HP TopTools for Hubs and Switches User Manual
Page 199
Setting Up Security for a Device
Switch Intrusion Log
14-19
•
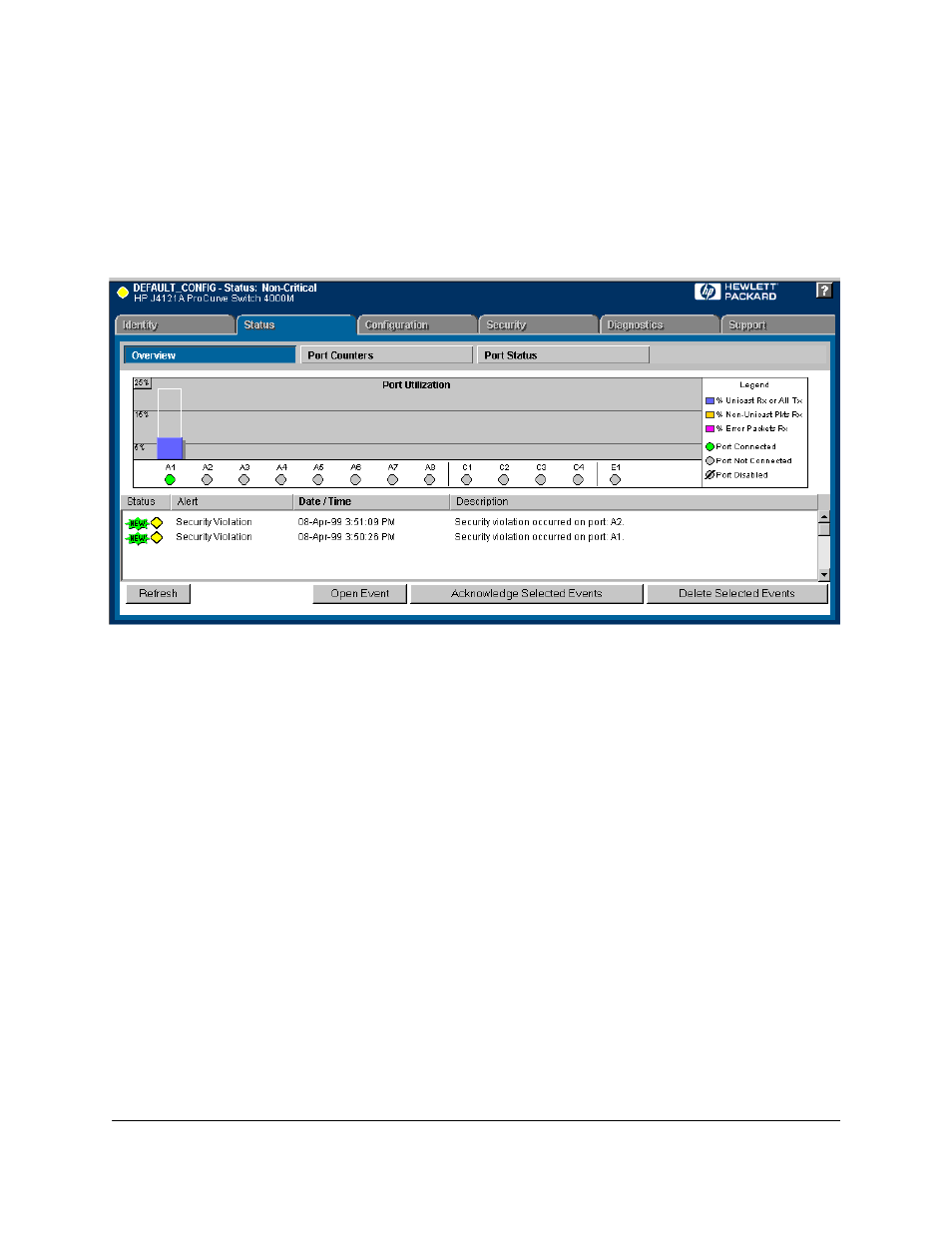
The Alert Log displays a Security Violation entry, with the system date
and time, and the port on which the violation occurred
•
The Intrusion Log lists the port number, the MAC address of the
intruding device, and the system time and date when the intrusion
occurred.
Figure 14-10.Security Violation Entries in the Alert Log
In the following figure, ports A1 and A2 have detected intrusions for which
their intrusion flags have not been reset, as indicated by the Ports with
Intrusion Flag entry. You must reset the intrusion flags for these ports before
the log can indicate any new intrusions for them. Ports A3 and A5 are not
listed, indicating that their intrusion flags have already been reset. These two
ports are ready to log any new intrusions.
- Scripting Toolkit for Linux (68 pages)
- Scripting Toolkit for Windows 9.50 (62 pages)
- Scripting Toolkit for Windows 9.60 (62 pages)
- Storage Area Manager (13 pages)
- Core HP-UX (5 pages)
- Matrix Operating Environment Software (232 pages)
- Matrix Operating Environment Software (70 pages)
- Matrix Operating Environment Software (120 pages)
- Matrix Operating Environment Software (36 pages)
- Matrix Operating Environment Software (192 pages)
- Matrix Operating Environment Software (99 pages)
- Matrix Operating Environment Software (198 pages)
- Matrix Operating Environment Software (66 pages)
- Matrix Operating Environment Software (95 pages)
- Matrix Operating Environment Software (152 pages)
- Matrix Operating Environment Software (264 pages)
- Matrix Operating Environment Software (137 pages)
- Matrix Operating Environment Software (138 pages)
- Matrix Operating Environment Software (97 pages)
- Matrix Operating Environment Software (33 pages)
- Matrix Operating Environment Software (142 pages)
- Matrix Operating Environment Software (189 pages)
- Matrix Operating Environment Software (58 pages)
- Matrix Operating Environment Software (68 pages)
- Matrix Operating Environment Software (79 pages)
- Matrix Operating Environment Software (223 pages)
- Matrix Operating Environment Software (136 pages)
- Matrix Operating Environment Software (34 pages)
- Matrix Operating Environment Software (63 pages)
- Matrix Operating Environment Software (67 pages)
- Matrix Operating Environment Software (128 pages)
- Matrix Operating Environment Software (104 pages)
- Matrix Operating Environment Software (75 pages)
- Matrix Operating Environment Software (245 pages)
- Matrix Operating Environment Software (209 pages)
- Matrix Operating Environment Software (71 pages)
- Matrix Operating Environment Software (239 pages)
- Matrix Operating Environment Software (107 pages)
- Matrix Operating Environment Software (77 pages)
- Insight Management-Software (148 pages)
- Matrix Operating Environment Software (80 pages)
- Insight Management-Software (128 pages)
- Matrix Operating Environment Software (132 pages)
- Matrix Operating Environment Software (74 pages)
- Matrix Operating Environment Software (76 pages)
