Grant access – HP Remote Device Access Software User Manual
Page 34
The Permitted Tunnels screen contains the following columns:
Access Control
Description
User
Displays the name of the user to be granted access. Any displays when all
users are allowed access.
Target
Displays the name of the host to which access is to be granted. Any displays
when a user can access any system within the customer's network.
Port
Displays the name of the port on the target to which access is to be granted.
Any displays when a user can access all ports on the target.
Proto
Displays the protocol the user has been granted access to. This can be one of
TCP/UDP/ANY. ANY displays when TCP and UDP traffic is allowed.
Action
Click
to edit a field. Click
to delete the value in the field.
Note: When you click
or
, the Grant Access dialog box
appears with the fields pre-populated with the current values.
Table 4.6 Permitted Tunnels
Note: If there are no access control entries, then No entries defined at this table displays in
the table.
To add new values to the Permitted Tunnels table, click Add Whitelist Entry. The Grant Access dialog
box appears. For more information about the Grant Access dialog box, see
".
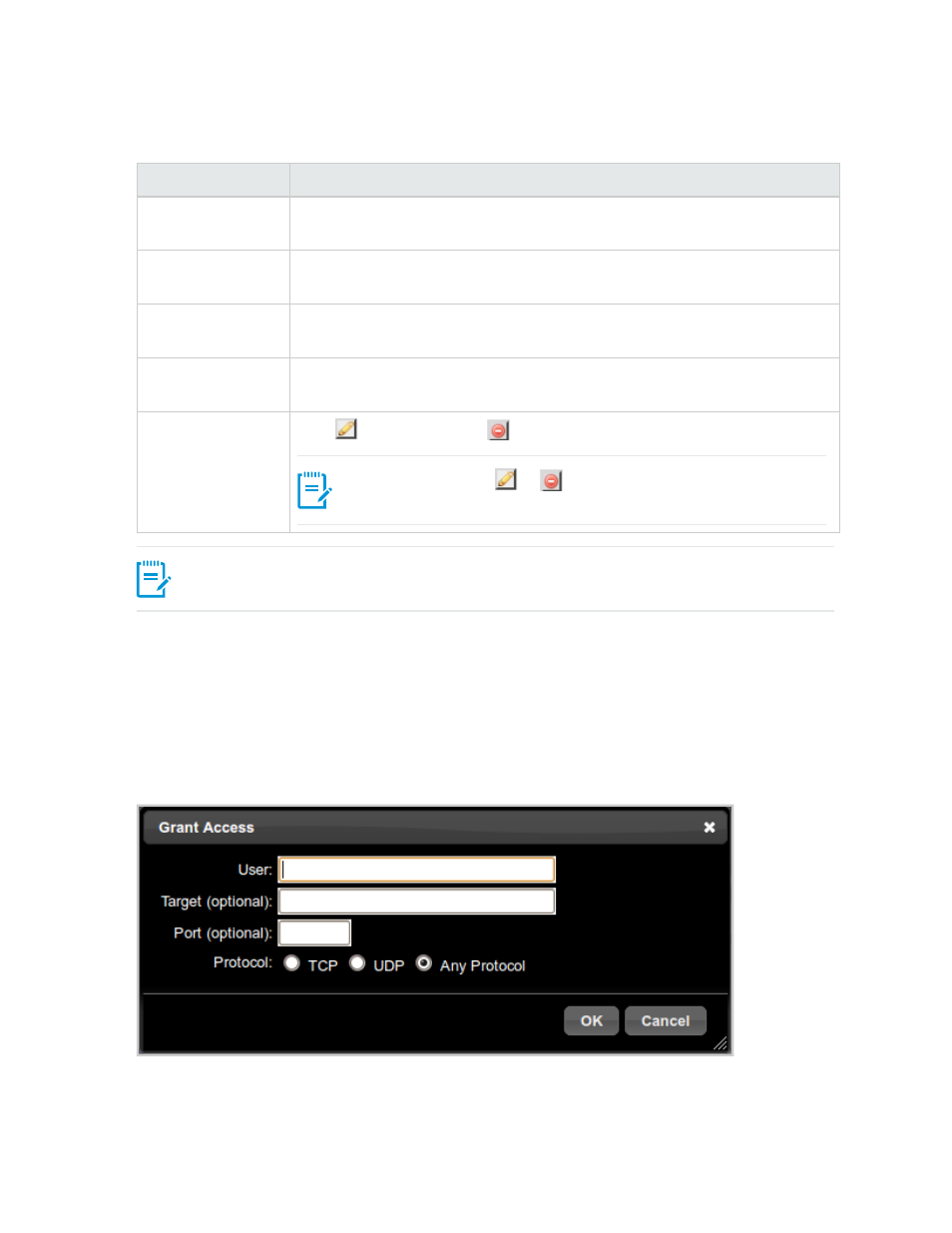
Grant Access
The Grant Access Dialog box allows you to add or modify information entered in the Permitted Tunnels
table.
Figure 4.6 Grant Access dialog box
The Grant Access dialog box contains the following fields:
HP Remote Device Access 8.1: vCAS User Guide
Page 34 of 65
Chapter 4: Managing your vCAS
