How authentication works – Echelon LonTal Stack User Manual
Page 85
LonTalk Stack Developer’s Guide
73
tool, but must specify an authentication key because the device has only a default
key.
How Authentication Works
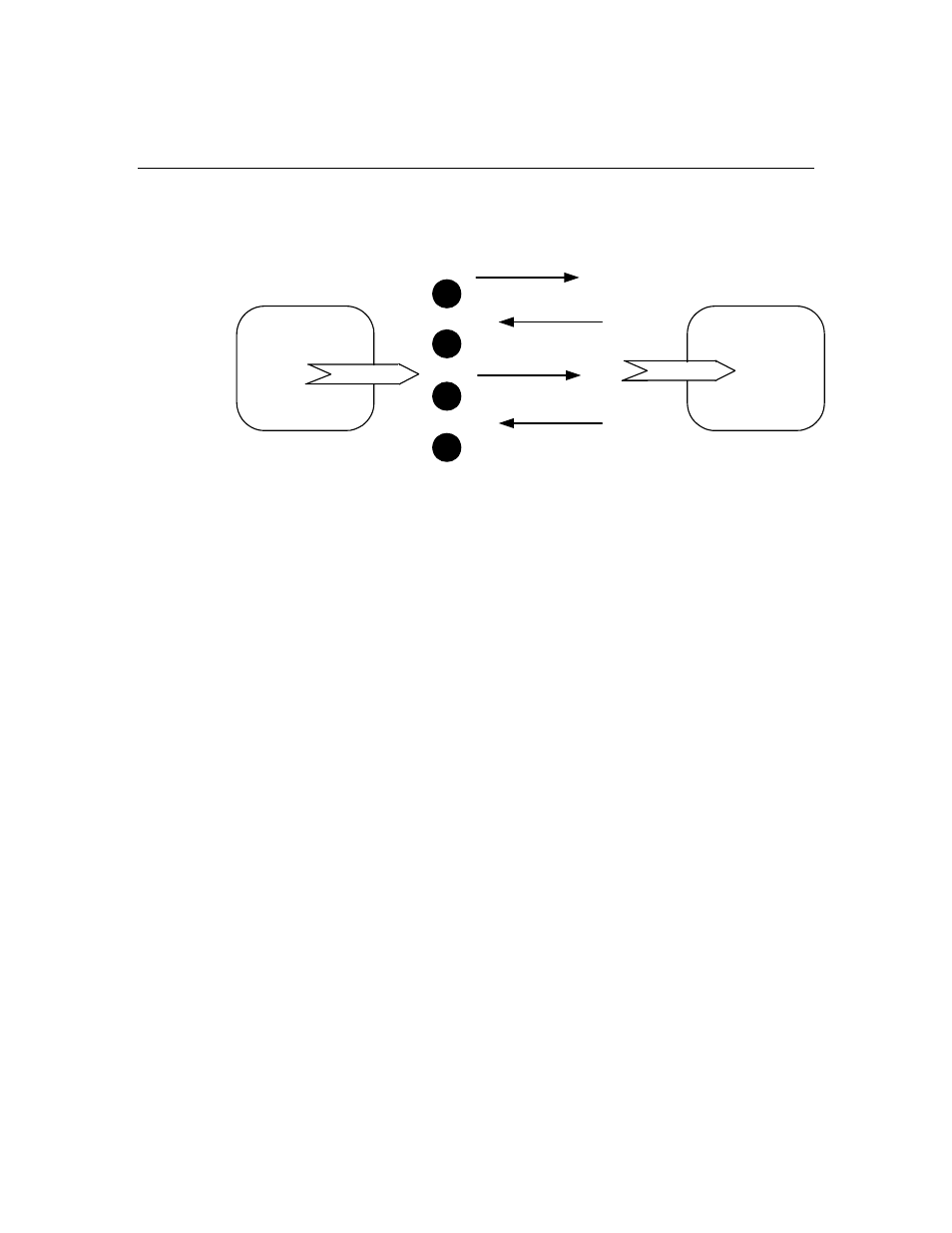
The following figure illustrates the authentication process:
Device B
(reader)
1
2
3
4
ACKD Message or
Request
Challenge
Reply to challenge
ACK or Response
Device A
(Writer)
1. Device A uses the acknowledged service to send an update to a network
variable that is configured with the authentication attribute on Device B.
If Device A does not receive the challenge (described in step 2), it sends a
retry of the initial update.
2. Device B generates a 64-bit random number and returns a challenge
packet that includes the 64-bit random number to Device A. Device B
then uses an encryption algorithm (part of the LonTalk host stack) to
compute a transformation on that random number using its 48-bit
authentication key and the message data. The transformation is stored
in Device B.
3. Device A then also uses the same encryption algorithm to compute a
transformation on the random number (returned to it by Device B) using
its 48-bit authentication key and the message data. Device A then sends
this computed transformation to Device B.
4. Device B compares its computed transformation with the number that it
receives from Device A. If the two numbers match, the identity of the
sender is verified, and Device B can perform the requested action and
send its acknowledgment to Device A. If the two numbers do not match,
Device B does not perform the requested action, and an error is logged in
the error table.
If the acknowledgment is lost and Device A tries to send the same message again,
Device B remembers that the authentication was successfully completed and
acknowledges it again.
If Device A attempts to update an output network variable that is connected to
multiple readers, each receiver device generates a different 64-bit random
number and sends it in a challenge packet to Device A. Device A must then
transform each of these numbers and send a reply to each receiver device.
The principal strength of authentication is that it cannot be defeated by simple
record and playback of commands that implement the desired functions (for
example, unlocking the lock). Authentication does not require that the specific
