Network requirements, Configuration procedure – H3C Technologies H3C S6300 Series Switches User Manual
Page 256
241
Configuring an IKE-based IPsec tunnel for IPv4 packets
Network requirements
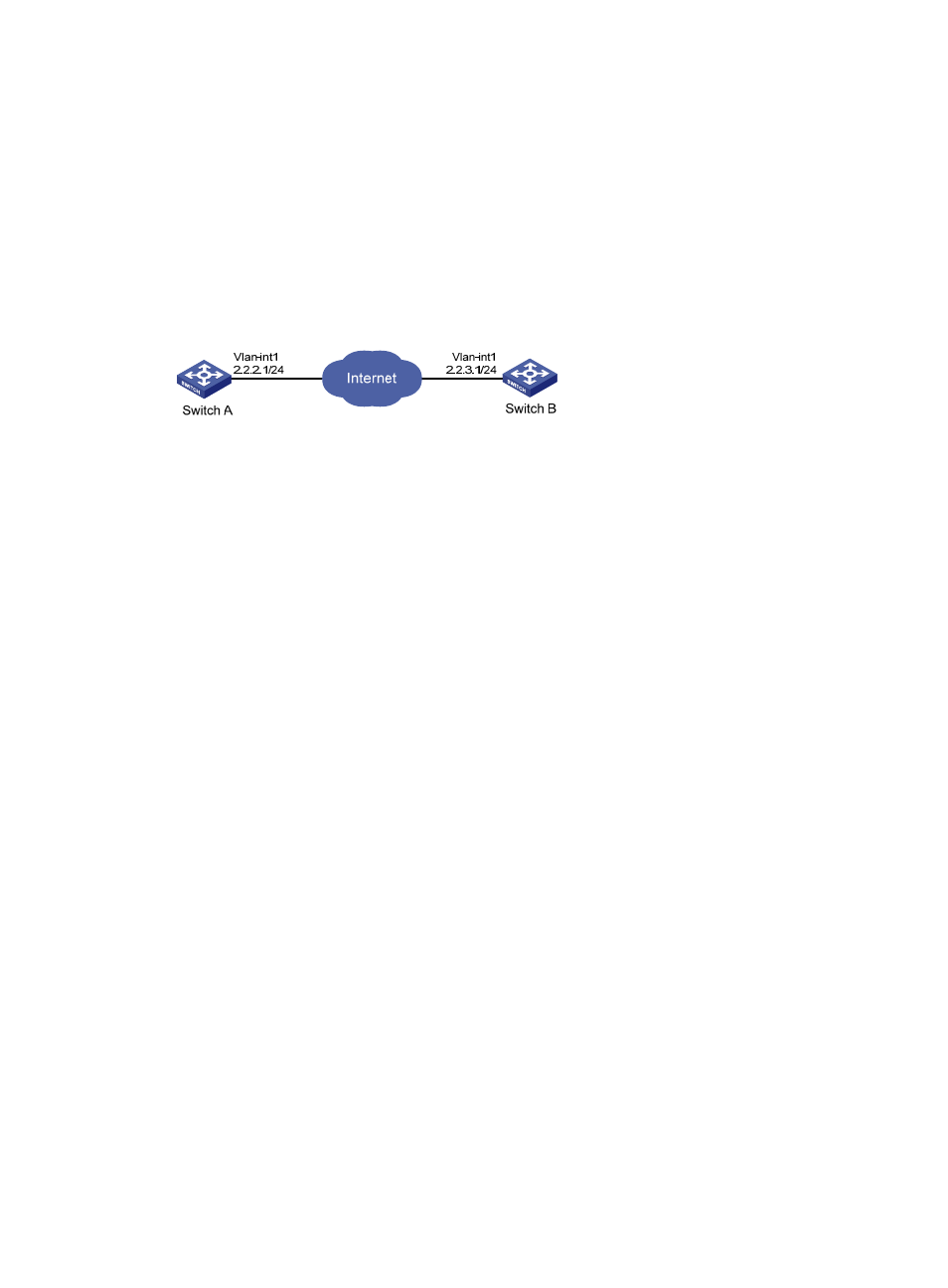
As shown in
, establish an IPsec tunnel between Switch A and Switch B to protect data flows
between the switches. Configure the IPsec tunnel as follows:
•
Specify the encapsulation mode as tunnel, the security protocol as ESP, the encryption algorithm as
AES-CBC-192, and the authentication algorithm as HMAC-SHA1.
•
Set up SAs through IKE negotiation.
Figure 78 Network diagram
Configuration procedure
1.
Configure Switch A:
# Configure an IP address for VLAN-interface 1.
[SwitchA] interface vlan-interface 1
[SwitchA-Vlan-interface1] ip address 2.2.2.1 255.255.255.0
[SwitchA-Vlan-interface1] quit
# Define an ACL to identify data flows from Switch A to Switch B.
[SwitchA] acl number 3101
[SwitchA-acl-adv-3101] rule 0 permit ip source 2.2.2.1 0 destination 2.2.3.1 0
[SwitchA-acl-adv-3101] quit
# Create an IPsec transform set named tran1.
[SwitchA] ipsec transform-set tran1
# Specify the encapsulation mode as tunnel.
[SwitchA-ipsec-transform-set-tran1] encapsulation-mode tunnel
# Specify the security protocol as ESP.
[SwitchA-ipsec-transform-set-tran1] protocol esp
# Specify the ESP encryption and authentication algorithms.
[SwitchA-ipsec-transform-set-tran1] esp encryption-algorithm aes-cbc-192
[SwitchA-ipsec-transform-set-tran1] esp authentication-algorithm sha1
[SwitchA-ipsec-transform-set-tran1] quit
# Create the IKE keychain named keychain1.
[SwitchA] ike keychain keychain1
# Configure the pre-shared key used with the peer 2.2.3.1 as plaintext string of
12345zxcvb!@#$%ZXCVB.
[SwitchA-ike-keychain-keychain1] pre-shared-key address 2.2.3.1 255.255.255.0 key
simple 12345zxcvb!@#$%ZXCVB
[SwitchA-ike-keychain-keychain1] quit
# Create the IKE profile named profile1.
[SwitchA] ike profile profile1
