Mac access, Wireless-a or wireless-b, Mac access wireless-a or wireless-b – Proxim AP-4000 User Manual
Page 123
Advanced Configuration
AP-4000 Series User Guide
SSID/VLAN/Security
123
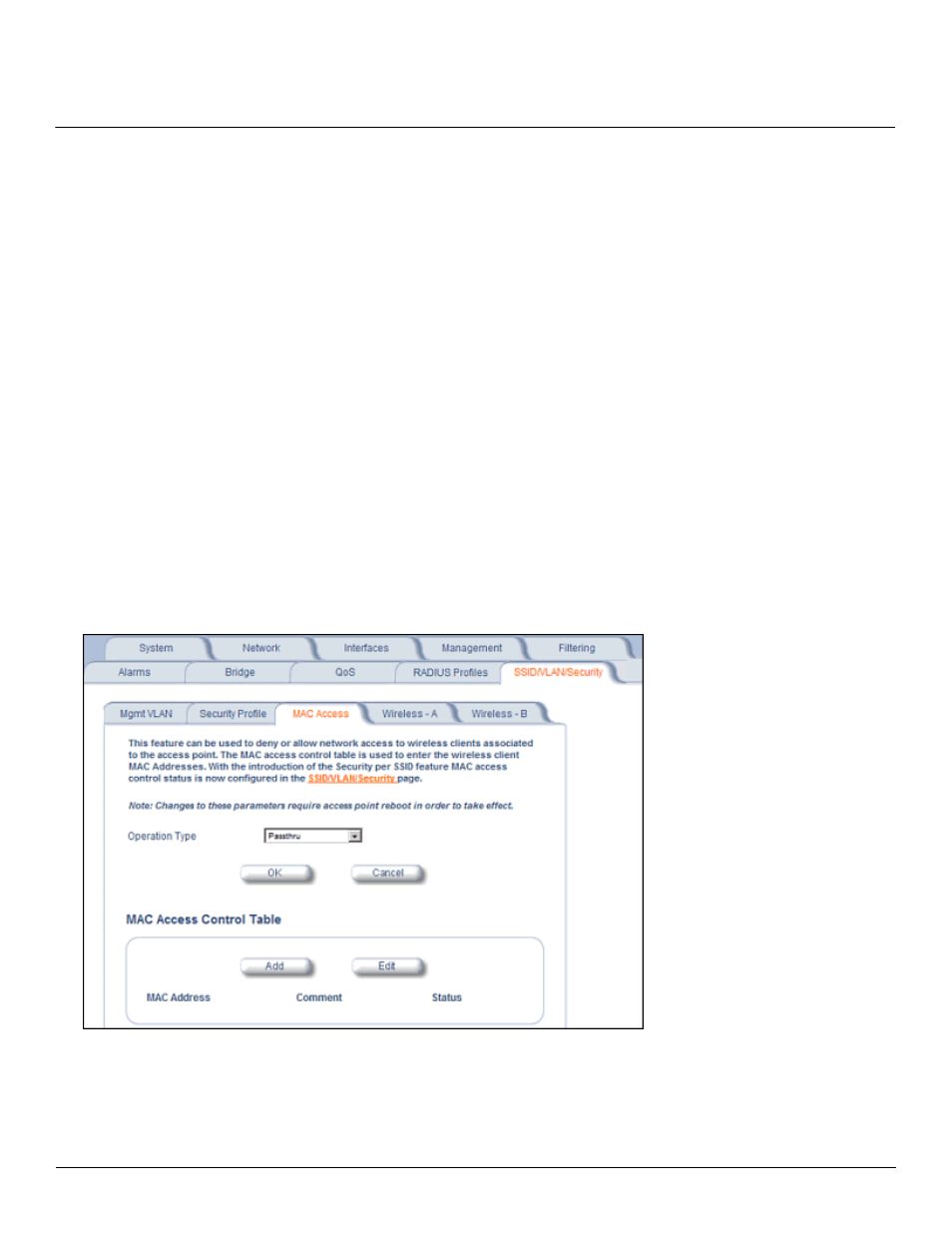
MAC Access
The MAC Access sub-tab allows you to build a list of stations, identified by their MAC addresses, authorized to access
the network through the AP. The list is stored inside each AP within your network. Note that you must reboot the AP for
any changes to the MAC Access Control Table to take effect. Up to 1000 entries can be made in the table.
The “MAC ACL Status” parameter (configurable on the SSID/VLAN > Wireless A or B sub-tab) is per VLAN if VLAN
Management is enabled. All other parameters besides “MAC ACL Status” are configured per AP, even if VLAN is
enabled.
The following list details the configurable MAC Access parameters.
NOTE: MAC Access Control status is enabled or disabled when configuring each Security Profile.
• Operation Type: Choose between Passthru and Block. This determines how the stations identified in the MAC
Access Control Table are filtered.
•
If set to Passthru, only the addresses listed in the Control Table will pass through the bridge.
•
If set to Block, the bridge will block traffic to or from the addresses listed in the Control Table.
• MAC Access Control Table: Click Add to create a new entry. Click Edit to change an existing entry. Each entry
contains the following field:
–
MAC Address: Enter the wireless client’s MAC address.
–
Comment: Enter an optional comment such as the client’s name.
–
Status: The entry is enabled automatically when saved (so the Status field is only visible when editing an entry).
You can also disable or delete entries by changing this field’s value.
NOTE: For larger networks that include multiple Access Points, you may prefer to maintain this list on a centralized
location using the
MAC Access Control Via RADIUS Authentication
.
Figure 4-43 MAC Access Configuration Screen
Wireless-A or Wireless-B
Each SSID can have its own Security Profile that defines its security mode, authentication mechanism, and encryption,
so that customers can have multiple types of clients (non-WEP, WEP, 802.1x, WPA, WPA-PSK, 802.11i, 802.11i-PSK) on
