Security monitoring thresholds – Brocade Monitoring and Alerting Policy Suite Administrators Guide (Supporting Fabric OS v7.3.0) User Manual
Page 108
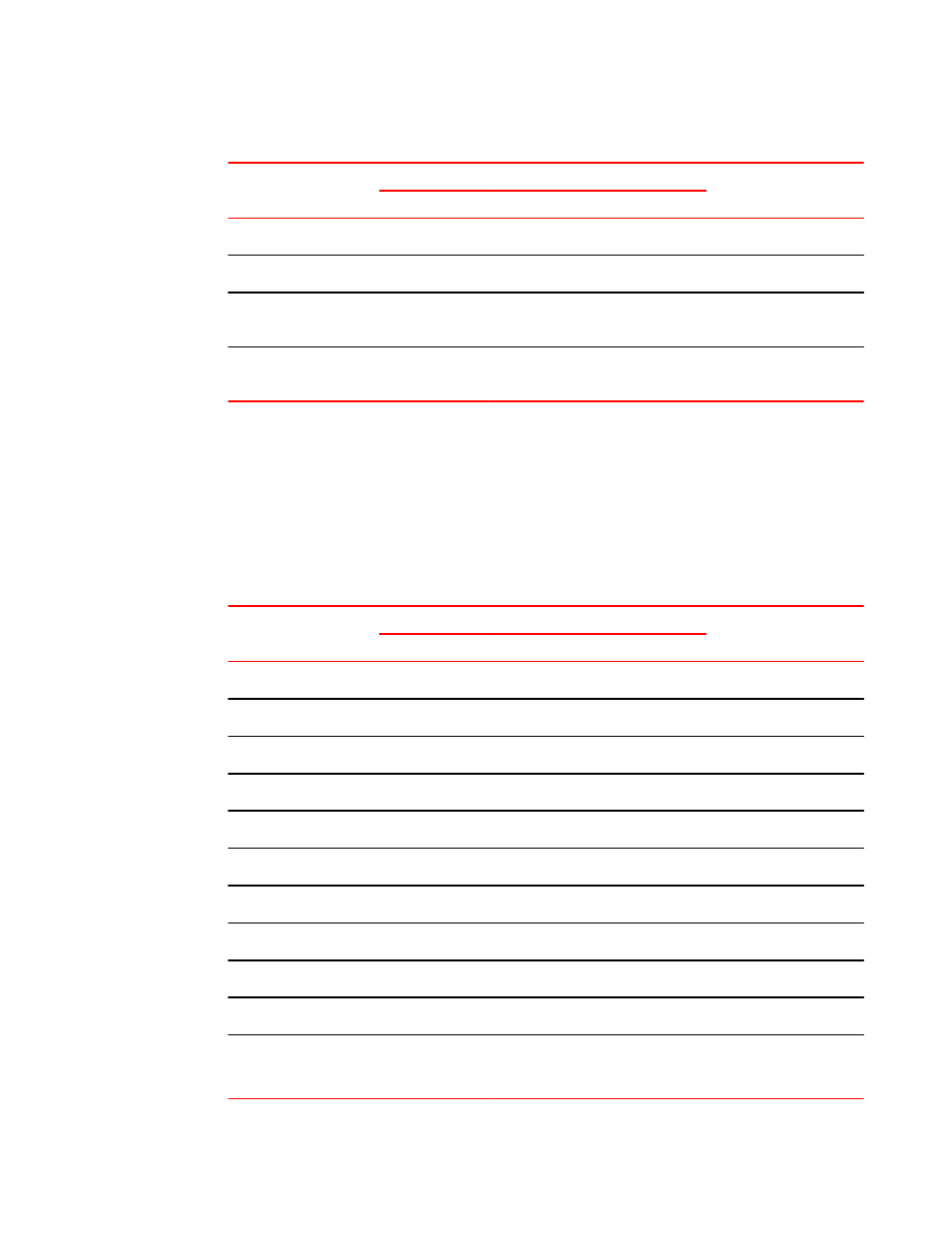
Default resource monitoring thresholds
TABLE 32
Monitoring statistic
MAPS thresholds and actions per policy
Actions
Aggressive
Moderate
Conservative
Flash (percentage used)
90
90
90
RASLOG, SNMP, EMAIL
CPU (percentage used)
80
80
80
RASLOG, SNMP, EMAIL
Memory (percentage
used)
75
75
75
RASLOG, SNMP, EMAIL
Management port (up or
down)
Up/Down
Up/Down
Up/Down
RASLOG, SNMP, EMAIL
Security monitoring thresholds
The following table lists the default monitoring thresholds for security criteria used by MAPS. Unless
noted otherwise, all thresholds are measured per minute and actions are triggered when the reported
value is greater than the threshold value.
Default security monitoring thresholds
TABLE 33
Monitoring statistic
MAPS thresholds and actions per policy
Actions
Aggressive
Moderate
Conservative
DCC violations
0
2
4
RASLOG, SNMP, EMAIL
HTTP violation
0
2
4
RASLOG, SNMP, EMAIL
Illegal command
0
2
4
RASLOG, SNMP, EMAIL
Incompatible security DB 0
2
4
RASLOG, SNMP, EMAIL
Login violations
0
2
4
RASLOG, SNMP, EMAIL
Invalid certifications
0
2
4
RASLOG, SNMP, EMAIL
No-FCS
0
2
4
RASLOG, SNMP, EMAIL
SCC violations
0
2
4
RASLOG, SNMP, EMAIL
SLAP failures
0
2
4
RASLOG, SNMP, EMAIL
Telnet violations
0
2
4
RASLOG, SNMP, EMAIL
TS out of sync
1/hr
2/day
2/hr
4/day
4/hr
10/day
RASLOG, SNMP, EMAIL
Security monitoring thresholds
108
Monitoring and Alerting Policy Suite Administrator's Guide
53-1003147-01
