Event auditing, Inter-zone access log auditing, Configuration guide – H3C Technologies H3C SecCenter Firewall Manager User Manual
Page 62: Abnormal traffic log auditing
56
Report export task management functions
Event auditing
The event auditing function allows you to audit abnormal traffic logs, blacklist logs, operation logs, NAT
logs, inter-zone access control logs, MPLS logs, and other logs. It also supports exporting up to 10,000
entries of logs. If there are more than 10,000 log entries, only the first 10,000 entries will be exported.
The event auditing function does not support cross-day query. If the query period spans a day or the
query start time is later than the end time, the end time will automatically change to 23:59 of the same
day as the start time.
Inter-zone access log auditing
Configuration guide
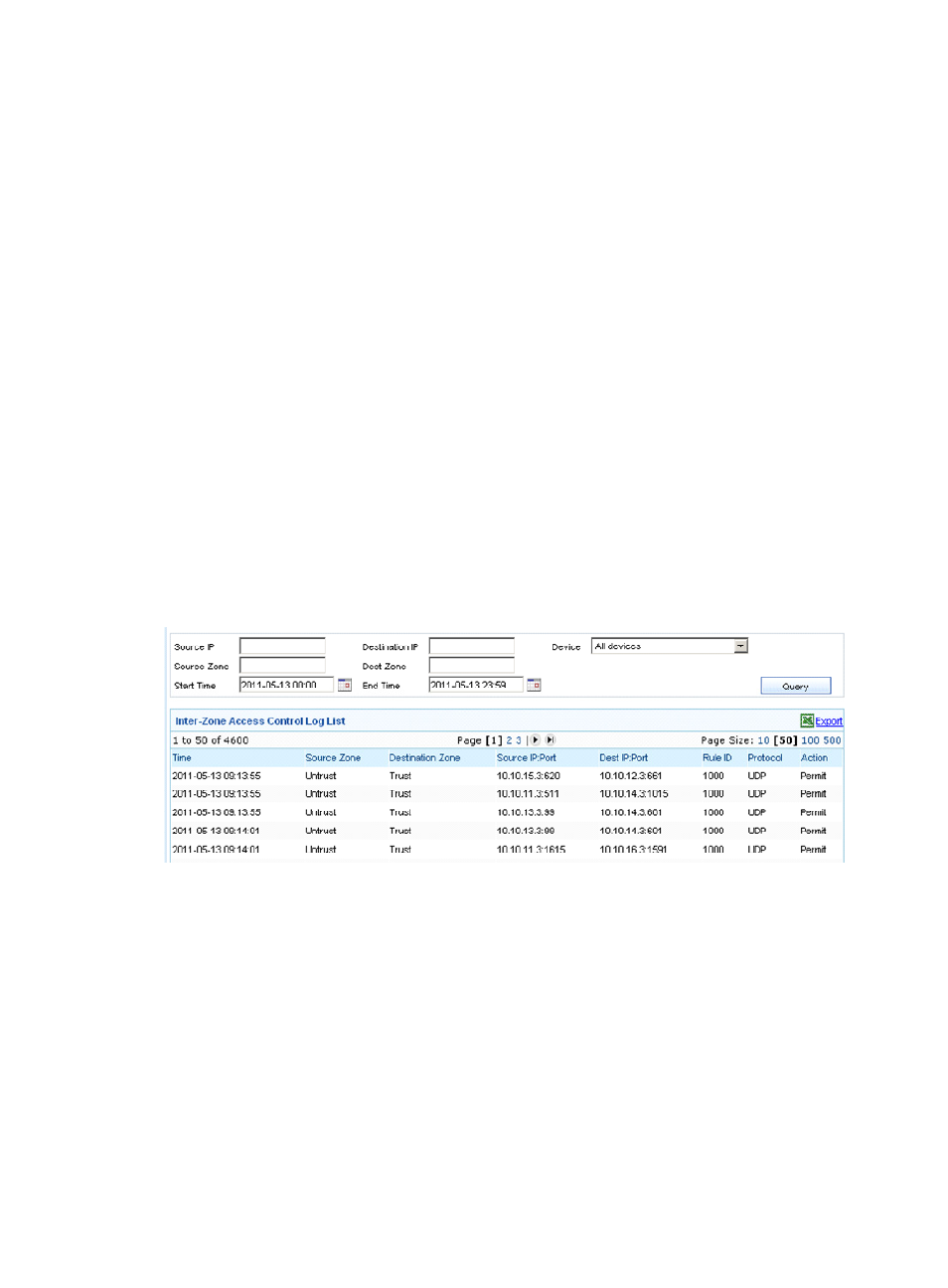
From the navigation tree of the firewall management component, select Inter-Zone Access Logs under
Event Auditing to enter the inter-zone access log auditing page, as shown in
.
A zone is a set consisting of one or more network segments. Inter-zone access logs are logs recorded by
the firewall device when network segments of security zones are attacked. Inter-zone access log auditing
is for analysis of such logs. Each log records the time when the attack occurred, the attack's source zone,
destination zone, source IP:port, destination IP:port, attack protection rule ID, protocol, and action taken
by the system, helping you know about the inter-zone access status of the network.
Figure 53 Inter-zone access log auditing
Abnormal traffic log auditing
Configuration guide
From the navigation tree of the firewall management component, select Abnormal Traffic Logs under
Event Auditing to enter the abnormal traffic log auditing page, as shown in
. This page lists the
logs in order of time, with the most recent log at the top. Each log records the time, source IP, and
destination IP of the abnormal traffic, reason for giving the alarm, severity, and ratio of each protocol
used by the abnormal traffic.
Abnormal traffic log auditing allows you to query abnormal traffic logs by source IP, destination IP,
reason, severity level, time, and device group, helping you analyze traffic for abnormal behaviors.
