Static wep settings – AMX MVP-5100 User Manual
Page 74
Protected Setup Pages
66
MVP-5100/5150 Modero Viewpoint Touch Panels
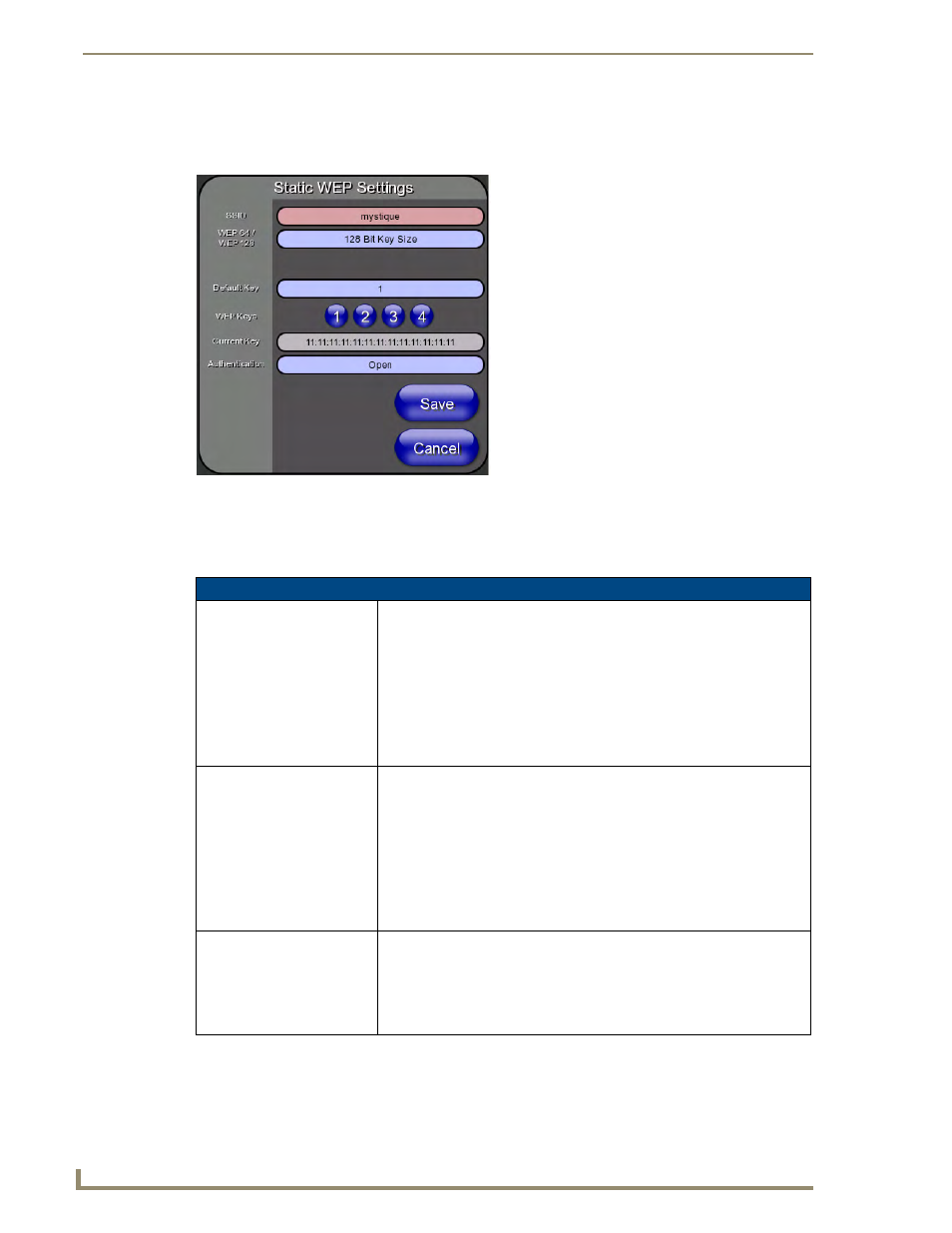
Static WEP Settings
Press the Static WEP button to open the Static WEP Settings page (FIG. 57).
Static WEP security requires that both a target WAP be identified and an encryption method be
implemented prior to establishing communication. In addition to providing both Open and Shared
Authentication capabilities, this page also supports Hexadecimal and ASCII keys.
FIG. 57
Wireless Settings page - Static WEP Settings
Static WEP Settings
SSID (Service Set Identifier):
Opens an on-screen keyboard to enter the SSID name used on the target
WAP. The SSID is a unique name used by the WAP, and is assigned to all
panels on that network. An SSID is required by the WAP before the panel is
permitted to join the network.
• The SSID is case sensitive and must not exceed 32 characters.
• Make sure this setting is the same for all points in your wireless network.
• NXA-WAP250Gs use AMX as their default SSID.
• If this field is left blank, the panel will attempt to connect to the first available
WAP.
WEP 64 / WEP 128:
Cycles through the available encryption options: 64 or 128 Bit Key Size.
“WEP” (Wired Equivalent Privacy) is an 802.11 security protocol designed to
provide wireless security equivalent to wired networks.
• WEP64 enables WEP encryption using a 64 Bit Key Size. All packets are
transmitted with their contents encrypted using the Default WEP Key.
• WEP128 enables WEP encryption using a 128 Bit Key Size. All packets are
transmitted with their contents encrypted using the Default WEP Key.
• If the key is not the correct size, the system will resize it to match the
number of bits required for the WEP encryption mode selected.
Default Key:
Cycles through the four available WEP key identifiers to select a WEP key to
use. As the Default Key value is altered (through selection) the corresponding
“Current Key” is displayed. Each Current Key corresponds to a WEP key.
This feature is useful for accessing different networks without having to
re-enter that networks’ WEP key. It is also sometimes used to set up a
rotating key schedule to provide an extra layer of security.
