Dns spoofing – H3C Technologies H3C WX3000E Series Wireless Switches User Manual
Page 84
73
DNS spoofing
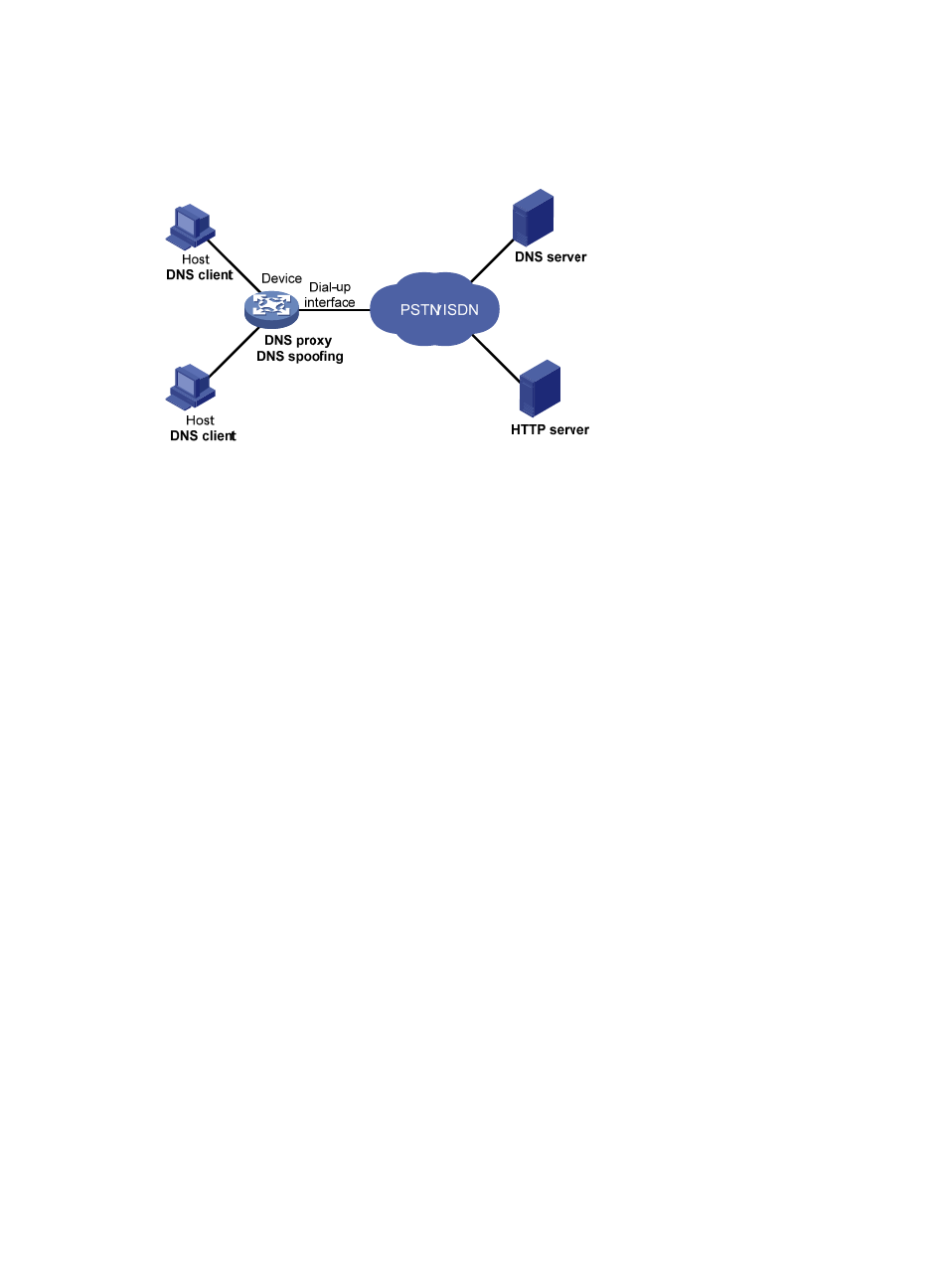
Figure 29 Application of DNS spoofing
DNS spoofing is applied to the dial-up network, as shown in
•
The device connects to the PSTN/ISDN network through a dial-up interface and triggers the
establishment of a dial-up connection only when packets are to be forwarded through the dial-up
interface.
•
The device serves as a DNS proxy and is specified as a DNS server on the hosts. After the dial-up
connection is established through the dial-up interface, the device dynamically obtains the DNS
server address through DHCP or other autoconfiguration mechanisms.
Without DNS spoofing enabled, the device forwards the DNS requests received from the hosts to the
DNS server, if it cannot find a match in the local domain name resolution table. However, without any
dial-up connection established, the device cannot obtain the DNS server address and cannot forward or
answer the requests from the clients. The domain name cannot be resolved and no traffic triggers the
establishment of a dial-up connection.
DNS spoofing can solve the problem. DNS spoofing enables the device to reply the DNS client with a
configured IP address when the device does not have a DNS server address or route to a DNS server.
Subsequent packets sent by the DNS client trigger the establishment of a dial-up connection with the
, a host accesses the HTTP server in following these steps.
1.
The host sends a DNS request to the device to resolve the domain name of the HTTP server into an
IP address.
2.
Upon receiving the request, the device searches the local static and dynamic DNS entries for a
match. If no match is found and the device does know the DNS server address, the device spoofs
the host by replying a configured IP address. The TTL of the DNS reply is 0. Note that the device
must have a route to the IP address with the dial-up interface as the outgoing interface.
3.
Upon receiving the reply, the host sends an HTTP request to the replied IP address.
4.
When forwarding the HTTP request through the dial-up interface, the device establishes a dial-up
connection with the network and dynamically obtains the DNS server address through DHCP or
other autoconfiguration mechanisms.
5.
When the DNS reply ages out, the host sends a DNS request to the device again.
6.
Then the device operates the same as a DNS proxy. For more information, see “
- H3C WX5500E Series Access Controllers H3C WX3500E Series Access Controllers H3C WX2500E Series Access Controllers H3C WX6000 Series Access Controllers H3C WX5000 Series Access Controllers H3C LSWM1WCM10 Access Controller Module H3C LSUM3WCMD0 Access Controller Module H3C LSUM1WCME0 Access Controller Module H3C LSWM1WCM20 Access Controller Module H3C LSQM1WCMB0 Access Controller Module H3C LSRM1WCM2A1 Access Controller Module H3C LSBM1WCM2A0 Access Controller Module H3C WA3600 Series Access Points H3C WA2600 Series WLAN Access Points
