Fortinet FortiGate 4000 User Manual
Page 50
50
Fortinet Inc.
Factory default configuration
Getting started
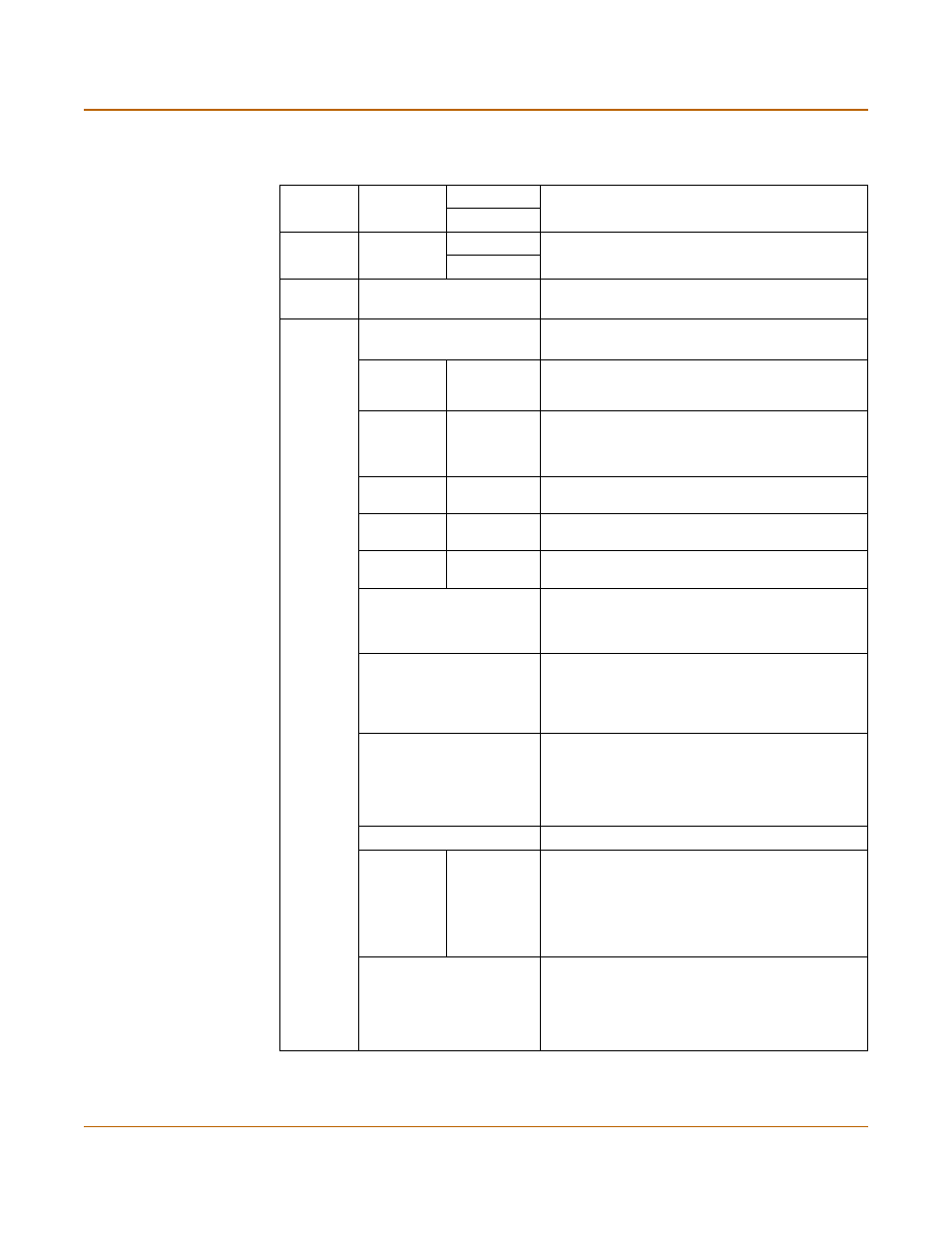
Table 14: Factory default firewall configuration
Internal
Address
Internal_All
IP: 0.0.0.0
Represents all of the IP addresses on the internal
network.
Mask: 0.0.0.0
External
Address
External_All
IP: 0.0.0.0
Represents all of the IP addresses on the external
network.
Mask: 0.0.0.0
Recurring
Schedule
Always
The schedule is valid at all times. This means that
the firewall policy is valid at all times.
Firewall
Policy
Internal->External
Firewall policy for connections from the internal
network to the external network.
Source
Internal_All
The policy source address. Internal_All means that
the policy accepts connections from any internal IP
address.
Destination External_All
The policy destination address. External_All means
that the policy accepts connections with a
destination address to any IP address on the
external network.
Schedule
Always
The policy schedule. Always means that the policy
is valid at any time.
Service
ANY
The policy service. ANY means that this policy
processes connections for all services.
Action
ACCEPT
The policy action. ACCEPT means that the policy
allows connections.
;
NAT
NAT is selected for the NAT/Route mode default
policy so that the policy applies network address
translation to the traffic processed by the policy.
NAT is not available for Transparent mode policies.
Traffic Shaping
Traffic shaping is not selected. The policy does not
apply traffic shaping to the traffic controlled by the
policy. You can select this option to control the
maximum or minimum amount of bandwidth
available to traffic processed by the policy.
Authentication
Authentication is not selected. Users do not have to
authenticate with the firewall before connecting to
their destination address. You can configure user
groups and select this option to require users to
authenticate with the firewall before they can
connect through the firewall.
;
Antivirus & Web Filter
Antivirus & Web Filter is selected.
Content
Profile
Scan
The scan content profile is selected. The policy
scans all HTTP, FTP, SMTP, POP3, and IMAP
traffic for viruses. See
for more information about the scan
content profile. You can select one of the other
content profiles to apply different levels of content
protection to traffic processed by this policy.
Log Traffic
Log Traffic is not selected. This policy does not
record messages to the traffic log for the traffic
processed by this policy. You can configure
FortiGate logging and select Log Traffic to record all
connections through the firewall that are accepted
by this policy.
