5 .1 alarm and audit log security – KROHNE Summit 8800 Vol 3 User Manual
Page 27
27
www.krohne.com
08/2013 - MA SUMMIT 8800 Vol3 R02 en
SUMMIT 8800
DATA LOGGING
05
5. DATA LOGGING
To store historical data is one of the major functions of a flow computer. The Summit 8800 is has
3 types of log’s:
Alarm log
Storage of current and historical alarms.
Audit trail log
Storage of any change made to the unit that has metrological significance.
Data log
Storage of user defined data, either periodically or event diven.
The first two are system logs and cannot be changed, however an audit log can be extended with
user defined data.
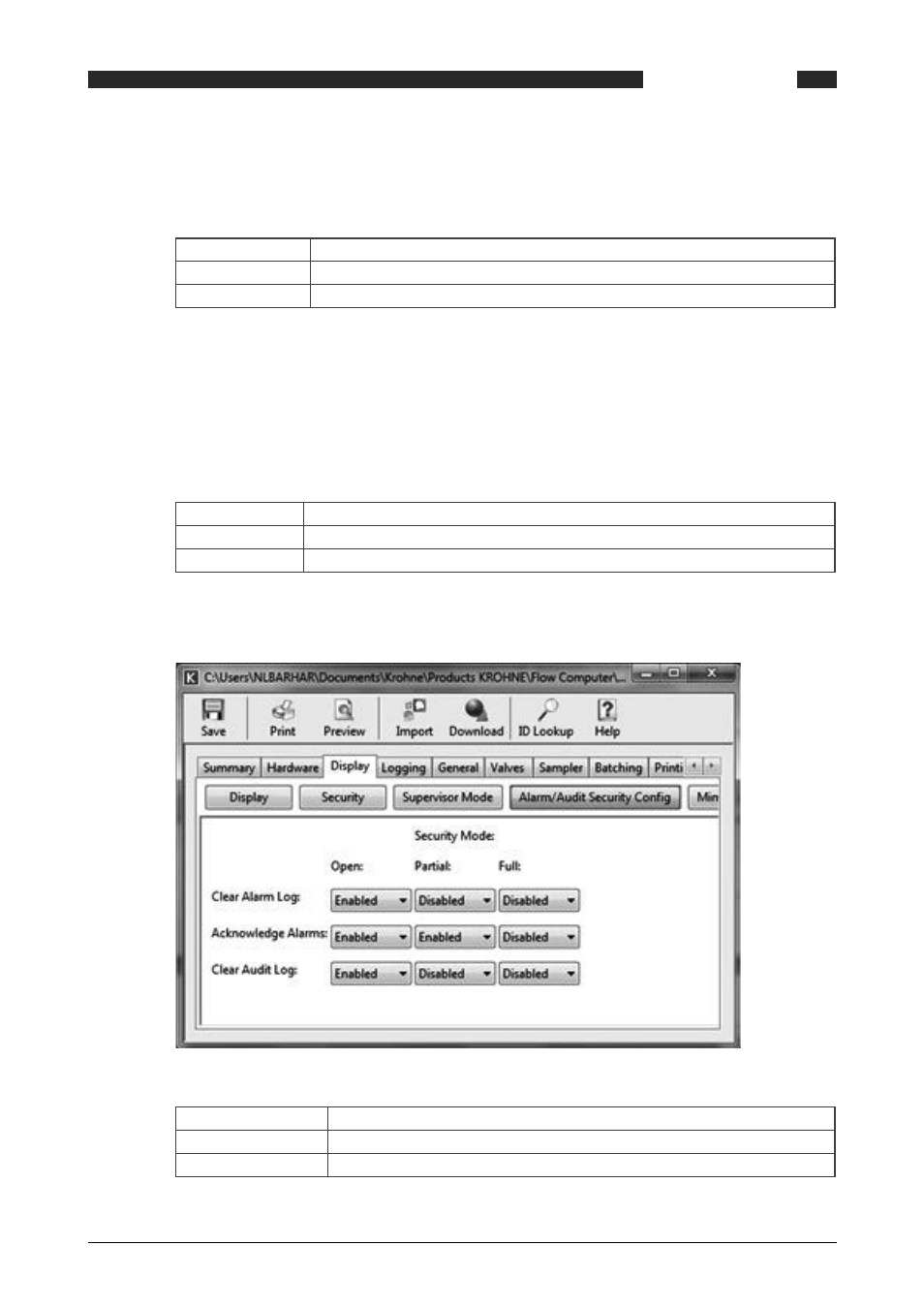
5 .1 Alarm and audit log security
It is possible to define what to do with alarm acknowledgment and clearing alarm and audit logs
depending on the 4 hardware security switches on the back of the Summit. Two of them deter-
mine the security mode of the Summit:
Open
Any changes can be made (using user passwords) and applications can be loaded.
Partial
Changes can be made except calibration data. No new application can be loaded.
Full
No changes in parameters, values or any other data is not possible.
The different security mode also effects the alarm/ audit clearing and acknowledgment and can
be set under “display, alarm/audit security configuration“
Figure 12 Display security window
Clear Alarm Log
Determines if the alarm log may be cleared in open/ partial/ full mode.
Acknowledge Alarms
Determines if the alarms may be acknowledged in open/ partial/ full mode.
Clear Audit Log
Determines if the audit log may be cleared in open/ partial/ full mode.
