Enter server login information, Using clustered exchange servers, Configure protection settings – HP Storage Mirroring V4.5 Software User Manual
Page 26: Enter server login information -4, Using clustered exchange servers -4, Configure protection settings -4
3 - 4
Notice that after the source and target servers are selected, the Protection Status on the Monitor tab
changes to Unprotected.
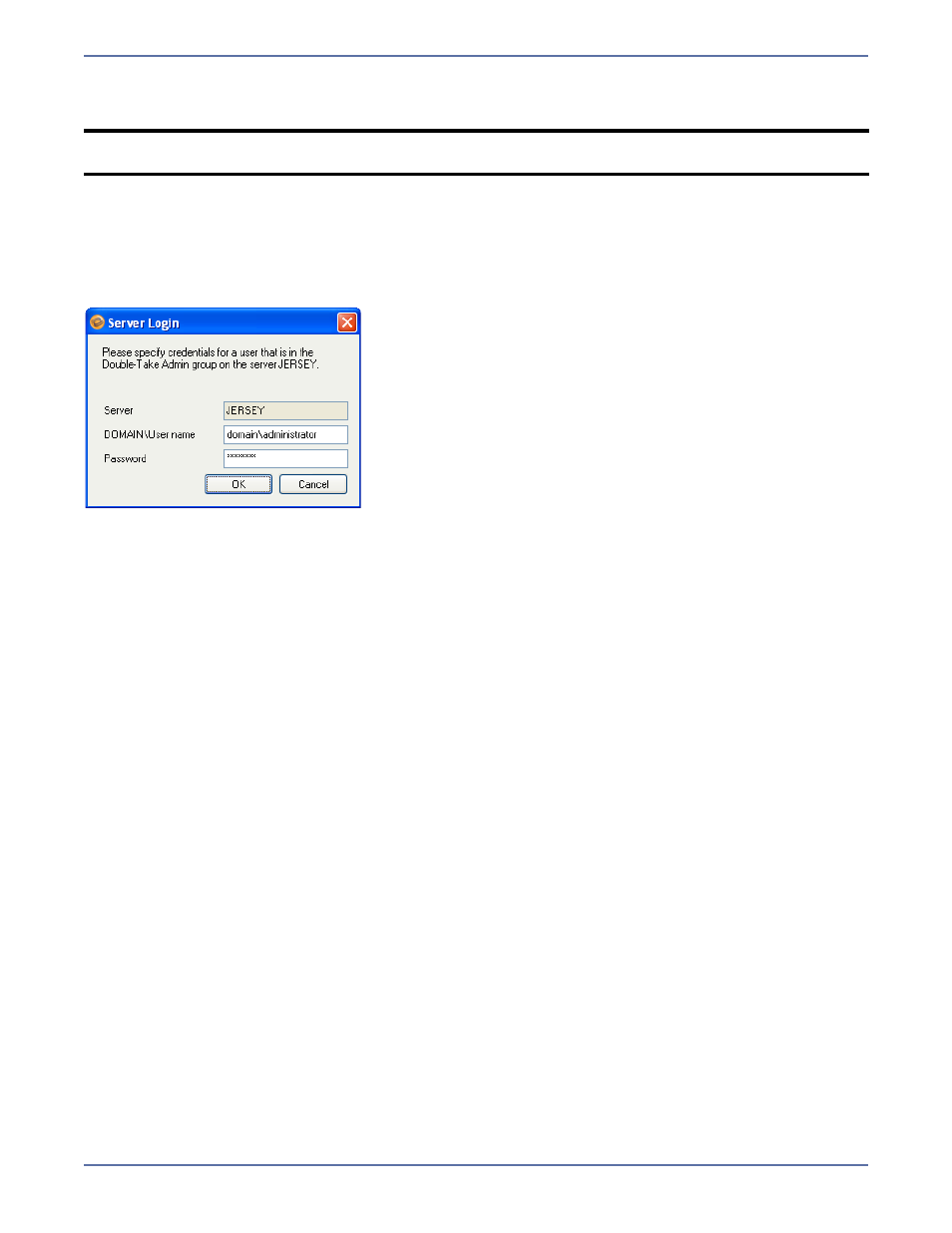
Enter server login information
After you select a server for the first time, you will be prompted to enter a user name and password
to use for logging in to the selected server. The login account MUST be a member of the Storage
Mirroring Admin local security group for the selected server. For more information about permissions,
see
Recommended Credentials
on page A-1.
You may enter a user name for a different domain by entering a fully-qualified user name. The
fully-qualified user name must be in the format domain\username or username@domain. If you
enter a non-qualified name, the DNS domain will be used. Entering the credentials for the logged-on
user may be valid.
The Application Manager will attempt to use the same user name and password the next time you
select a server.
Using clustered Exchange servers
Exchange virtual servers (EVS) are selectable in the same way as physical servers; however, physical
servers that are members of a cluster (called a “node”) are not shown in the server drop-down list.
For more information about setting up protection for a cluster with a like-named cluster, see
Protecting an Exchange Cluster with a Like-Named Cluster
on page 4-1.
Configure protection settings
If you do not need to change the configuration settings, continue with
Validate the Configuration
on page 9-1.
If you have already enabled protection for a connection and need to change the configuration
parameters, you will first need to disable protection as described in
Disable protection
on
page 10-2.
To change the default configuration parameters, click Configure from the main Application Manager
window, or select Actions, Configure Protection from the menu. The Configure Protection window
will appear.
The Configure Protection window has tabs for configuring failover, connection, and advanced settings.
The following sections describe the options on each of these tabs.
NOTE:
If you select a target that is monitoring a connection that has met a failover condition and
requires manual intervention, a prompt will appear asking if you want to initiate failover.
