20. security – ICP DAS USA MSM-6226 User Manual
Page 153
Publication date: Sep, 2009
Revision A8
141
3-20. Security
Function name:
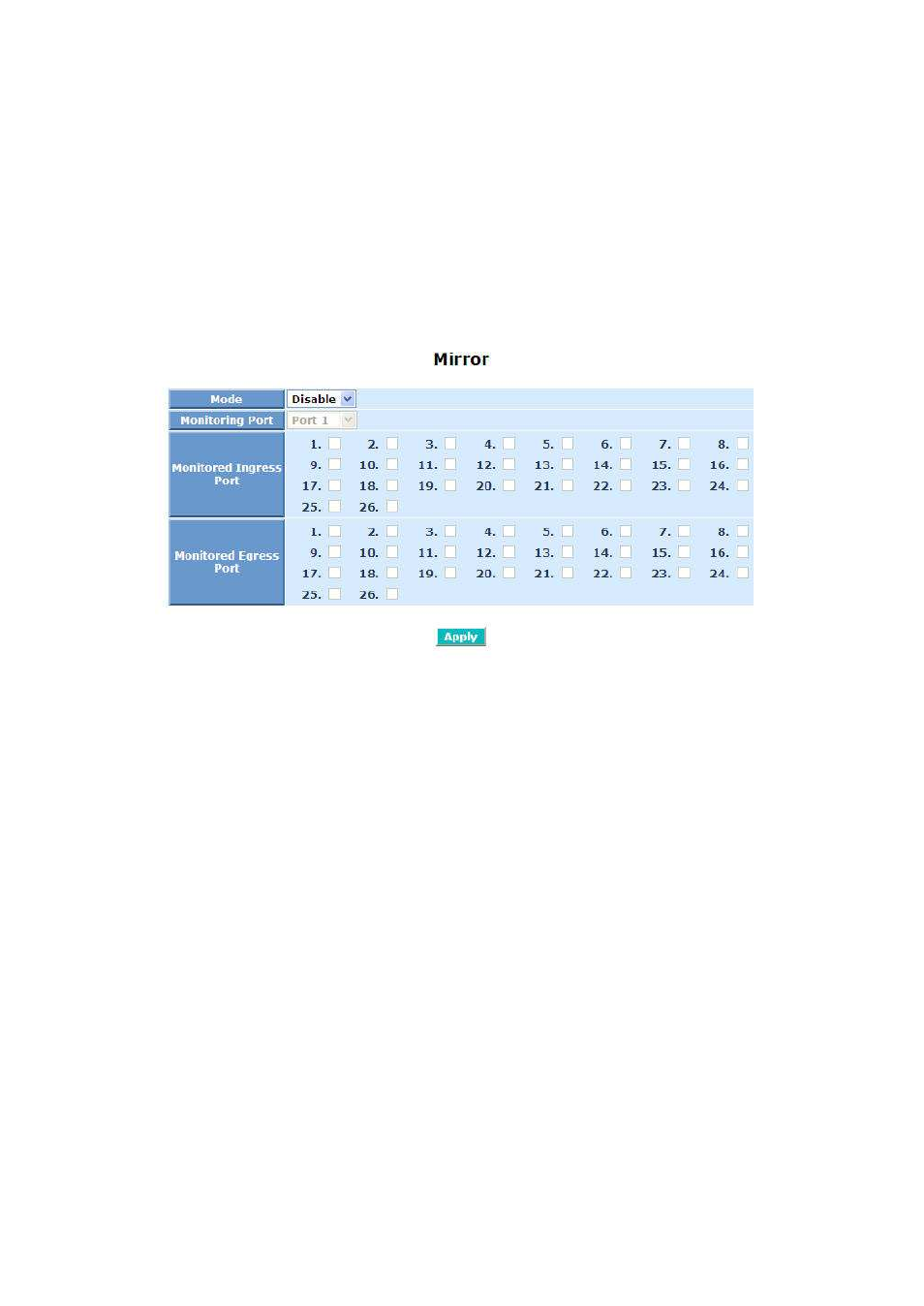
Mirror Configuration
Function description:
Mirror Configuration is to monitor the traffic of the network. For example, we
assume that Port A and Port B are Monitoring Port and Monitored Port
respectively, thus, the traffic received by Port B will be copied to Port A for
monitoring.
Fig. 3-64
Parameter description:
Mode:
Used for the activation or de-activation of Port Mirror function. Default is
disable.
Monitoring Port:
Set up the port for monitoring. Valid port is Port 1~26 and default is
Port 1.
Monitored Ingress Port:
Set up the port for being monitored. It only monitor the packets received
by the port you set up. Just tick the check box
(
)
beside the port x and
valid port is Port 1~26.
Monitored Egress Port:
Set up the port for being monitored. It only monitor the packets
transmitted by the port you set up. Just tick the check box
(
)
beside
the port x and valid port is Port 1~26.
