 filter box as a
shared network device.
NOTE: When the IPC share is created, no drives are mapped in
this share.
