Controlling access, Tunnel access control – HP Remote Device Access Software User Manual
Page 33
Controlling Access
The Access Control tab allows you define who can tunnel through your vCAS into your network and to
what and where they can connect. It also allows you define who can log on to a command shell on your
vCAS. The Access Control tab also allows administrators to change the access control for tunnel access
and user login access.
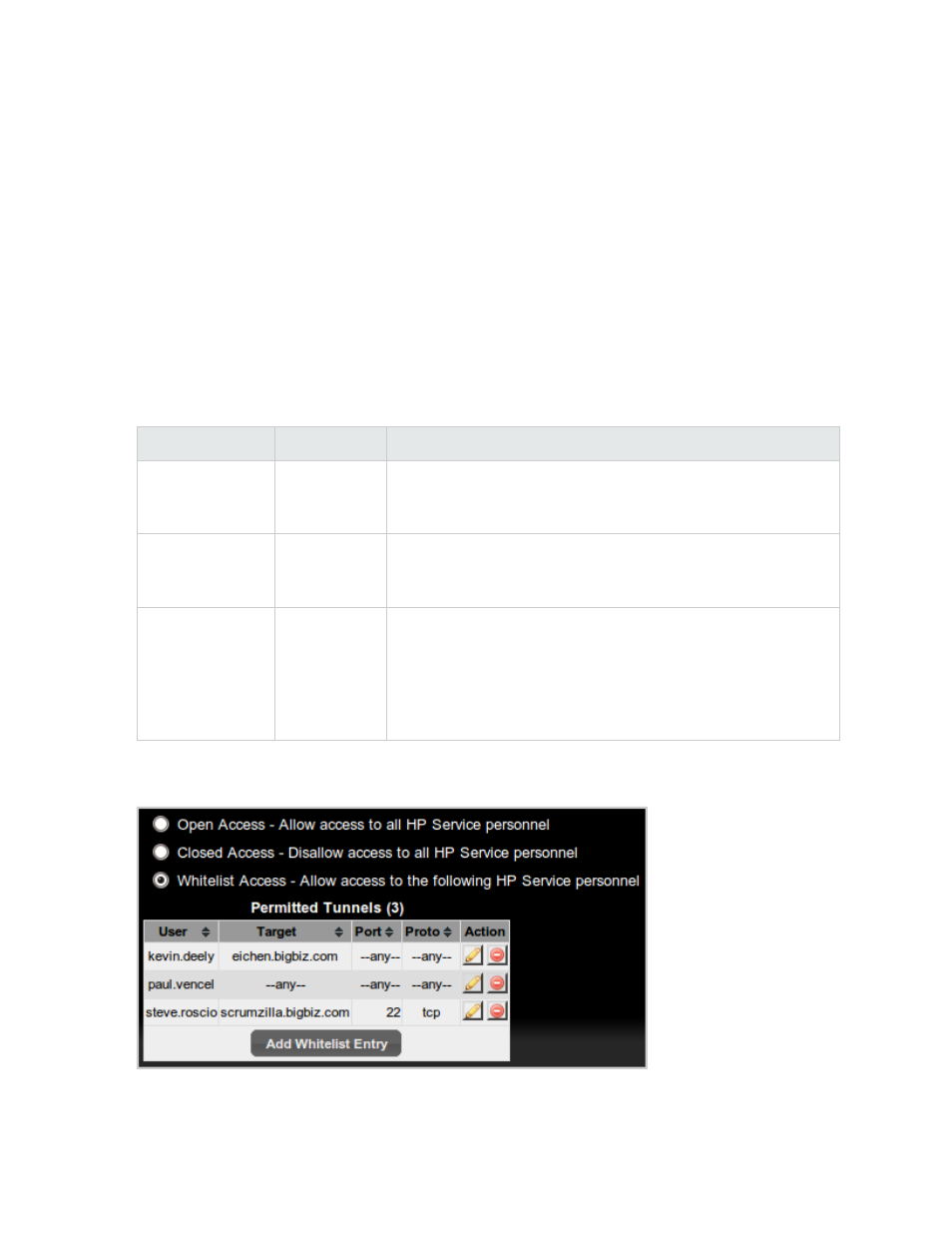
Tunnel Access Control
Tunnel access control allows administrators to control the access a user has to open a tunnel to a target
within the customer's network. Access control types display as radio buttons on the GUI.
The following table describes each of the access control types:
Access Control
Action
Description
Open Access
Allows
access to all
HP users
Allows any HP user with a valid DigitalBadge authentication
access to the vCAS and any of the targets configured to it.
Closed Access
Denies
access to all
HP users
Denies access to or through the vCAS for all users.
Whitelist Access
Allows
access to the
HP users as
per the
Permitted
Tunnels list
Allows HP users with a valid DigitalBadge authentication access
through the vCAS if they are configured in a whitelist. Access is
closed for users who are not configured in this list.
Table 4.5 Access Control Types
You can view user and tunnel information in the Permitted Tunnels table.
Figure 4.5 Permitted Tunnels
HP Remote Device Access 8.1: vCAS User Guide
Page 33 of 65
Chapter 4: Managing your vCAS
