SENA STS Series User Manual
Page 54
54
that the client portion of the handshake is finished.
9.
The server sends a message to the client informing it that future messages from the server will
be encrypted with the session key. It then sends a separate (encrypted) message indicating
that the server portion of the handshake is finished.
10. The SSL/TLS handshake is now complete, and the SSL/TLS session has begun. The client
and the server use the session keys to encrypt and decrypt the data they send to each other
and to validate its integrity.
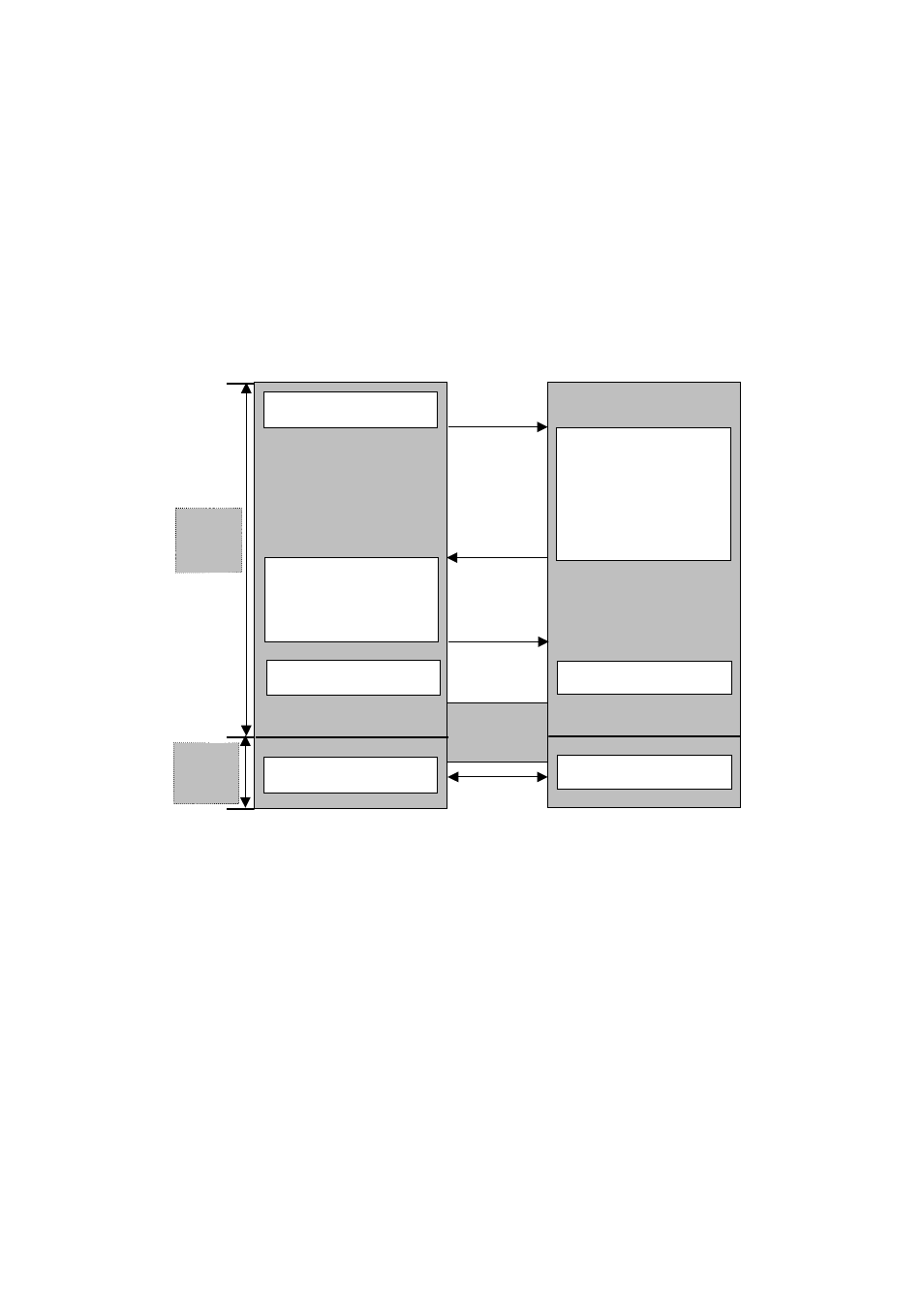
Client
Client Hello
Certificate
ClientKeyExchange
CertificateVerify
Application Data
ChangeCiperSpec
Server Hello
Certificate
ServerKeyExchange
CertificateRequest
ServerHelloDone
ChangeCiperSpec
Application Data
Handshake
Finished
Plain
Text
Cipher
Text
Server
Figure 4-10 Typical SSL/TLS Handshake Process
The STS Series can act as a SSL/TLS server or as a SSL/TLS client depending on status of TCP
mode. If TCP connection with SSL/TLS is initiated from remote host first, STS Series acts as a
SSL/TLS server during the SSL handshake process. On the contrary, if TCP connection with SSL/TLS
is initiated from serial port of STS Series first, STS Series acts as a SSL/TLS client during the SSL
handshake process.
When user uses SSL/TLS cryptography method, user can configure following parameters.
Enable/Disable cipher suites
A cipher suite is an object that specifies the asymmetric, symmetric and hash algorithms that are used
to secure an SSL/TLS connection. The asymmetric algorithm is used to verify the identity of the server
(and optionally, that of the client) and to securely exchange secret key information. The symmetric
