Configuration of vpn clients, 2 configuration of vpn clients – Kerio Tech Firewall6 User Manual
Page 316
Chapter 23
Kerio VPN
316
23.2 Configuration of VPN clients
The following conditions must be met to enable connection of remote clients to local networks
via encrypted channels:
•
The Kerio VPN Client must be installed at remote clients (for detailed description, refer
to a stand-alone document, Kerio VPN Client — User Guide).
•
Users whose accounts are used for authentication to Kerio VPN Client must possess
rights enabling them connect to the VPN server in WinRoute (see chapter
•
Connection to the VPN server from the Internet as well as communication between
VPN clients must be allowed by traffic rules.
Note: Remote VPN clients connecting toWinRoute are included toward the number of persons
using the license (see chapters
and
). Be aware of this fact when deciding on what license
type should be purchased (or whether an add-on for upgrade to a higher number of users for
the license should be bought).
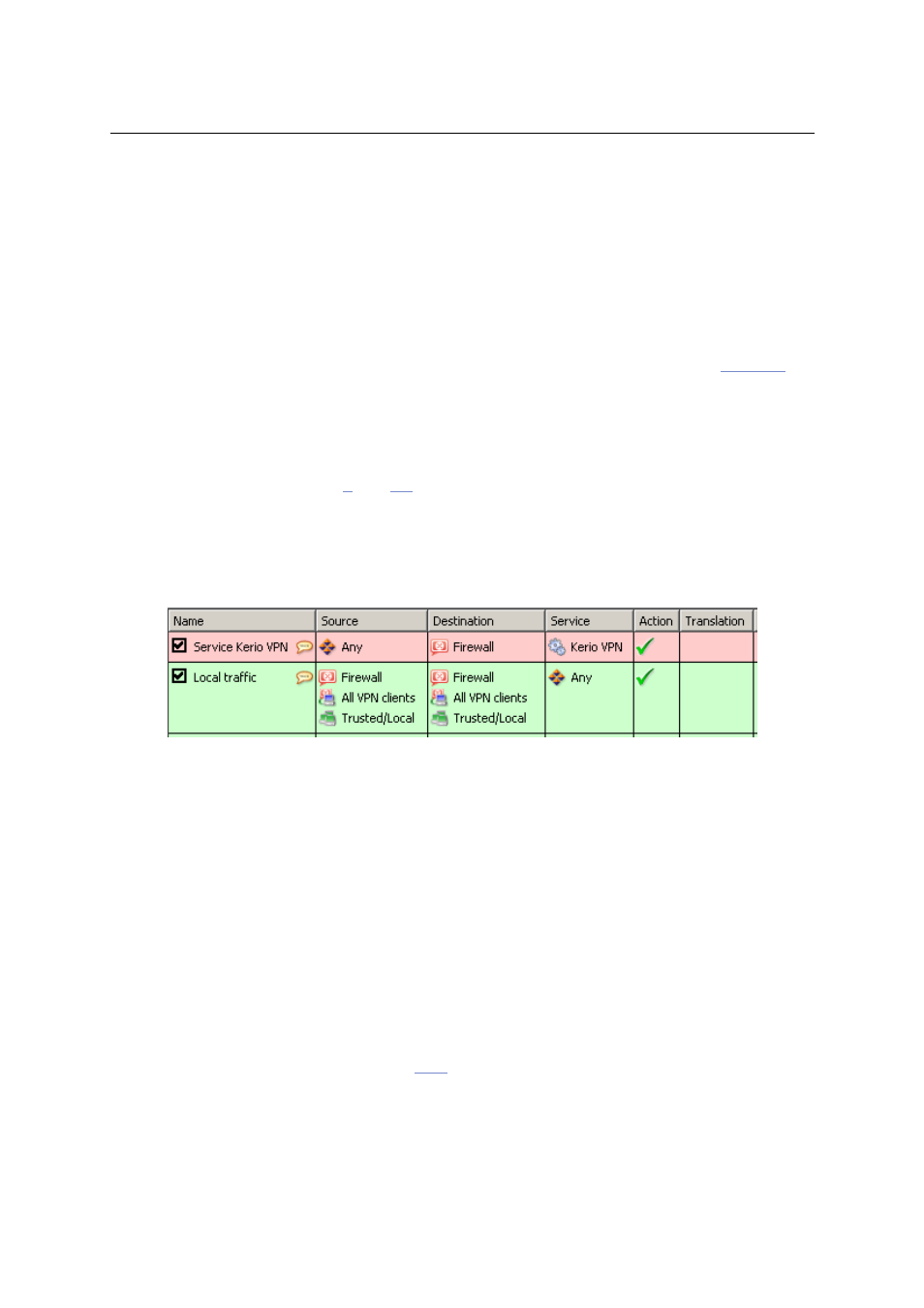
Basic configuration of traffic rules for VPN clients
Figure 23.6
Common traffic rules for VPN clients
•
The first rule allows connection to the VPN server in WinRoute from the Internet.
To restrict the number of IP addresses from which connection to the VPN server will
be allowed, edit the Source entry.
By default, the Kerio VPN service is defined for TCP and UDP protocols, port 4090. If
the VPN server is running at another port, this service must be redefined.
•
The second rule allows communication between the firewall, local network and VPN
clients.
If the rules are set like this, all VPN clients can access local networks and vice versa (all local
hosts can communicate with all VPN clients). To restrict the type of network access available
to VPN clients, special rules must be defined. A few alternatives of the restrictions settings
within Kerio VPN are focused in chapter
Note:
1.
If the Network Rules Wizard is used to create traffic rules, the described rules can be gen-
erated automatically (including matching of VPN clients with the Source and Destination
