Table 2. ieee 802.1x configuration – Allied Telesis AT-WA7400/EU User Manual
Page 107
AT-WA7400 Management Software User’s Guide
107
IEEE 802.1x mode is a better choice than Static WEP because keys are
dynamically generated and changed periodically. However, the encryption
algorithm used is the same as that of Static WEP and is therefore not as
reliable as the more advanced encryption methods such as
TKIP
and
SCMP
(
AES
) used in Wi-Fi Protected Access (
WPA
) or
WPA2
.
Additionally, compatibility issues may be cumbersome because of the
variety of authentication methods supported and the lack of a standard
implementation method.
Therefore, IEEE 802.1x mode is not as secure a solution as Wi-Fi
Protected Access (
WPA
) or
WPA2
. If, you cannot use
WPA
because some
of your client stations do not have WPA, then a better solution than using
IEEE 802.1x mode is to use WPA/WPA2 Enterprise (RADIUS) mode
instead and check the Allow non-WPA IEEE 802.1x clients checkbox to
allow non-WPA clients. This provides the benefit of IEEE 802.1x key
management for non-WPA clients along with even better data protection of
TKIP and CCMP (AES) key management and encryption algorithms for
your WPA and WPA2 clients.
If you have an external RADIUS server on your network, Allied Telesis
recommends that you use it rather than the using the embedded RADIUS
server on the access point. An external RADIUS server provides better
security than the local authentication server.
For information on how to configure IEEE 802.1x security mode, see
“IEEE 802.1x” on page 119.
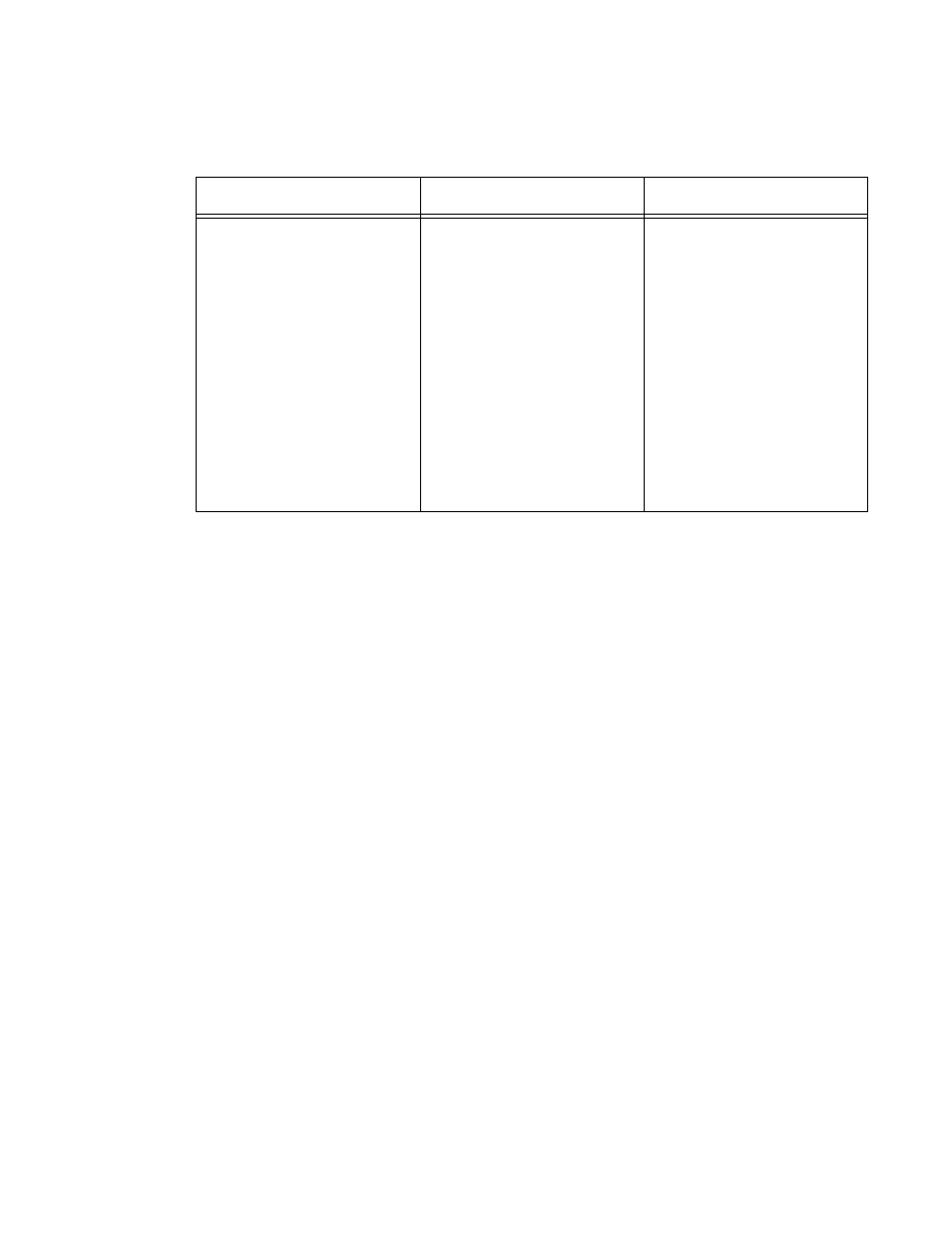
Table 2. IEEE 802.1x Configuration
Key Management
Encryption Algorithm
User Authentication
IEEE 802.1x provides
dynamically-generated
keys that are periodically
refreshed.
There are different
Unicast
keys for each station.
An
RC4
stream cipher is
used to encrypt the frame
body and cyclic
redundancy checking
(CRC) of each 802.11
frame.
EEE 802.1x mode
supports a variety of
authentication methods,
like certificates, Kerberos,
and public key
authentication with a
RADIUS server.
You have a choice of using
the embedded RADIUS
server or an external
RADIUS server. The
embedded RADIUS server
supports Protected
EAP
(PEAP) and MSCHAP V2.
