Network requirements, Configuration procedure, Configuring source ip-based web login control – H3C Technologies H3C SecPath F1000-E User Manual
Page 102
94
Source IP-based SNMP login control configuration example
Network requirements
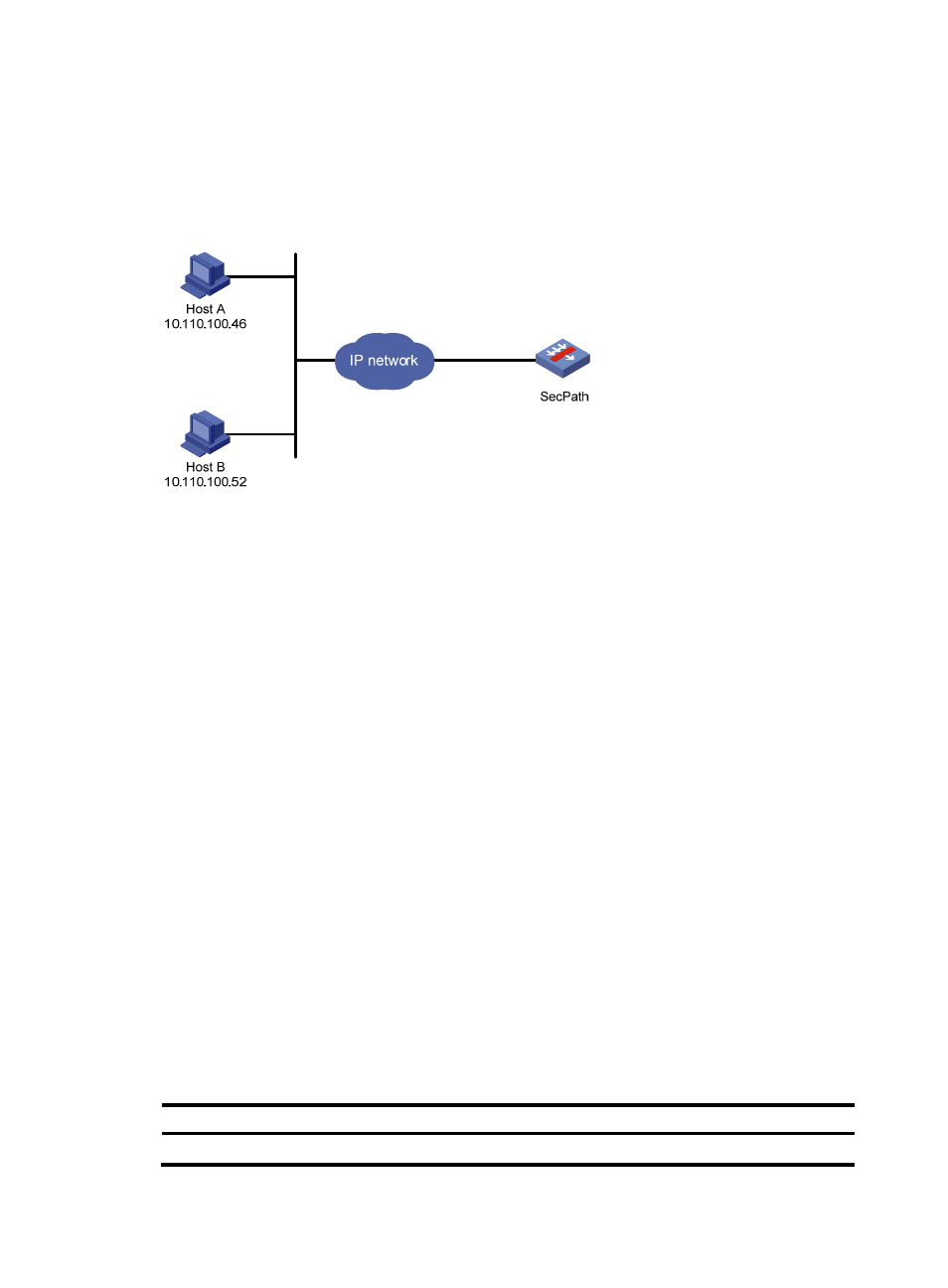
As shown in
, configure SecPath to allow only NMS users from Host A and Host B to access.
Figure 58 Network diagram
Configuration procedure
# Create ACL 2000, and configure rule 1 to permit packets sourced from Host B, and rule 2 to permit
packets sourced from Host A.
[Sysname] acl number 2000 match-order config
[Sysname-acl-basic-2000] rule 1 permit source 10.110.100.52 0
[Sysname-acl-basic-2000] rule 2 permit source 10.110.100.46 0
[Sysname-acl-basic-2000] quit
# Associate the ACL with the SNMP community and the SNMP group.
[Sysname] snmp-agent community read aaa acl 2000
[Sysname] snmp-agent group v2c groupa acl 2000
[Sysname] snmp-agent usm-user v2c usera groupa acl 2000
Configuring source IP-based Web login control
You can log in to the Web management page of the device through HTTP/HTTPS to remotely manage
the devices. By using the ACL, you can control Web user access to the device.
Before configuration, determine the permitted or denied source IP addresses.
Configuring source IP-based Web login control
Basic ACLs match the source IP addresses of packets, so you can use basic ACLs to implement source
IP-based login control over Web users. Basic ACLs are numbered from 2000 to 2999. For more
information about ACL, see Access Control Configuration Guide.
To configure source IP-based Web login control:
Step Command
Remarks
1.
Enter system view.
system-view
N/A
- H3C SecPath F5000-A5 Firewall H3C SecPath F1000-A-EI H3C SecPath F1000-E-SI H3C SecPath F1000-S-AI H3C SecPath F5000-S Firewall H3C SecPath F5000-C Firewall H3C SecPath F100-C-SI H3C SecPath F1000-C-SI H3C SecPath F100-A-SI H3C SecBlade FW Cards H3C SecBlade FW Enhanced Cards H3C SecPath U200-A U200-M U200-S H3C SecPath U200-CA U200-CM U200-CS
