Ipsec vpn, 1 ipsec vpn overview, Chapter 18 ipsec vpn – ZyXEL Communications P-2608HWL-Dx Series User Manual
Page 221: Figure 119 vpn: example
P-2608HWL-Dx Series User’s Guide
Chapter 18 IPSec VPN
221
C
H A P T E R
18
IPSec VPN
This chapter explains how tos set up and maintain IPSec VPNs in the ZyXEL Device.
18.1 IPSec VPN Overview
A virtual private network (VPN) provides secure communications between sites without the
expense of leased site-to-site lines. A secure VPN is a combination of tunneling, encryption,
authentication, access control and auditing. It is used to transport traffic over the Internet or
any insecure network that uses TCP/IP for communication.
Internet Protocol Security (IPSec) is a standards-based VPN that offers flexible solutions for
secure data communications across a public network like the Internet. IPSec is built around a
number of standardized cryptographic techniques to provide confidentiality, data integrity and
authentication at the IP layer.
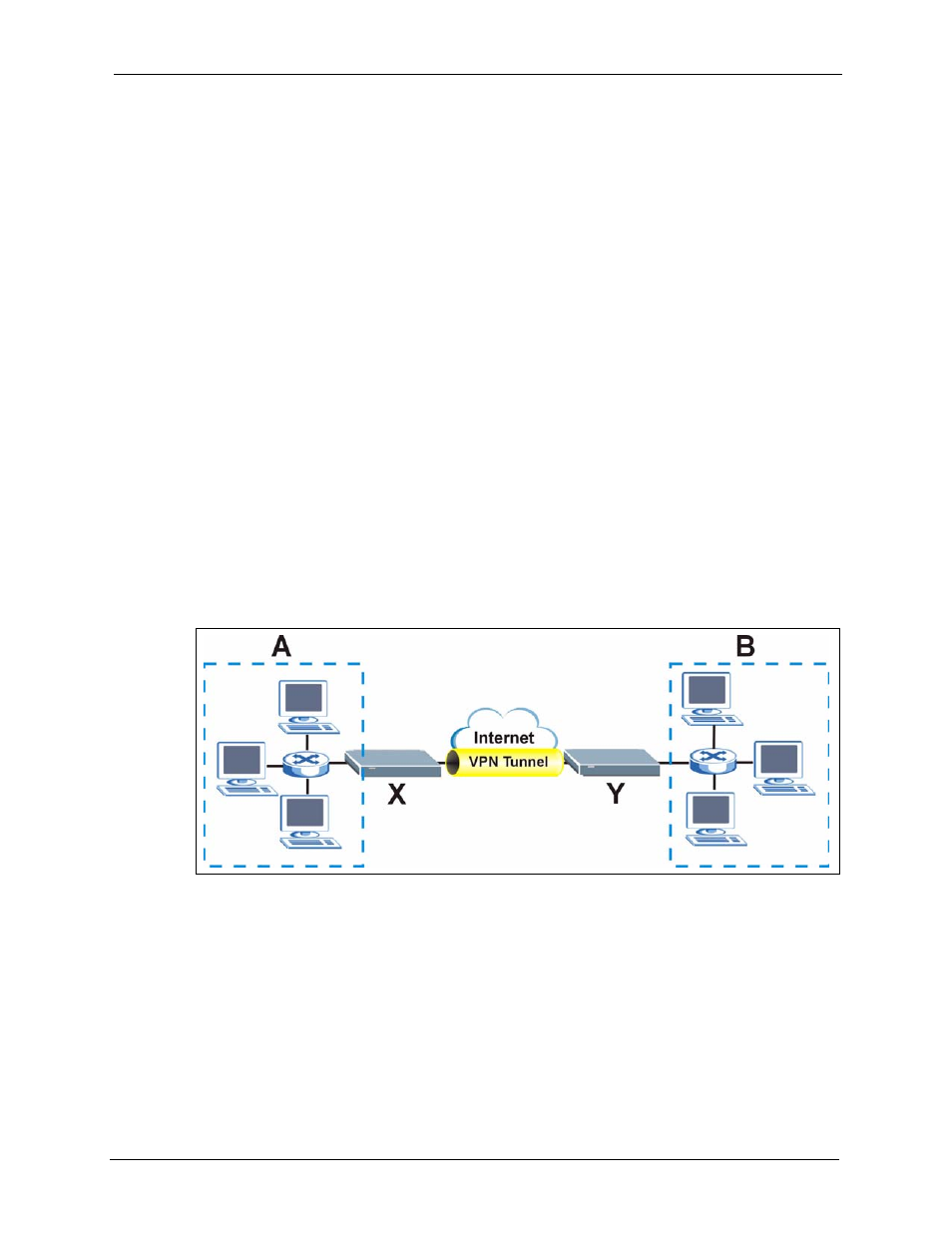
The following figure is one example of a VPN tunnel.
Figure 119 VPN: Example
The VPN tunnel connects the ZyXEL Device (X) and the remote IPSec router (Y). These
routers then connect the local network (A) and remote network (B).
A VPN tunnel is usually established in two phases. Each phase establishes a security
association (SA), a contract indicating what security parameters the ZyXEL Device and the
remote IPSec router will use. The first phase establishes an Internet Key Exchange (IKE) SA
between the ZyXEL Device and remote IPSec router. The second phase uses the IKE SA to
securely establish an IPSec SA through which the ZyXEL Device and remote IPSec router can
send data between computers on the local network and remote network. This is illustrated in
the following figure.
