Brocade Fabric OS Encryption Administrator’s Guide Supporting RSA Data Protection Manager (DPM) Environments (Supporting Fabric OS v7.2.0) User Manual
Page 311
Fabric OS Encryption Administrator’s Guide (DPM)
291
53-1002922-01
Reclaiming the WWN base of a failed Brocade Encryption Switch
6
Type: DPM
Secondary Key Vault not configured
Additional Key Vault/Cluster Information:
Key Vault/CA Certificate Validity: Yes
Port for Key Vault Connection: 443
Time of Day on Key Server: N/A
Server SDK Version: N/A
Encryption Node (Key Vault Client) Information:
Node KAC Certificate Validity: Yes
Time of Day on the Switch: N/A
Client SDK Version: RKM-Client 3.1 27-Jan-2012
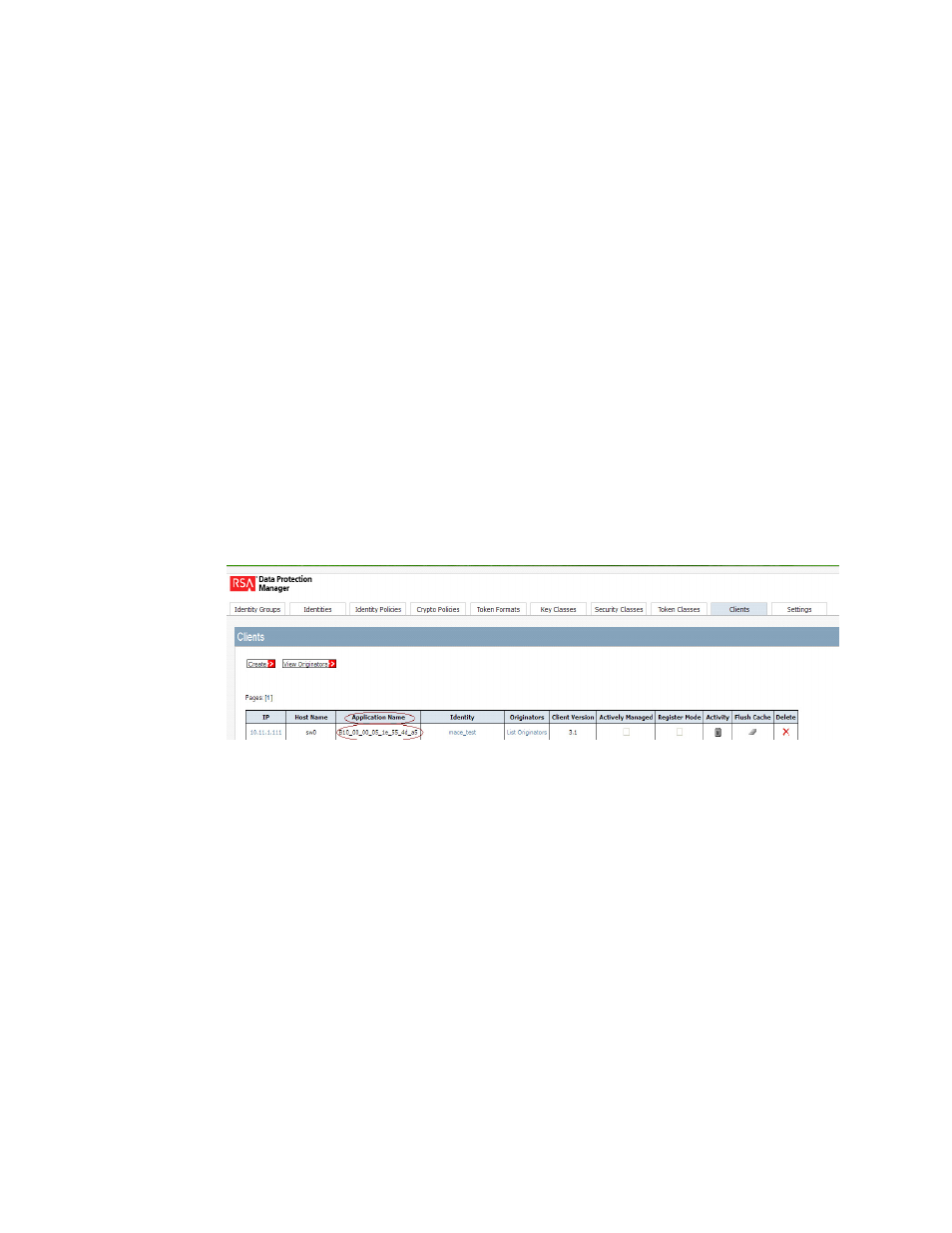
Client Username: B10_00_00_05_1e_55_4d_a5
Client Usergroup: N/A
Connection Timeout: 3 seconds
Response Timeout: 25 seconds
Connection Idle Timeout: N/A
Once identified, the client on the DPM Key Vault with the corresponding name should be deleted
when the DPM is deregistered on the Brocade Encryption Switch. Otherwise reregistration of the
DPM Key Vault will result in key vault connectivity failure on the Brocade Encryption Switch. (Refer
to
FIGURE 111
DPM Clients page
Reclaiming the WWN base of a failed Brocade Encryption Switch
When a Brocade Encryption Switch fails, to reclaim the WWN base, follow these steps:
1. Locate the Brocade Encryption Switch that has failed and deregister from the encryption
group.
Admin:switch> cryptocfg –-dereg –membernode
2. Reclaim the WWN base of the failed Brocade Encryption Switch.
Admin:switch> cryptocfg --reclaimWWN –membernode
3. Synchronize the crypto configurations across all member nodes.
Admin:switch> cryptocfg –-commit
