2 click on the authentication tab, 3 do one of the following – Enterasys Networks Network Card User Manual
Page 235
RiverMaster Administrator’s Guide
223
Appendix B
Configuring Tunnel Protocols
ANG-3000/7000 Preconfiguration Stored on a Floppy Disk
2
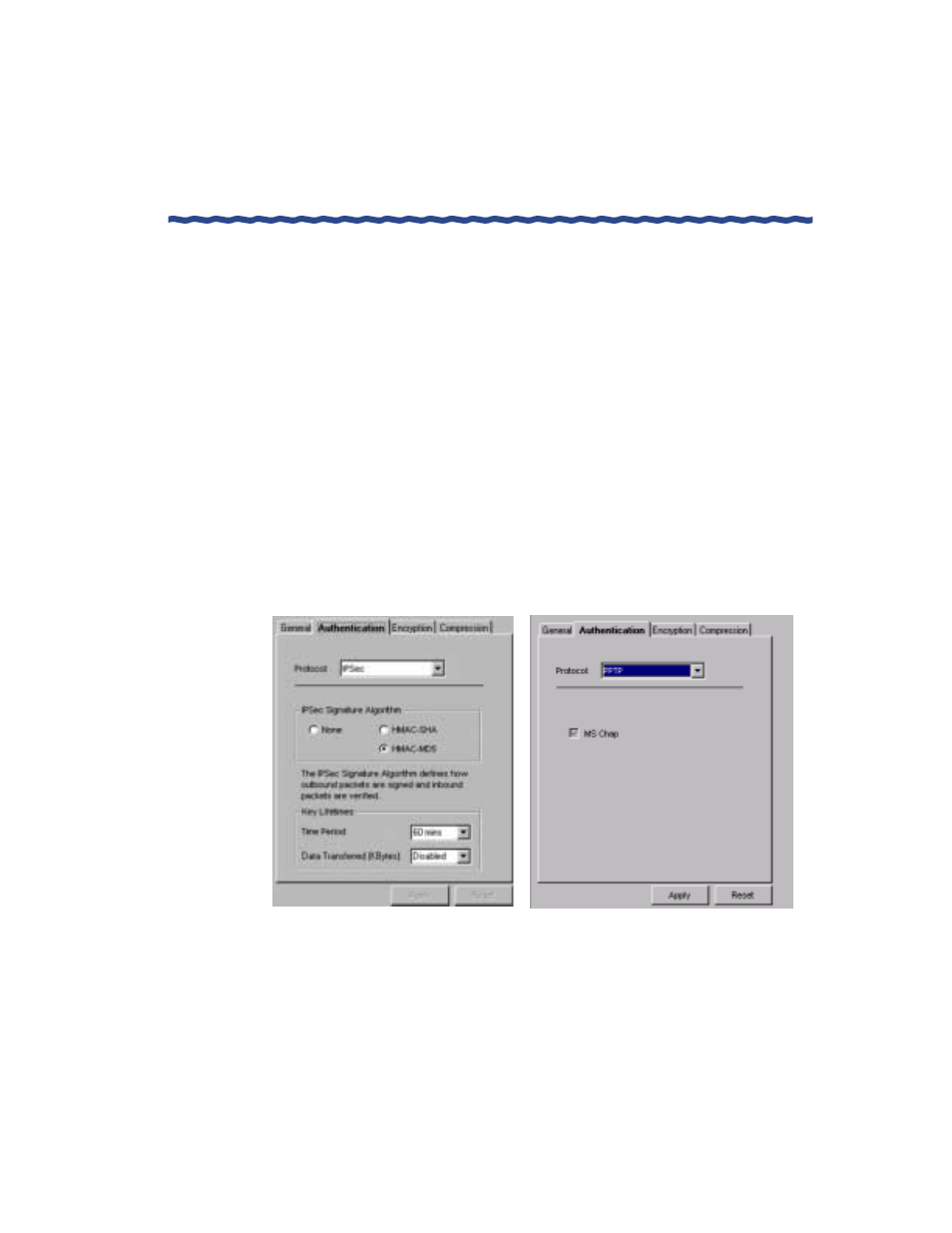
Click on the Authentication tab.
Figure 124 shows the authentication parameters available for each
tunnel protocol.
3
Do one of the following:
–
Choose IPSec from the Protocol pull down menu.
- Use the information in Table 18 to select the IPSec Signature
Algorithm that determines how IPSec packets exchanged
between the ANG and Aurorean users are signed and
verified.
- Use Table 18 to select the Time Period and Data Transferred
values which set how long the key lifetime should last in
terms of time elapsed or kilobytes amassed.
- Click Apply.
–
For PPTP, no additional work is required. Unlike IPSec, PPTP
does not authenticate individual packets; instead, PPTP relies on
user authentication using MS-CHAP. After the remote user is
authenticated, all PPTP packets are allowed access.
Figure 124 Tunnel Protocol Authentication Window
IPSec
PPTP
