Performing optional configuration, Authentication – HP Remote Device Access Software User Manual
Page 36
Access Control
Description
User
The name of the user for which access is or is not granted.
Access Allowed
This check box indicates if access is allowed or denied. A selected check box
indicates access is allowed. A clear check box indicates access is denied.
Action
Click
to delete a user account from the vCAS.
Table 4.8 Permitted Shell Logins
Performing Optional Configuration
From the Tools menu, you can configure the following options:
l
Authentication
l
Email Alerts
l
Licensing
l
Preferences
l
Remote Logging
l
Setup
l
Software Updates
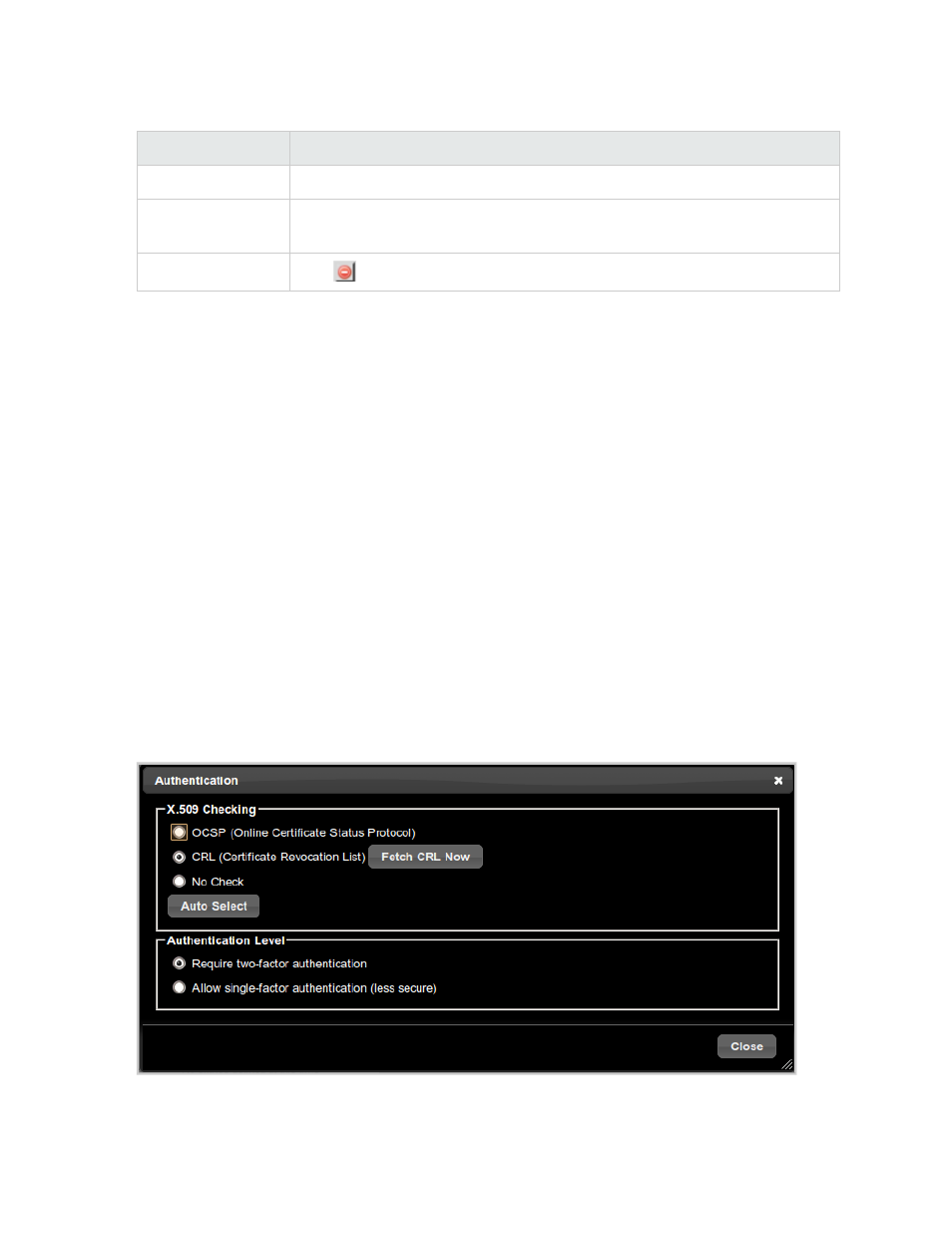
Authentication
Incoming connections are authenticated using X.509 certificates. Some of these certificates are revoked
before they expire. The Authentication dialog box allows administrators to select the way the vCAS
checks the setting of the X.509 certificates. There are three options for certificate revocation checking:
OCSP, CRL, and No Check.
Figure 4.8 Authentication
HP Remote Device Access 8.1: vCAS User Guide
Page 36 of 65
Chapter 4: Managing your vCAS
- Scripting Toolkit for Linux (68 pages)
- Scripting Toolkit for Windows 9.50 (62 pages)
- Scripting Toolkit for Windows 9.60 (62 pages)
- Storage Area Manager (13 pages)
- Core HP-UX (5 pages)
- Matrix Operating Environment Software (34 pages)
- Matrix Operating Environment Software (63 pages)
- Matrix Operating Environment Software (67 pages)
- Matrix Operating Environment Software (128 pages)
- Matrix Operating Environment Software (104 pages)
- Matrix Operating Environment Software (75 pages)
- Matrix Operating Environment Software (245 pages)
- Matrix Operating Environment Software (209 pages)
- Matrix Operating Environment Software (71 pages)
- Matrix Operating Environment Software (239 pages)
- Matrix Operating Environment Software (107 pages)
- Matrix Operating Environment Software (77 pages)
- Insight Management-Software (148 pages)
- Matrix Operating Environment Software (80 pages)
- Insight Management-Software (128 pages)
- Matrix Operating Environment Software (74 pages)
- Matrix Operating Environment Software (132 pages)
- Matrix Operating Environment Software (76 pages)
- Matrix Operating Environment Software (233 pages)
- Matrix Operating Environment Software (61 pages)
- Matrix Operating Environment Software (232 pages)
- Matrix Operating Environment Software (120 pages)
- Matrix Operating Environment Software (70 pages)
- Matrix Operating Environment Software (36 pages)
- Matrix Operating Environment Software (99 pages)
- Matrix Operating Environment Software (192 pages)
- Matrix Operating Environment Software (198 pages)
- Matrix Operating Environment Software (66 pages)
- Matrix Operating Environment Software (152 pages)
- Matrix Operating Environment Software (95 pages)
- Matrix Operating Environment Software (264 pages)
- Matrix Operating Environment Software (138 pages)
- Matrix Operating Environment Software (137 pages)
- Matrix Operating Environment Software (97 pages)
- Matrix Operating Environment Software (33 pages)
- Matrix Operating Environment Software (189 pages)
- Matrix Operating Environment Software (142 pages)
- Matrix Operating Environment Software (58 pages)
- Matrix Operating Environment Software (68 pages)
- Matrix Operating Environment Software (79 pages)
