Interlogix NS3500-28T-4S User Manual User Manual
Page 222
222
LAN.
Until the client is authenticated, 802.1X access control allows only Extensible Authentication Protocol over LAN
(EAPOL)
traffic through the port to which the client is connected. After authentication is successful, normal traffic can
pass through the port.
This section includes this conceptual information:
Device Roles
Authentication Initiation and Message Exchange
Ports in Authorized and Unauthorized States
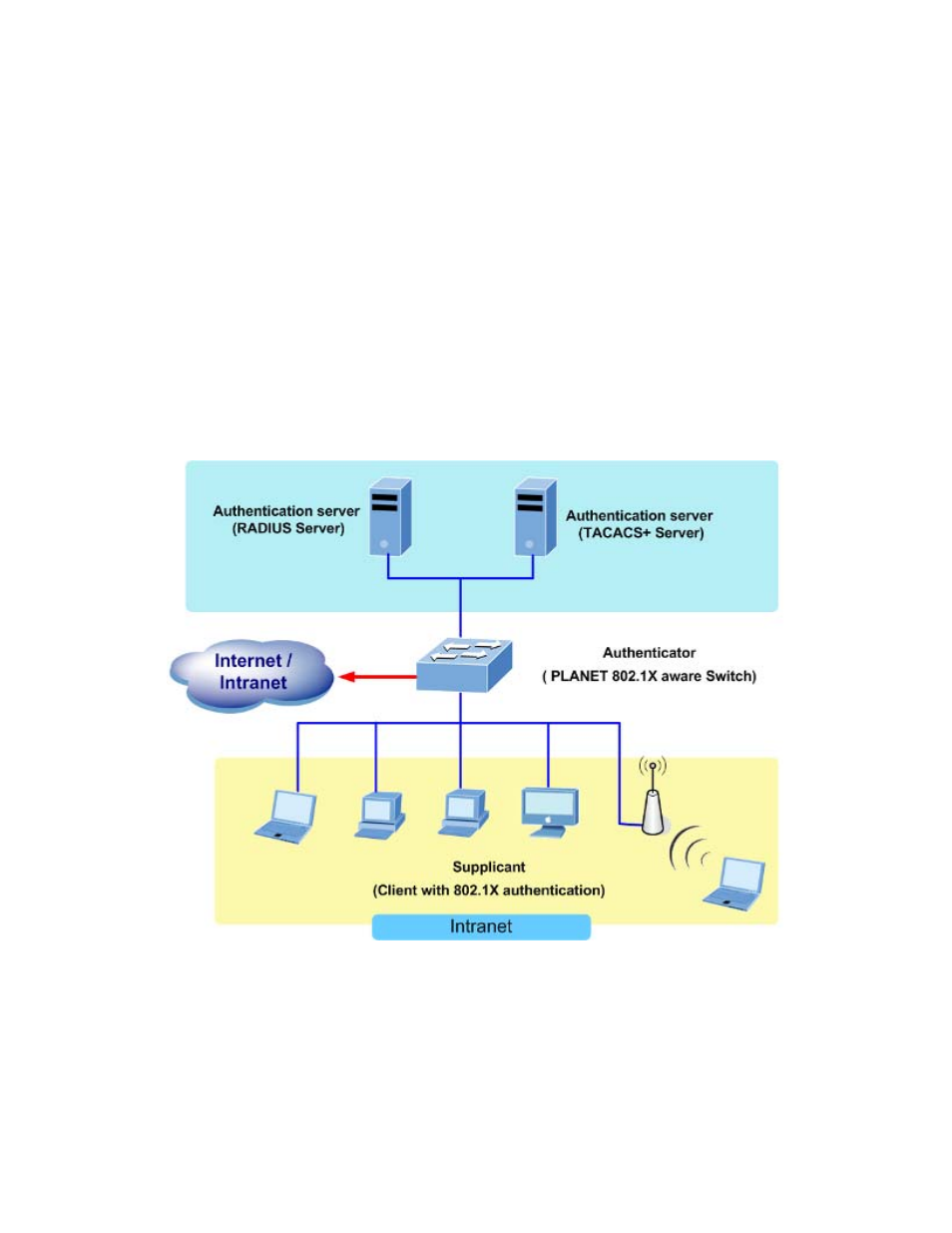
Device Roles
With 802.1X port-based authentication, the devices in the network have specific roles as shown below.
Figure 4-9-1
Client
—the device (workstation) that requests access to the LAN and switch services and responds to
requests from the switch. The workstation must be running 802.1X-compliant client software such as that
offered in the Microsoft Windows XP operating system. (The client is the supplicant in the IEEE 802.1X
specification.)
- 600-1053-4 (12 pages)
- NX-590NE (38 pages)
- NX-591NE-GSM (16 pages)
- NX-592E (13 pages)
- Simon XT CDMA Module V4 (9 pages)
- Simon XT GSM Module V4 (10 pages)
- NX-548E (12 pages)
- NX-540E (32 pages)
- D1000 Series (10 pages)
- D1300 Series (11 pages)
- D1315 Series (10 pages)
- D1810 Series (8 pages)
- D2100 Series (10 pages)
- D2300CPS Series (10 pages)
- D7100 Series (8 pages)
- D7400 Series (10 pages)
- D7400RSH Series (10 pages)
- DE7100 Series (9 pages)
- DE7200M Series (8 pages)
- DE7300 Series (9 pages)
- DECT3000 Series (8 pages)
- DED2500 Series (9 pages)
- DT3000 Series (6 pages)
- D1200 Series (8 pages)
- D19100SHR Series (16 pages)
- D9100 Series (12 pages)
- MC250-4T/1CXT (25 pages)
- MC251-4P/1CXT (28 pages)
- MC250-4T Series (23 pages)
- MC251-4P/1S (27 pages)
- MC350-4T-2S (32 pages)
- MC352-4P-2S (31 pages)
- MCR200-1T/1CX (25 pages)
- MCR200-1T-1TW (23 pages)
- MC250-1T/1S (24 pages)
- MCR205-1T/1S User Manual (62 pages)
- MCR205-1T/1S Installation Guide (11 pages)
- MC201-1P/1FS (20 pages)
- MC355-1T/1S Installation Guide (13 pages)
- MC350-1T-2S (29 pages)
- MC352-1P/1S (29 pages)
- MC355-1T/1S User Manual (64 pages)
- MCR300-1T/1S (20 pages)
- MCR300-1T-2S (17 pages)
- MCR-R15 (14 pages)
