Tunneled authentication, Tunneled authentication -8 – Motorola ENTERPRISE DIGITAL ASSISTANT MC70 User Manual
Page 132
7 - 8
MC70 Integrator Guide
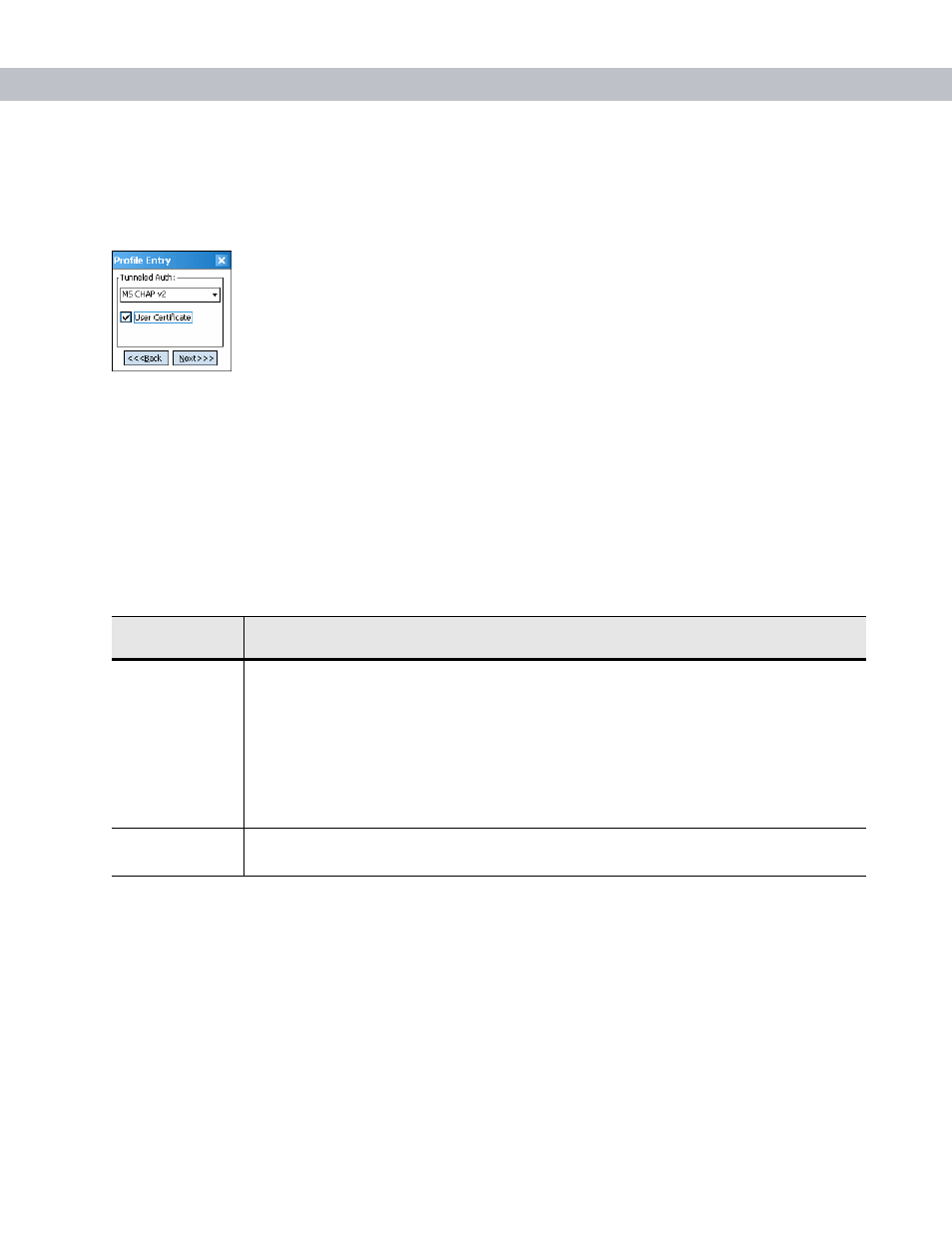
Tunneled Authentication
Use the
Tunneled Authentication
dialog box to select the tunneled authentication options. There are different
selections available for PEAP or TTLS authentication.
Figure 7-9
Tunneled Authentication Dialog Box
To select a tunneled authentication type:
1.
Select a tunneled authentication type from the drop-down list. See
2.
Select the
User Certificate
check box if a certificate is required. If you selected the TLS tunnel type that
requires a user certificate, the check box is already selected.
3.
Tap
Next
. The
Installed User Certificates
dialog box appears.
lists the PEAP tunneled authentication options.
Table 7-7
PEAP Tunneled Authentication Options
PEAP Tunneled
Authentication
Description
MS CHAP v2
Microsoft Challenge Handshake Authentication Protocol version 2 (MS CHAP v2) is a
password-based, challenge-response, mutual authentication protocol that uses the
industry-standard Message Digest 4 (MD4) and Data Encryption Standard (DES)
algorithms to encrypt responses. The authenticating server challenges the access client
and the access client challenges the authenticating server. If either challenge is not
correctly answered, the connection is rejected. MS CHAP v2 was originally designed by
Microsoft as a PPP authentication protocol to provide better protection for dial-up and
virtual private network (VPN) connections. With Windows XP SP1, Windows XP SP2,
Windows Server 2003, and Windows 2000 SP4, MS CHAP v2 is also an EAP type.
TLS
EAP TLS is used during phase 2 of the authentication process. This method uses a user
certificate to authenticate.
