Userloginwithoui configuration example – H3C Technologies H3C S12500-X Series Switches User Manual
Page 112
100
#
Execute the display port-security interface command after the number of MAC addresses learned by the
port reaches 64. You can see that the port security mode has changed to secure.
When any frame with a new MAC address arrives, intrusion protection is triggered and you see the port
has been disabled. The port should be re-enabled 30 seconds later.
After the port is re-enabled, delete several secure MAC addresses. You can see that the port security
mode of the port changes to autoLearn, and the port can learn MAC addresses again.
210B
userLoginWithOUI configuration example
431B
Network requirements
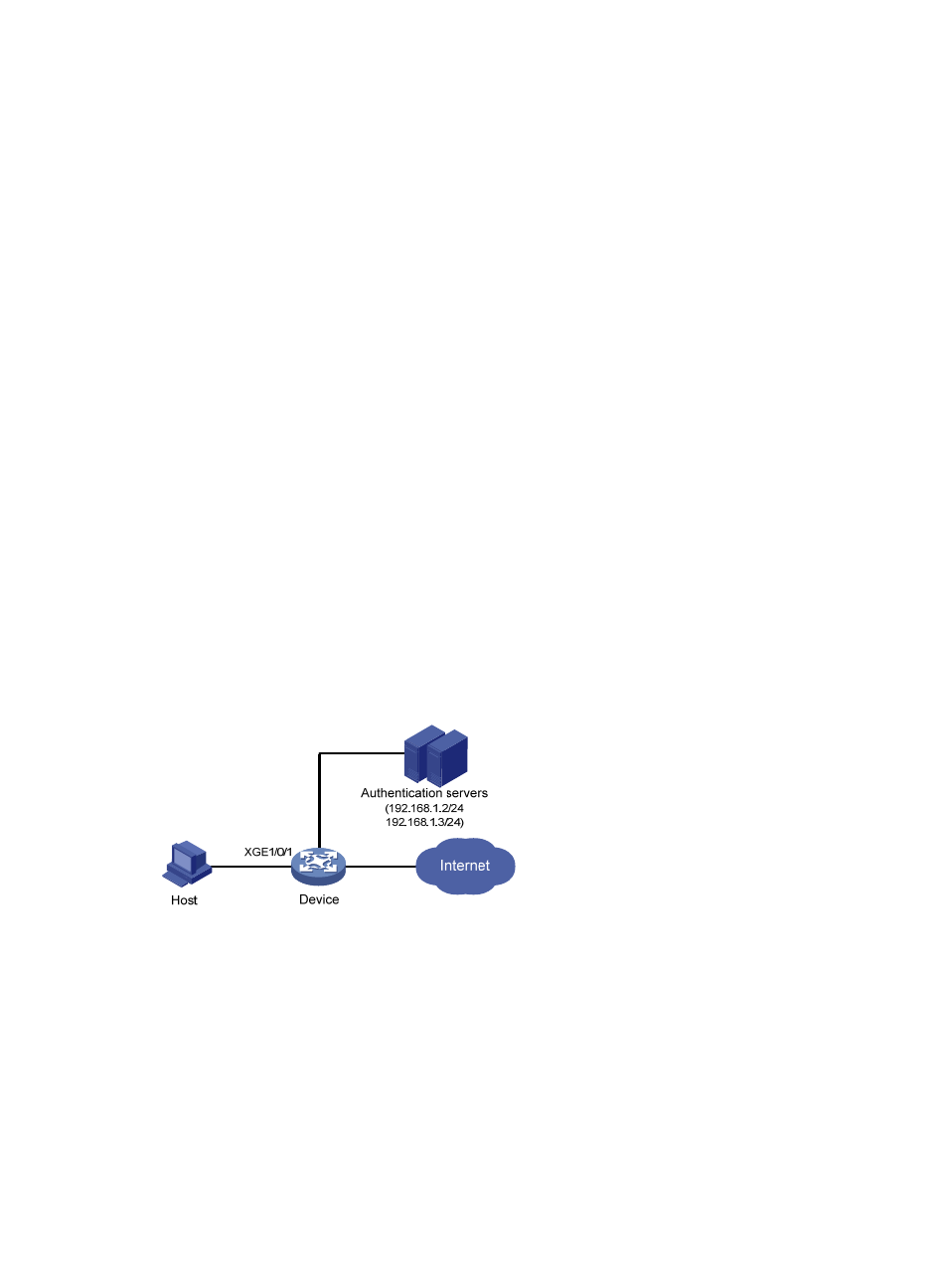
As shown in
811H
Figure 35
, a client is connected to the device through port Ten-GigabitEthernet 1/0/1. The
device authenticates the client with a RADIUS server. If the authentication succeeds, the client is
authorized to access the Internet.
•
The RADIUS server at 192.168.1.2 functions as the primary authentication server and the secondary
accounting server, and the RADIUS server at 192.168.1.3 functions as the secondary authentication
server and the primary accounting server. The shared key for authentication is name, and that for
accounting is money.
•
All users use the authentication, authorization, and accounting methods of ISP domain sun.
•
The RADIUS server response timeout time is 5 seconds and the maximum number of RADIUS packet
retransmission attempts is 5. The Device sends real-time accounting packets to the RADIUS server at
15-minute intervals, and sends usernames without domain names to the RADIUS server.
Configure port Ten-GigabitEthernet 1/0/1 of the device to allow only one 802.1X user and a user that
uses one of the specified OUI values to be authenticated.
Figure 35 Network diagram
432B
Configuration procedure
The following configuration steps cover some AAA/RADIUS configuration commands. For more
information about the commands, see Security Command Reference.
Make sure the host and the RADIUS server can reach each other.
1.
Configure AAA:
# Configure a RADIUS scheme named radsun.
[Device] radius scheme radsun
[Device-radius-radsun] primary authentication 192.168.1.2
- H3C S5560 Series Switches H3C WX6000 Series Access Controllers H3C WX5000 Series Access Controllers H3C WX3000 Series Unified Switches H3C LSWM1WCM10 Access Controller Module H3C LSWM1WCM20 Access Controller Module H3C LSQM1WCMB0 Access Controller Module H3C LSRM1WCM2A1 Access Controller Module H3C LSBM1WCM2A0 Access Controller Module H3C S9800 Series Switches H3C S5130 Series Switches H3C S5120 Series Switches
