Eap-message, Message-authenticator, Initiating 802.1x authentication – H3C Technologies H3C S6300 Series Switches User Manual
Page 80: 1x client as the initiator, Access device as the initiator
65
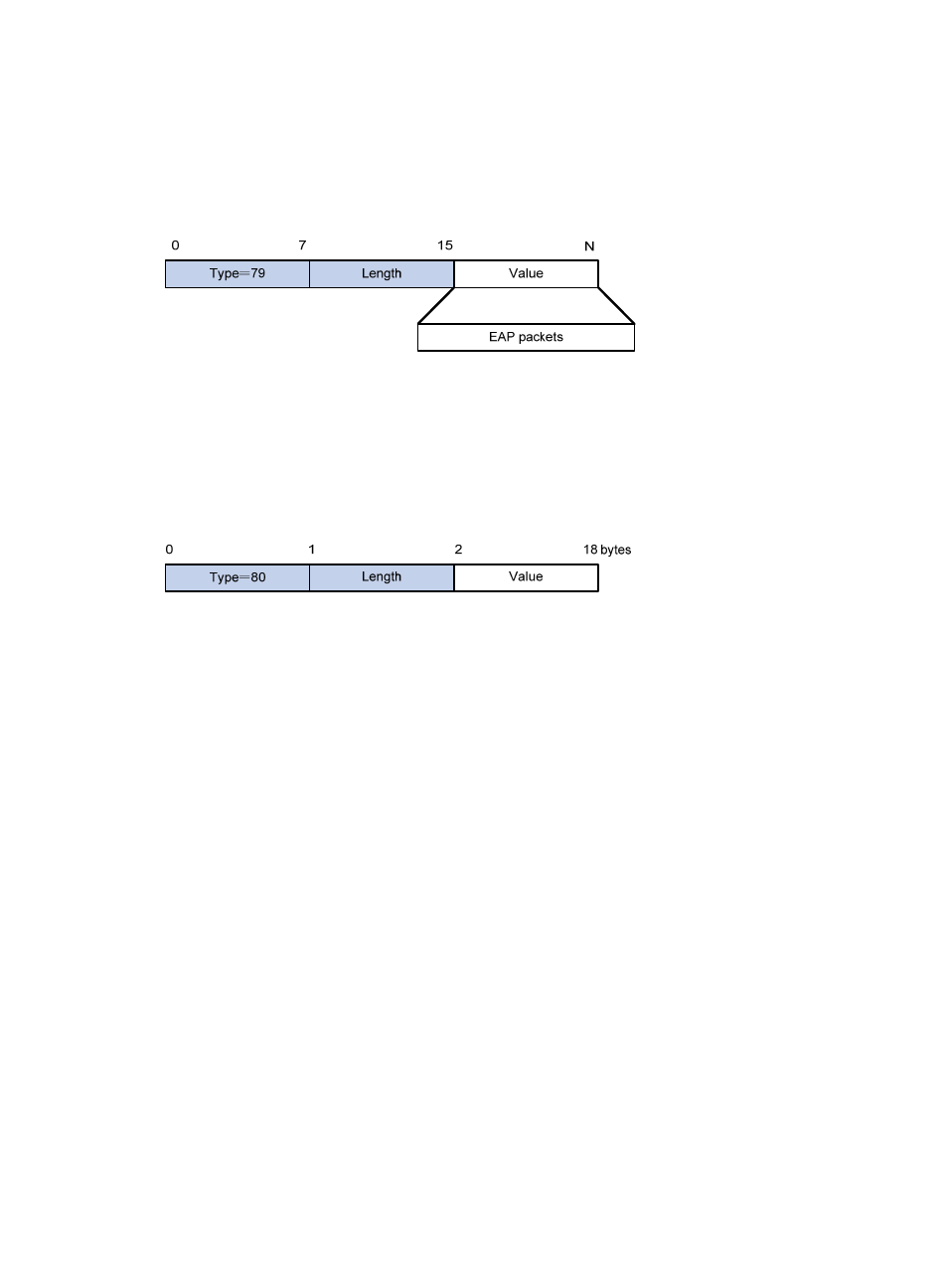
EAP-Message
RADIUS encapsulates EAP packets in the EAP-Message attribute, as shown in
. The Type field
takes 79, and the Value field can be up to 253 bytes. If an EAP packet is longer than 253 bytes, RADIUS
encapsulates it in multiple EAP-Message attributes.
Figure 24 EAP-Message attribute format
Message-Authenticator
RADIUS includes the Message-Authenticator attribute in all packets that have an EAP-Message attribute
to check their integrity. The packet receiver drops the packet if the calculated packet integrity checksum
is different from the Message-Authenticator attribute value. The Message-Authenticator prevents EAP
authentication packets from being tampered with during EAP authentication.
Figure 25 Message-Authenticator attribute format
Initiating 802.1X authentication
Both the 802.1X client and the access device can initiate 802.1X authentication.
802.1X client as the initiator
The client sends an EAPOL-Start packet to the access device to initiate 802.1X authentication. The
destination MAC address of the packet is the IEEE 802.1X specified multicast address
01-80-C2-00-00-03 or the broadcast MAC address. If any intermediate device between the client and
the authentication server does not support the multicast address, you must use an 802.1X client (for
example, the H3C iNode 802.1X client) that can send broadcast EAPOL-Start packets.
Access device as the initiator
The access device initiates authentication, if a client cannot send EAPOL-Start packets. One example is
the 802.1X client available with Windows XP.
The access device supports the following modes:
•
Multicast trigger mode—The access device multicasts Identity EAP-Request packets periodically
(every 30 seconds by default) to initiate 802.1X authentication.
•
Unicast trigger mode—Upon receiving a frame with the source MAC address not in the MAC
address table, the access device sends an Identity EAP-Request packet out of the receiving port to
the unknown MAC address. It retransmits the packet if no response has been received within a
certain time interval.
