3 ipsec sa overview, Figure 124 vpn/nat example – ZyXEL Communications P-2608HWL-Dx Series User Manual
Page 227
P-2608HWL-Dx Series User’s Guide
Chapter 18 IPSec VPN
227
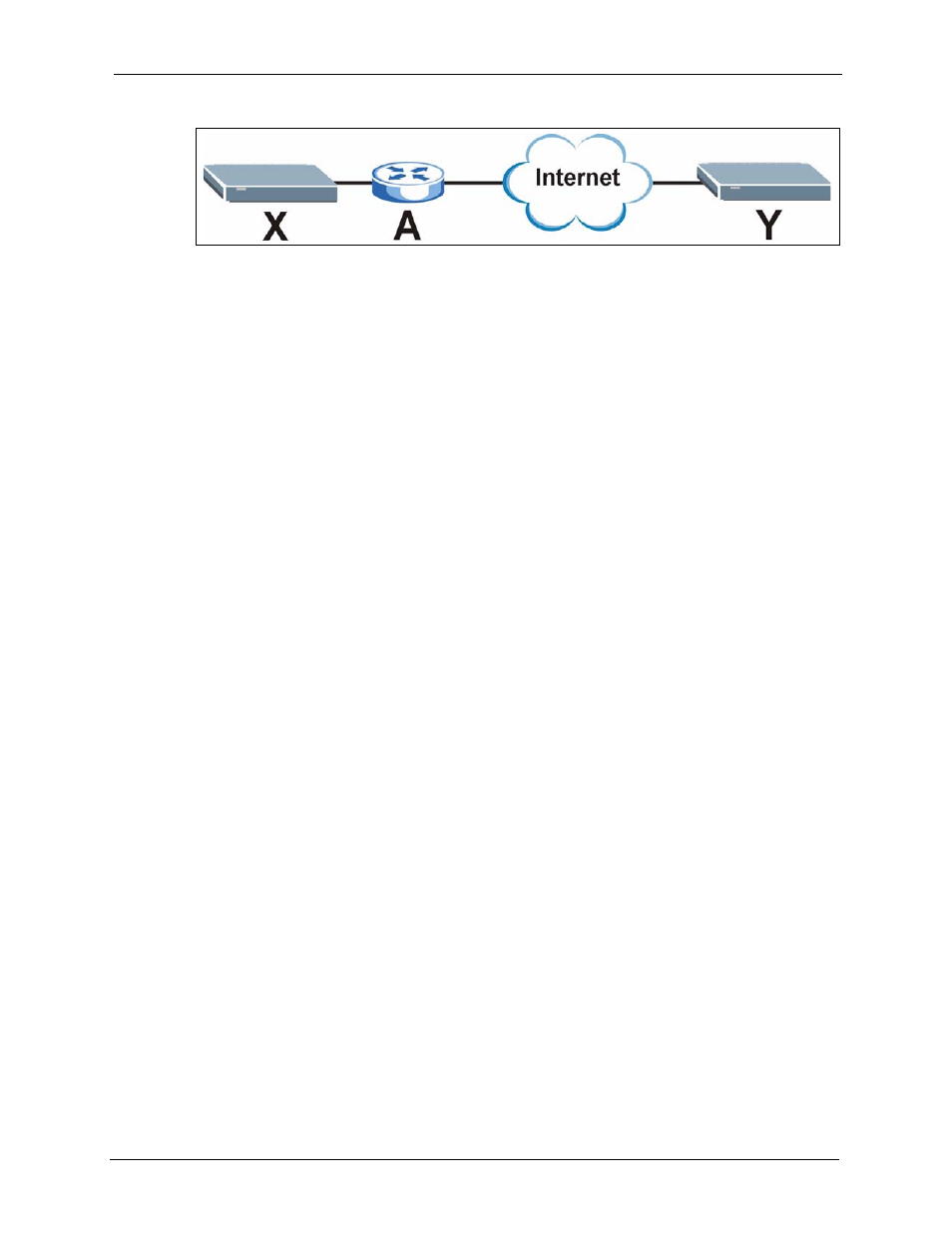
Figure 124 VPN/NAT Example
If router A does NAT, it might change IP addresses (source or destination), port numbers
(source or destination), or any combination of these. If router X and router Y try to establish a
VPN tunnel, the authentication fails because authentication depends on the original IP
addresses and port numbers.
Most routers that support NAT (like router A) have an IPSec pass-through feature. This
feature helps router A recognize VPN packets and route them appropriately. If router A has
this feature, router X and router Y can establish a VPN tunnel as long as the active protocol is
ESP. (See
for more information about active protocols.)
If router A does not have an IPSec pass-through or if the active protocol is AH, you can solve
this problem by enabling NAT traversal. In NAT traversal, router X and router Y add an extra
header to the IKE SA and IPSec SA packets. If you configure router A to forward these
packets unchanged, router X and router Y can establish a VPN tunnel.
You have to do the following things to set up NAT traversal.
• Enable NAT traversal on the ZyXEL Device and remote IPSec router.
• Configure the NAT router to forward packets with the extra header unchanged. The extra
header may be UDP port 500 or UDP port 4500, depending on the standard(s) the ZyXEL
Device and remote IPSec router support.
Note: You must enable NAT traversal on the ZyXEL Device and the remote IPSec
router, and you must configure the NAT router to forward packets with the extra
header unchanged.
18.1.3 IPSec SA Overview
Once the ZyXEL Device and remote IPSec router have established the IKE SA, they can use
the IKE SA to securely negotiate IPSec SAs through which to send data between computers on
the networks.
Note: An IPSec SA stays connected even if the underlying IKE SA is not available
anymore.
This section introduces the key components of IPSec SA.
