HP Storage Mirroring V5 Software User Manual
Page 144
11
-
10
12.
Specify if you want to
Failover IP Address(es)
on the source to the target.
13.
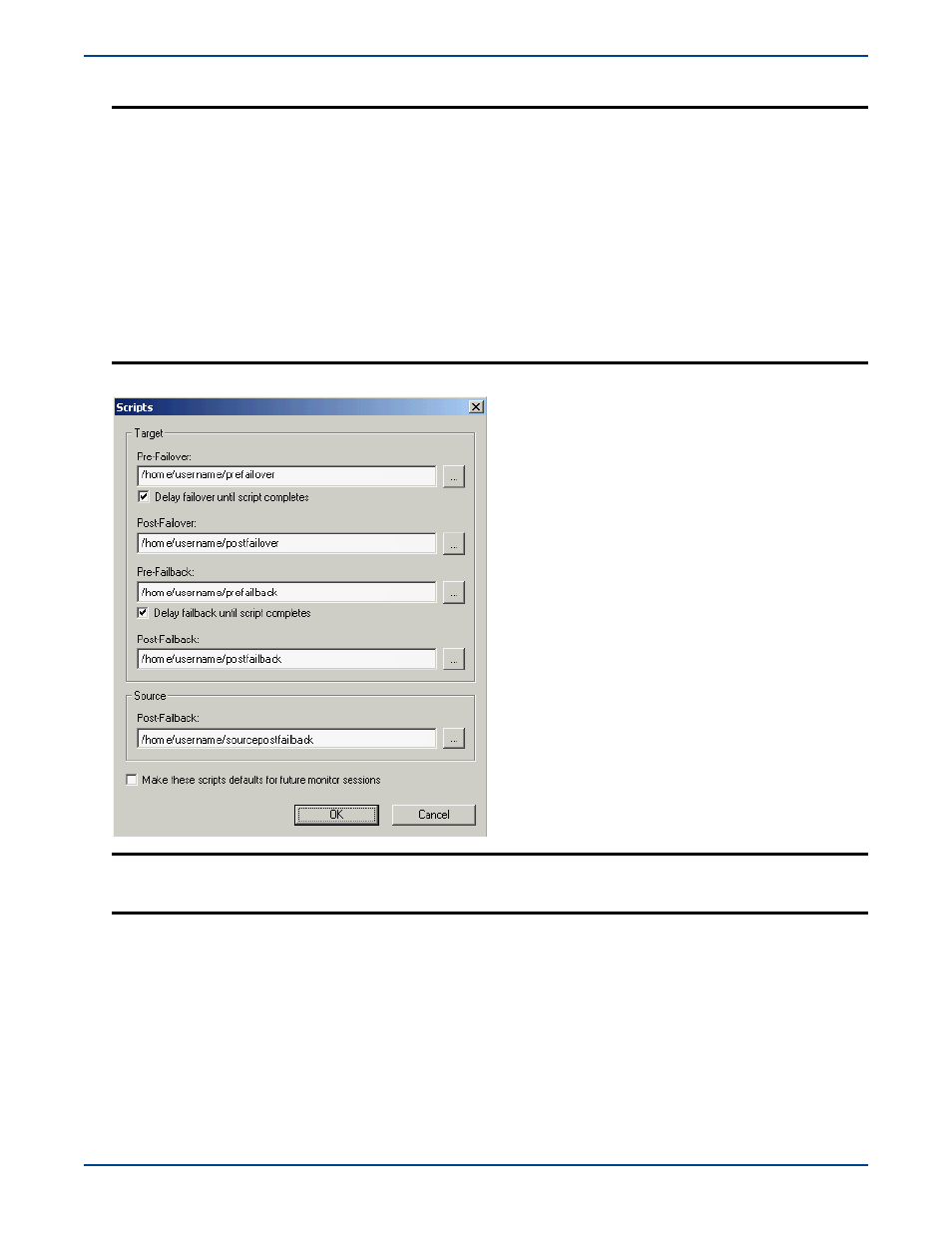
If you are using any scripts, click
Scripts
and enter the path and filename for each script type.
14.
If you want to delay the failover or failback processes until the associated script has completed, mark the appropriate
check box.
15.
If you want the same scripts to be used as the default for future monitor sessions, mark the appropriate check box.
16.
Click
OK
to return to the Monitor Settings dialog box and click
OK
again to save your monitor settings and begin
monitoring for a failure.
NOTE:
When multiple IP addresses are monitored, there is the potential for IP address conflicts during failover.
Conflict may occur when the number of IP addresses that trigger failover is less than the number of IP
addresses that are assumed by the target during failover.
For example, suppose a source machine has three IP addresses and two of these are monitored. If a failover
occurs due to a machine failure, there is not an address conflict because all of the IP addresses have failed
and no longer exist. If the failure only occurs on one of the monitored addresses, the other two IP
addresses (monitored and unmonitored) are still affected. The
Items to Failover
option forces these
addresses to be assumed by the target as well. These addresses then exist on both the source and the
target. This occurs because the
Items to Failover
option allows the selected (monitored) IP addresses or
all of the machine addresses to be failed over, but it does not allow the individual failed IP address to be
failed over. Therefore, when a source machine has fewer IP addresses that trigger failover than IP
addresses that will be assumed, there is a risk of an IP address conflict.
The delay before the failover process begins can be used to determine the cause of the failover, thus
possibly avoiding IP address conflicts.
NOTE:
If you click
Browse
next to the
Source Post-Failback
script, the directory structure for the target machine
appears by default. From this point, you can access your network so that you can see the directory
structure for the source machine, and then select the file you want.
