8 click the encryption tab, 9 do one of the following, Table 2 ipsec authentication parameters – Enterasys Networks Network Card User Manual
Page 58
46
RiverMaster Administrator’s Guide
Tunnel Protocols
Chapter 3
Configuring an ANG-3000/7000
8
Click the Encryption tab.
9
Do one of the following:
–
To set IPSec encryption parameters, choose IPSec from the
Protocol menu. IPSec encryption parameters are shown in
Figure 25. Select the IPSec Encryption Algorithm that determines
how IPSec packets exchanged between the ANG and Aurorean
Client remote users are encrypted.
–
To set PPTP encryption parameters, choose PPTP from the
Protocol menu. PPTP encryption parameters are shown in
Figure 25. Select the Microsoft Point-to-Point Encryption (MPPE)
algorithm that determines how PPTP packets exchanged between
the ANG and Aurorean remote users are encrypted.
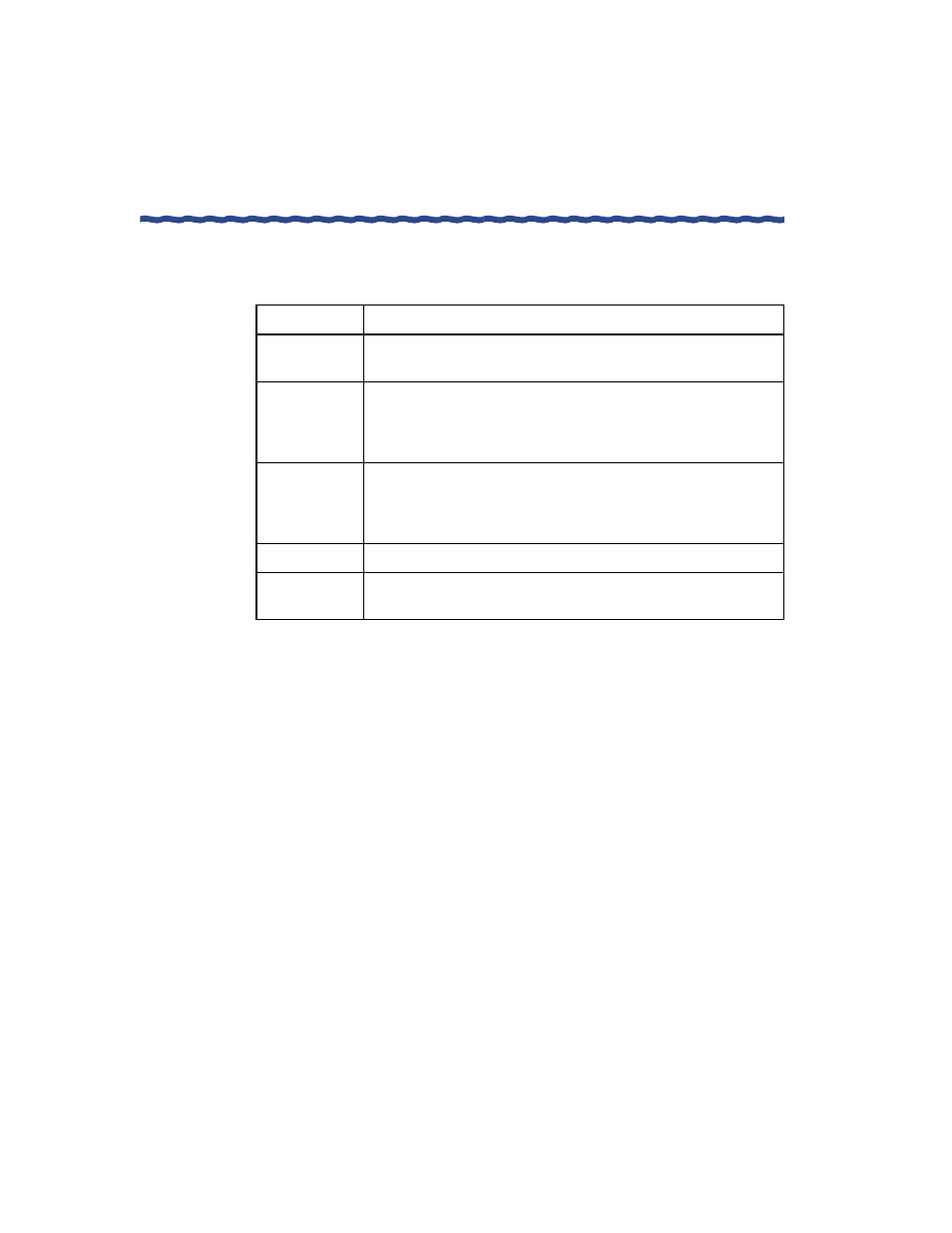
Table 2 IPSec Authentication Parameters
Parameter
Explanation
None
Disables the Signature Algorithm for IPSec packets; individual
packets are no longer signed and verified during transmission.
HMAC-SHA
Enables hashing message authentication codes (HMAC) that are
generated using the SHA cryptographic hashing function. HMAC-
SHA is generally regarded as stronger, more secure
cryptographic function than HMAC-MD5.
HMAC-MD5
Enables hashing message authentication codes (HMAC) that are
generated using the Rivest MD5 message digest algorithm
hashing function. While not as strong cryptographically as
HMAC-SHA, HMAC-MD5 provides better performance.
Time Period
Interval after which a new key is generated.
Data
Transferred
Lifetime volume (in kilobytes) of the key after which a new key is
generated.
