Configuring ike, Overview, Ike negotiation process – H3C Technologies H3C S12500-X Series Switches User Manual
Page 163
151
8B
Configuring IKE
Unless otherwise specified, the term "IKE" in this chapter refers to IKEv1.
99B
Overview
Built on a framework defined by ISAKMP, Internet Key Exchange (IKE) provides automatic key negotiation
and SA establishment services for IPsec, dramatically simplifying the configuration and maintenance of
IPsec.
IKE provides the following benefits for IPsec:
•
Automatically negotiates IPsec parameters.
•
Performs DH exchanges to calculate shared keys, making sure each SA has a key that is
independent of other keys.
•
Automatically negotiates SAs when the sequence number in the AH or ESP header overflows,
making sure IPsec can provide the anti-replay service by using the sequence number.
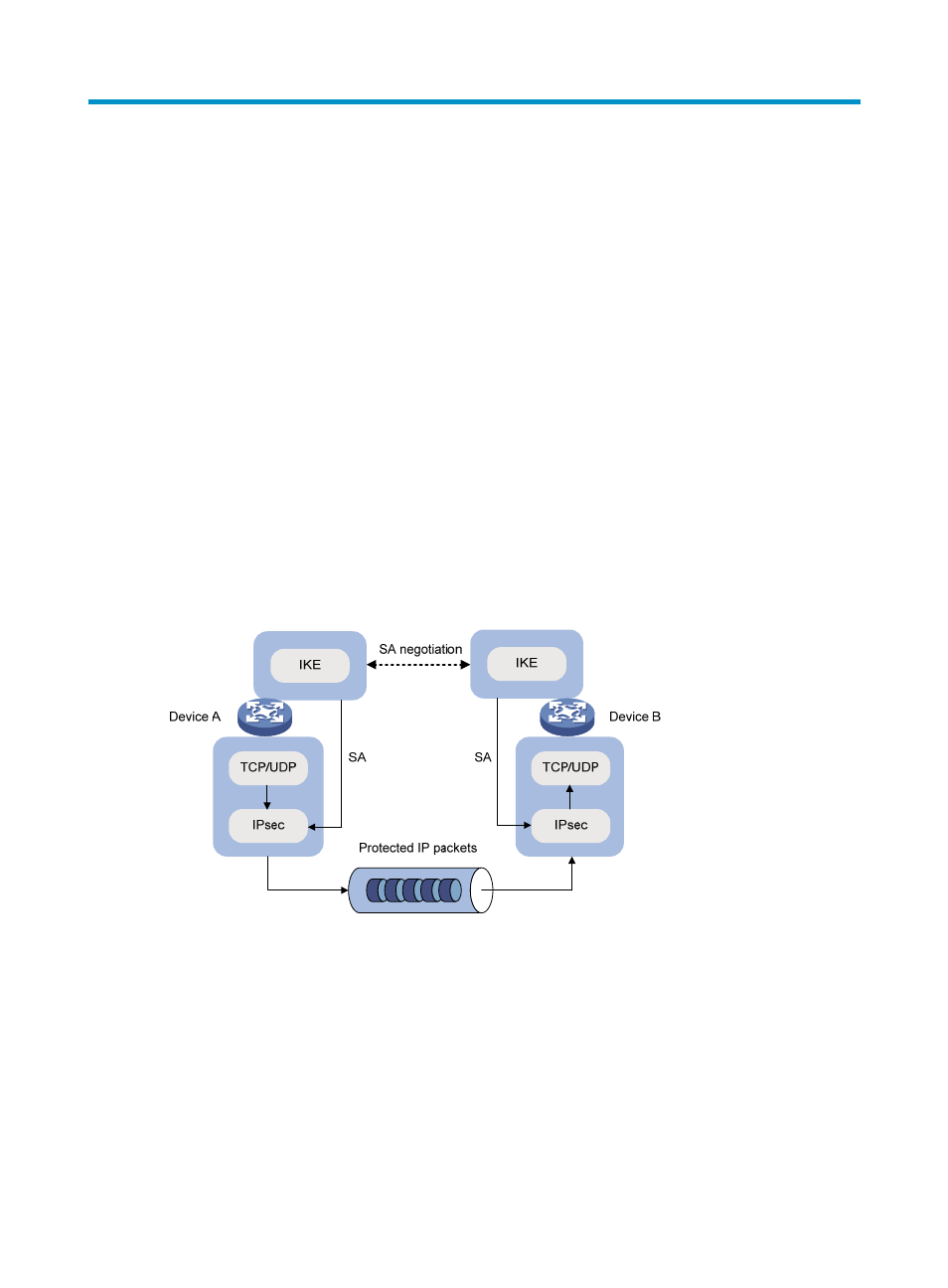
As shown in
858H
Figure 45
, IKE negotiates SAs for IPsec and transfers the SAs to IPsec, and IPsec uses the SAs
to protect IP packets.
Figure 45 Relationship between IKE and IPsec
251B
IKE negotiation process
IKE negotiates keys and SAs for IPsec in two phases:
1.
Phase 1—The two peers establish an IKE SA, a secure, authenticated channel for communication.
In this phase, two modes are available: main mode and aggressive mode.
2.
Phase 2—Using the IKE SA established in phase 1, the two peers negotiate to establish IPsec SAs.
- H3C S5560 Series Switches H3C WX6000 Series Access Controllers H3C WX5000 Series Access Controllers H3C WX3000 Series Unified Switches H3C LSWM1WCM10 Access Controller Module H3C LSWM1WCM20 Access Controller Module H3C LSQM1WCMB0 Access Controller Module H3C LSRM1WCM2A1 Access Controller Module H3C LSBM1WCM2A0 Access Controller Module H3C S9800 Series Switches H3C S5130 Series Switches H3C S5120 Series Switches
