Proxy arp, Route interface grouping, Gratuitous arp generation – D-Link DFL-2500 User Manual
Page 96
automatically be transferred back to it.
Route Interface Grouping
When using route monitoring, it is important to check if a failover to another route will cause the
routing interface to be changed. If this could happen, it is necessary to take some precautionary steps
to ensure that policies and existing connections will be maintained.
To illustrate the problem, consider the following configuration:
First, there is one IP rule that will NAT all HTTP traffic destined for the Internet through the wan
interface:
#
Action
Src Iface
Src Net
Dest Iface
Dest Net
Parameters
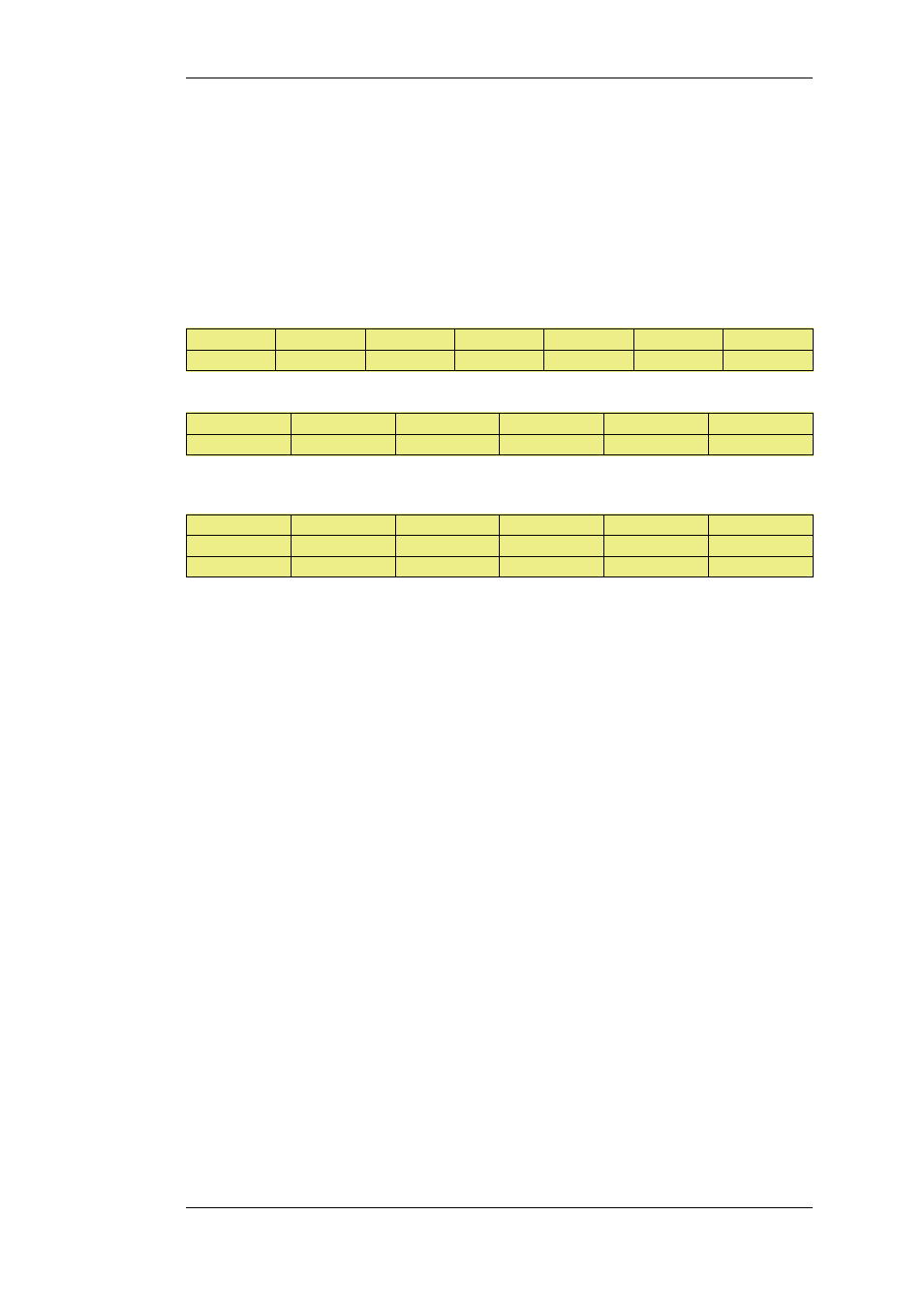
1
NAT
lan
lannet
wan
all-nets
http
The routing table consequently contains the following default route:
Route #
Interface
Destination
Gateway
Metric
Monitoring
1
wan
all-nets
195.66.77.1
10
Off
Now a secondary route is added over a backup DSL connection and Route Monitoring is enabled for
this. The updated routing table will look like this:
Route #
Interface
Destination
Gateway
Metric
Monitoring
1
wan
all-nets
195.66.77.1
10
On
2
dsl
all-nets
193.54.68.1
20
Off
Notice that Route Monitoring is enabled for the first route but not the backup, failover route.
As long as the preferred wan route is healthy, everything will work as expected. Route Monitoring
will also be functioning, so the secondary route will be enabled should the wan route fail.
There are, however, some problems with this setup: if a route failover occurs, the default route will
then use the dsl interface. When a new HTTP connection is then established from the intnet
network, a route lookup will be made resulting in a destination interface of dsl. The IP rules will
then be evaluated, but the original NAT rule assumes the destination interface to be wan so the new
connection will be dropped by the rule set.
In addition, any existing connections matching the NAT rule will also be dropped as a result of the
change in the destination interface. Clearly, this is undesirable.
To overcome this issue, potential destination interfaces should be grouped together into an Interface
Group and the Security/Transport Equivalent flag should be enabled for the Group. The Interface
Group is then used as the Destination Interface when setting policies. For more information on
groups, see Section 3.3.6, “Interface Groups”.
Gratuitous ARP Generation
By default NetDefendOS generates a gratuitous ARP request when a route failover occurs. The
reason for this is to notify surrounding systems that there has been a route change. This behaviour
can be controlled by the advanced setting RFO_GratuitousARPOnFail.
4.2.4. Proxy ARP
As explained previously in Section 3.4, “ARP”, the ARP protocol facilitates a mapping between an
IP address and the MAC address of a node on an Ethernet network. However, situations may exist
where a network running Ethernet is separated into two parts with a routing device such as an
installed D-Link Firewall, in between. In such a case, NetDefendOS itself can respond to ARP
requests directed to the network on the other side of the D-Link Firewall using the feature known as
Proxy ARP.
For example, host A on one subnet might send an ARP request to find out the MAC address of the
4.2.4. Proxy ARP
Chapter 4. Routing
96
