Access control list examples, Using the permit-established keyword – Extreme Networks 200 Series User Manual
Page 126
124
Summit 200 Series Switch Installation and User Guide
Access Policies
Access Control List Examples
This section presents three access control list examples:
•
Using the permit-establish keyword
•
Filtering ICMP packets
•
Using a rate limit
Using the Permit-Established Keyword
This example uses an access list that permits TCP sessions (Telnet, FTP, and HTTP) to be established in
one direction.
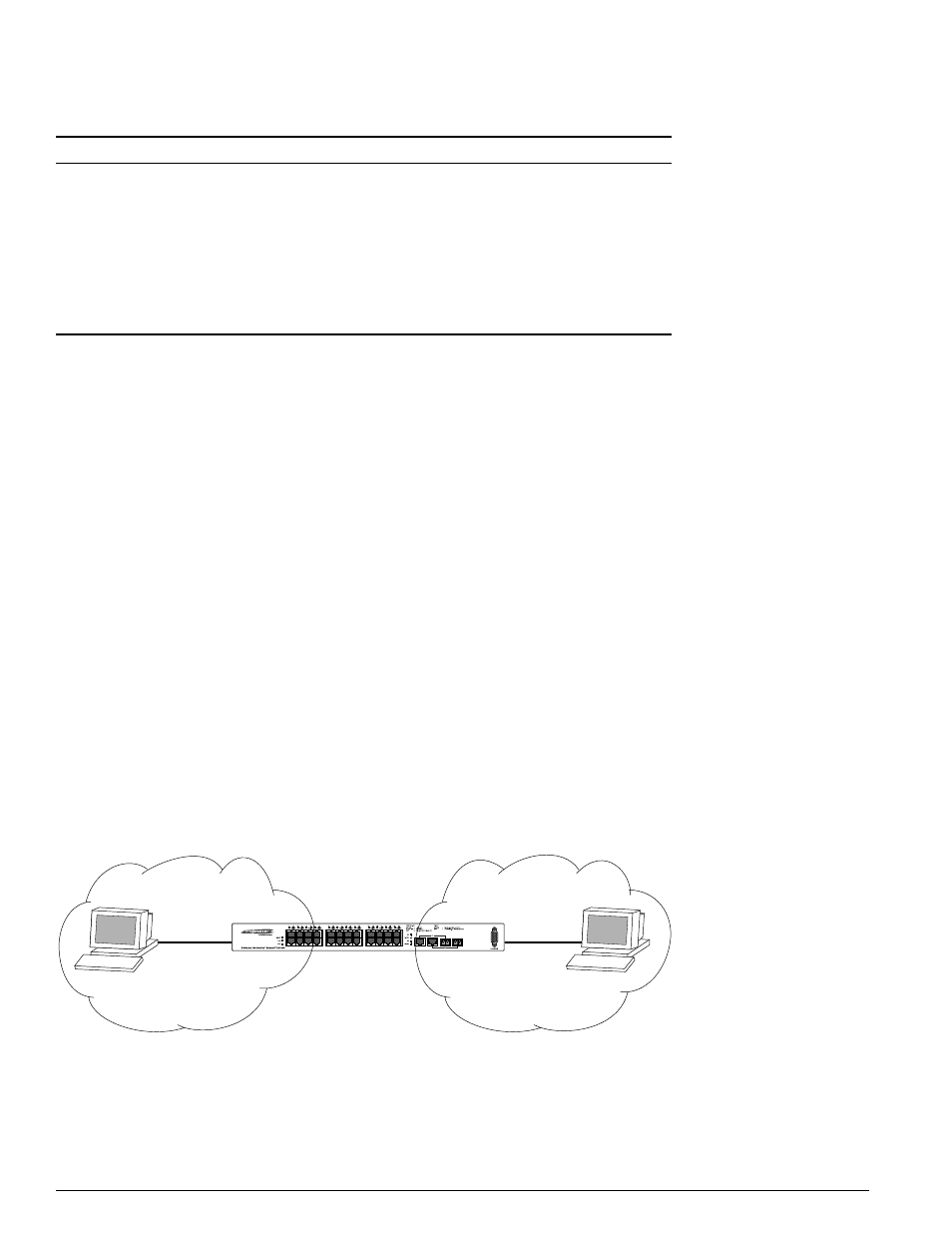
The switch, shown in Figure 16, is configured as follows:
•
Two VLANs, NET10 VLAN and NET20 VLAN, are defined.
•
The NET10 VLAN is connected to port 2 and the NET20 VLAN is connected to port 10
•
The IP addresses for NET10 VLAN is 10.10.10.1/24.
•
The IP address for NET20 VLAN is 10.10.20.1/24.
•
The workstations are configured using addresses 10.10.10.100 and 10.10.20.100.
•
IPForwarding is enabled.
Figure 16: Permit-established access list example topology
The following sections describe the steps used to configure the example.
delete access-list
Deletes an access list.
delete access-mask
Deletes an access mask. Any access lists or rate
limits that reference this mask must first be
deleted.
delete rate-limit
Deletes a rate limit.
show access-list {
Displays access-list information.
show access-mask {
Displays access-list information.
show rate-limit {
Displays access-list information.
Table 32: Access Control List Configuration Commands (continued)
Command
Description
LC24008
10.10.10.1
10.10.10.100
10.10.20.100
10.10.20.1
NET20 VLAN
NET10 VLAN
