Application environment of trusted ports, Configuring trusted ports in a cascaded network – H3C Technologies H3C WX3000E Series Wireless Switches User Manual
Page 69
58
•
IP source guard: IP source guard uses dynamic binding entries generated by DHCP snooping to
filter packets on a per-port basis, and thus prevents unauthorized packets from traveling through. For
more information, see the Security Configuration Guide.
Application environment of trusted ports
Configuring a trusted port connected to a DHCP server
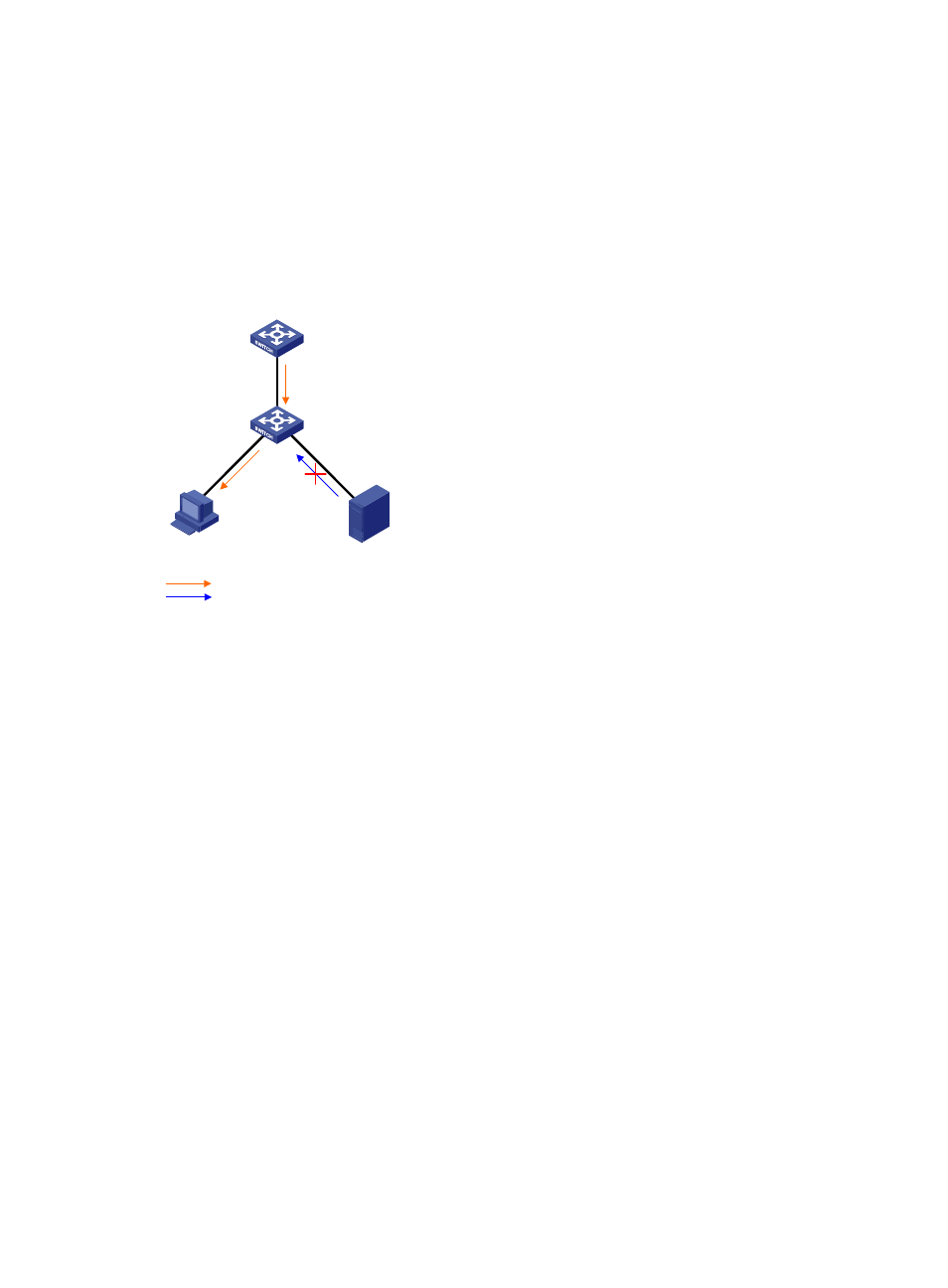
Figure 24 Configure trusted and untrusted ports
As shown in
, the DHCP snooping device port that is connected to an authorized DHCP server
should be configured as a trusted port. The trusted port forwards reply messages from the authorized
DHCP server to the client, but the untrusted port does not forward reply messages from the unauthorized
DHCP server. This ensures that the DHCP client obtains an IP address from the authorized DHCP server.
Configuring trusted ports in a cascaded network
In a cascaded network involving multiple DHCP snooping devices, the ports connected to other DHCP
snooping devices should be configured as trusted ports.
To save system resources, you can disable the trusted ports, which are indirectly connected to DHCP
clients, from recording client IP-to-MAC bindings upon receiving DHCP requests.
Trusted
DHCP server
DHCP snooping
Untrusted
Untrusted
Unauthorized
DHCP server
DHCP client
DHCP reply messages
- H3C WX5500E Series Access Controllers H3C WX3500E Series Access Controllers H3C WX2500E Series Access Controllers H3C WX6000 Series Access Controllers H3C WX5000 Series Access Controllers H3C LSWM1WCM10 Access Controller Module H3C LSUM3WCMD0 Access Controller Module H3C LSUM1WCME0 Access Controller Module H3C LSWM1WCM20 Access Controller Module H3C LSQM1WCMB0 Access Controller Module H3C LSRM1WCM2A1 Access Controller Module H3C LSBM1WCM2A0 Access Controller Module H3C WA3600 Series Access Points H3C WA2600 Series WLAN Access Points
