Rules – RuggedCom RuggedRouter RX1100 User Manual
Page 124
14. Configuring The Firewall
Revision 1.14.3
124
RX1000/RX1100™
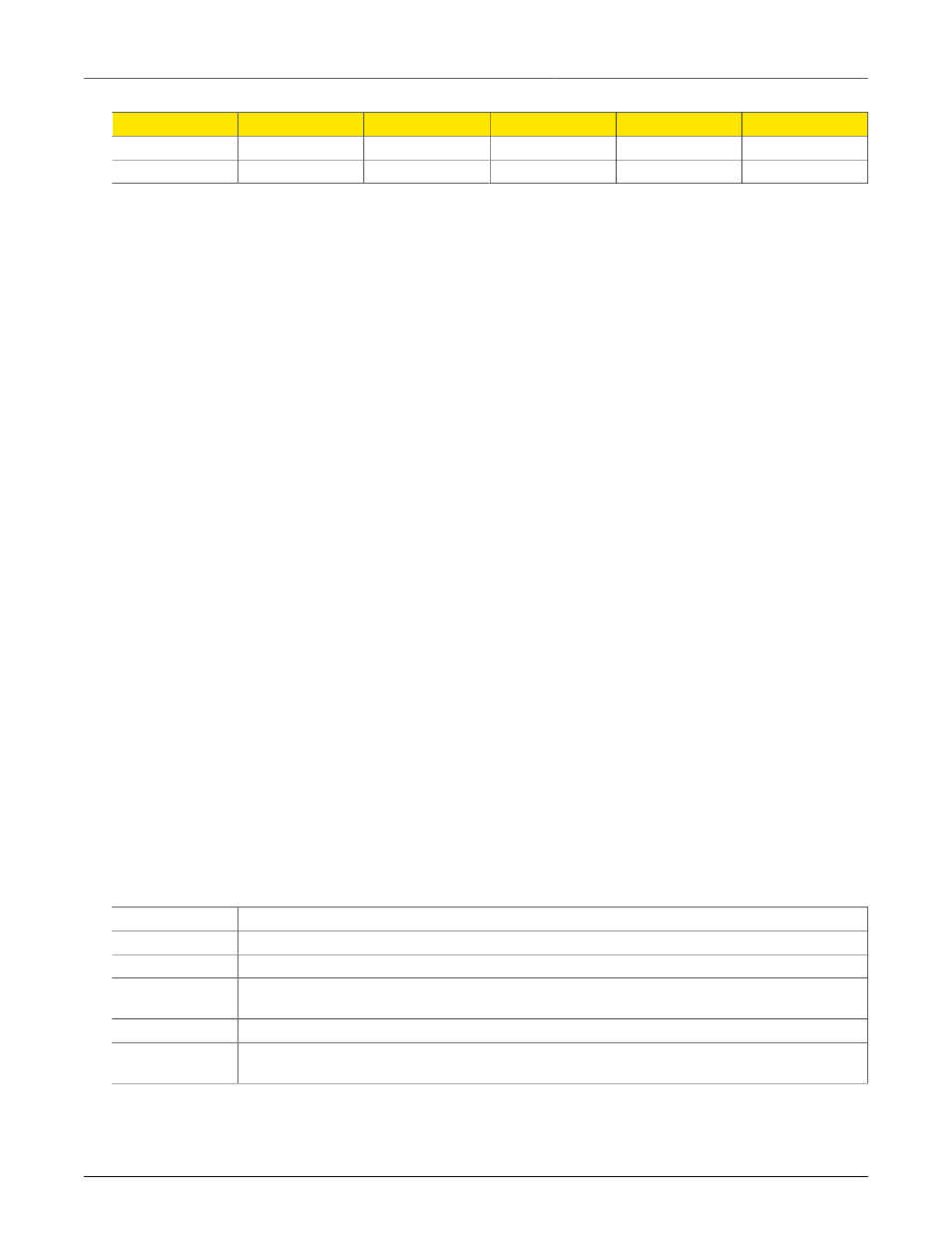
Rule
Interface
Subnet
Address
Protocol
Ports
4
w1ppp
eth1
100.1.101.16
5
w1ppp
eth1
100.1.101.16
tcp
smtp
1.
In this masquerading rule, port eth2 is connected to the local network and eth1 is connected
to a DSL modem. Traffic from the subnet handled by eth2 should be translated to whatever
IP is assigned to the modem. Internet clients will not be able to determine the router's public
address unless some form of dynamic dns is employed.
2.
In this SNAT rule a static address of 66.11.180.161 is acquired from the ISP. Traffic from the
subnet handled by eth2 should be translated to 66.11.180.161 as it sent to the Internet over
ppp. The + at the end of “ppp+” causes Shorewall to match any ppp interface.
3.
This example is much the same as the previous one only the subnet is explicitly described,
and could include traffic from any of the Ethernet ports.
4.
In this SNAT rule, traffic from the subnet handled by only port eth1 should be translated to
100.1.101.16 as it sent to the Internet on t1/e1 port w1ppp.
5.
This example is much the same as the previous one excepting that only smtp from eth1 will
be allowed.
Masquerading and SNAT rules are defined in the file /etc/shorewall/masq and are modified from the
Masquerading menu.
14.4.6. Rules
The default policies can completely configure traffic based upon zones. But the default policies cannot
take into account criteria such as the type of protocol, IP source/destination addresses and the need
to perform special actions such as port forwarding. The Shorewall rules can accomplish this.
The Shorewall rules provide exceptions to the default policies. In actuality, when a connection request
arrives the rules file is inspected first. If no match is found then the default policy is applied. Rules
are of the form:
Action Source-Zone Destination-Zone Protocol Destination-Port Source-Port Original-Destination-IP
Rate-Limit User-Group
Actions are ACCEPT, DROP, REJECT, DNAT, DNAT-, REDIRECT, REDIRECT-, CONTINUE, LOG
and QUEUE. The DNAT-, REDIRECT-, CONTINUE, LOG and QUEUE actions are not widely used
used and are not described here.
Action
Description
ACCEPT
Allow the connection request to proceed.
DROP
The connection request is simply ignored. No notification is made to the requesting client.
REJECT
The connection request is rejected with an RST (TCP) or an ICMP destination-unreachable packet
being returned to the client.
DNAT
Forward the request to another system (and optionally another port).
REDIRECT
Redirect the request to a local tcp port number on the local firewall. This is most often used to “remap”
port numbers for services on the firewall itself.
The remaining fields of a rule are as described below:
