2 telecommuters using unique vpn rules example – ZyXEL Communications P-2608HWL-Dx Series User Manual
Page 246
P-2608HWL-Dx Series User’s Guide
246
Chapter 18 IPSec VPN
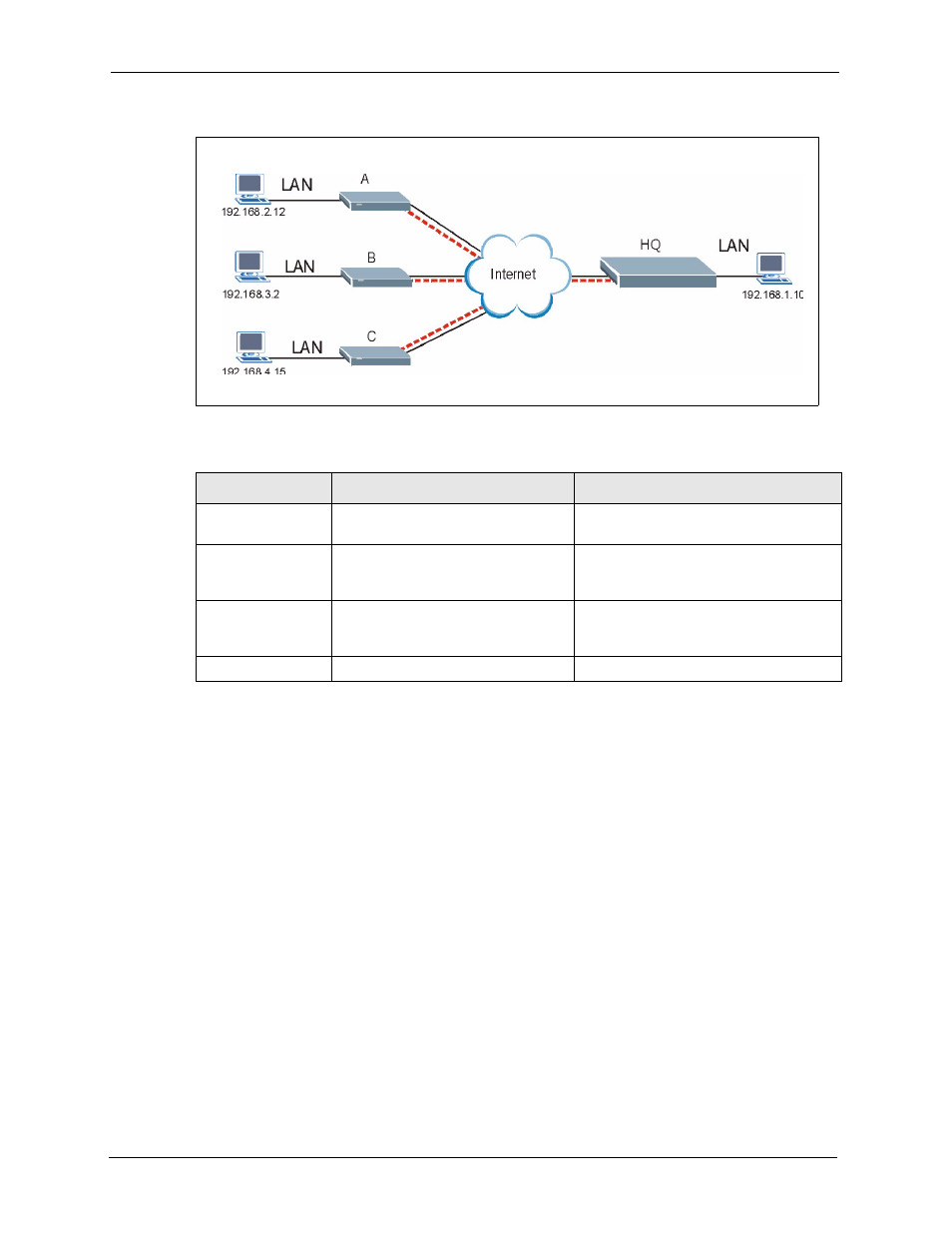
Figure 132 Telecommuters Sharing One VPN Rule Example
18.8.2 Telecommuters Using Unique VPN Rules Example
In this example the telecommuters (A, B and C in the figure) use IPSec routers with domain
names that are mapped to their dynamic WAN IP addresses (use Dynamic DNS to do this).
With aggressive negotiation mode (see
), the ZyXEL Device can
use the ID types and contents to distinguish between VPN rules. Telecommuters can each use
a separate VPN rule to simultaneously access a ZyXEL Device at headquarters. They can use
different IPSec parameters. The local IP addresses (or ranges of addresses) of the rules
configured on the ZyXEL Device at headquarters can overlap. The local IP addresses of the
rules configured on the telecommuters’ IPSec routers should not overlap.
See the following table and figure for an example where three telecommuters each use a
different VPN rule for a VPN connection with a ZyXEL Device located at headquarters. The
ZyXEL Device at headquarters (HQ in the figure) identifies each incoming SA by its ID type
and content and uses the appropriate VPN rule to establish the VPN connection.
The ZyXEL Device at headquarters can also initiate VPN connections to the telecommuters
since it can find the telecommuters by resolving their domain names.
Table 89 Telecommuters Sharing One VPN Rule Example
FIELDS
TELECOMMUTERS
HEADQUARTERS
My IP Address:
0.0.0.0 (dynamic IP address assigned
by the ISP)
Public static IP address
Secure Gateway IP
Address:
Public static IP address
0.0.0.0 With this IP address only the
telecommuter can initiate the IPSec
tunnel.
Local IP Address:
Telecommuter A: 192.168.2.12
Telecommuter B: 192.168.3.2
Telecommuter C: 192.168.4.15
192.168.1.10
Remote IP Address: 192.168.1.10
0.0.0.0 (N/A)
