14 manual key setup, 1 security parameter index (spi) – ZyXEL Communications P-2802H(W)(L)-I Series User Manual
Page 202
Chapter 14 VPN Screens
P-2802H(W)(L)-I Series User’s Guide
202
14.14 Manual Key Setup
Manual key management is useful if you have problems with IKE key management.
14.14.1 Security Parameter Index (SPI)
An SPI is used to distinguish different SAs terminating at the same destination and using the
same IPSec protocol. This data allows for the multiplexing of SAs to a single gateway. The
SPI (Security Parameter Index) along with a destination IP address uniquely identify a
particular Security Association (SA). The SPI is transmitted from the remote VPN gateway to
the local VPN gateway. The local VPN gateway then uses the network, encryption and key
values that the administrator associated with the SPI to establish the tunnel.
Current ZyXEL implementation assumes identical outgoing and incoming SPIs.
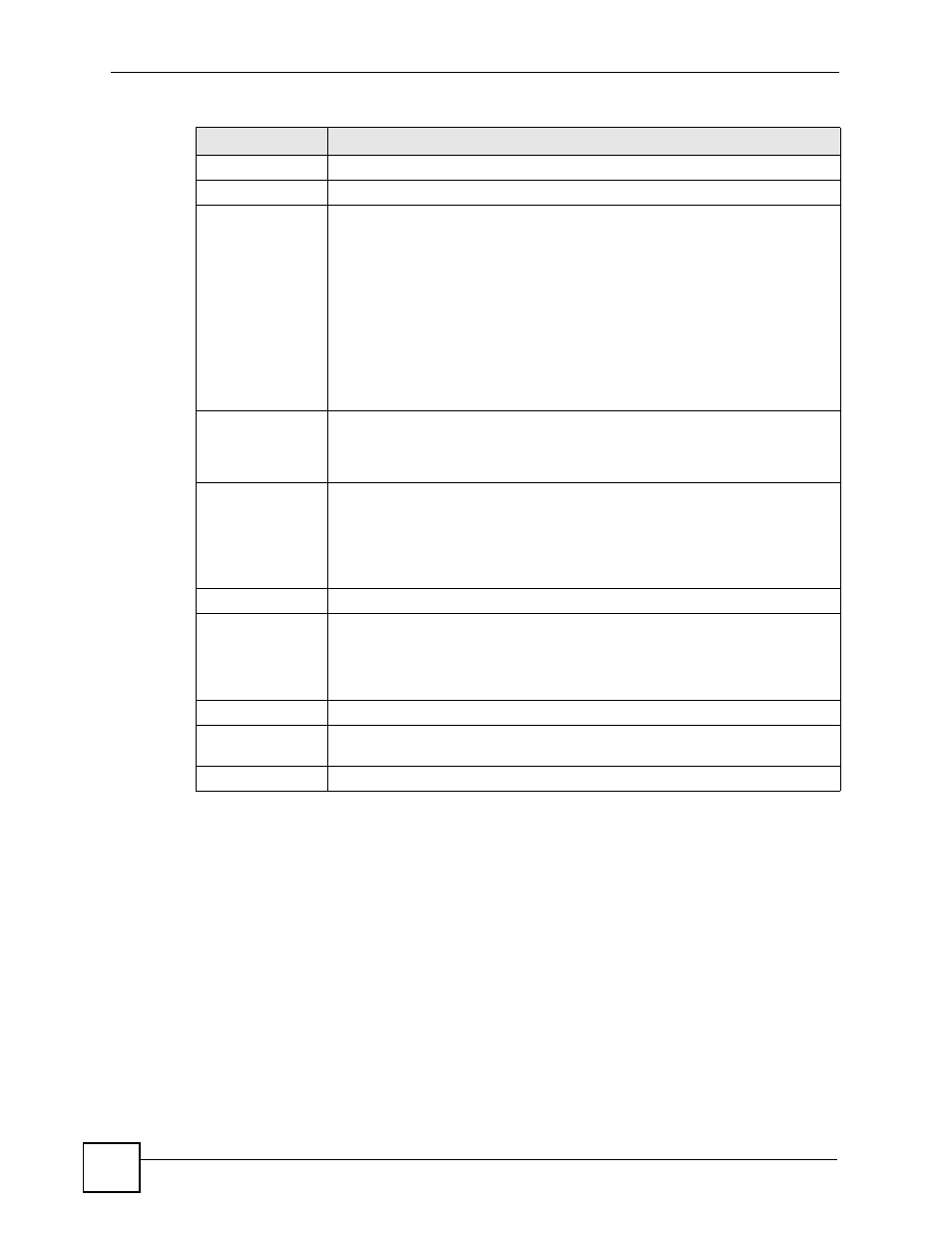
Phase 2
Active Protocol
Use the drop-down list box to choose from ESP or AH.
Encryption
Algorithm
This field is available when you select ESP in the Active Protocol field.
Select DES, 3DES, AES or NULL from the drop-down list box.
When you use one of these encryption algorithms for data communications, both
the sending device and the receiving device must use the same secret key, which
can be used to encrypt and decrypt the message or to generate and verify a
message authentication code. The DES encryption algorithm uses a 56-bit key.
Triple DES (3DES) is a variation on DES that uses a 168-bit key. As a result,
3DES is more secure than DES. It also requires more processing power, resulting
in increased latency and decreased throughput. This implementation of AES uses
a 128-bit key. AES is faster than 3DES.
Select NULL to set up a tunnel without encryption. When you select NULL, you
do not enter an encryption key.
Authentication
Algorithm
Select SHA1 or MD5 from the drop-down list box. MD5 (Message Digest 5) and
SHA1 (Secure Hash Algorithm) are hash algorithms used to authenticate packet
data. The SHA1 algorithm is generally considered stronger than MD5, but is
slower. Select MD5 for minimal security and SHA-1 for maximum security.
SA Life Time
(Seconds)
Define the length of time before an IKE SA automatically renegotiates in this field.
It may range from 60 to 3,000,000 seconds (almost 35 days).
A short SA Life Time increases security by forcing the two VPN gateways to
update the encryption and authentication keys. However, every time the VPN
tunnel renegotiates, all users accessing remote resources are temporarily
disconnected.
Encapsulation
Select Tunnel mode or Transport mode from the drop-down list box.
Perfect Forward
Secrecy (PFS)
Perfect Forward Secrecy (PFS) is disabled (NONE) by default in phase 2 IPSec
SA setup. This allows faster IPSec setup, but is not so secure. Choose DH1 or
DH2 from the drop-down list box to enable PFS. DH1 refers to Diffie-Hellman
Group 1 a 768 bit random number. DH2 refers to Diffie-Hellman Group 2 a 1024
bit (1Kb) random number (more secure, yet slower).
Back
Click Back to return to the previous screen.
Apply
Click Apply to save your changes back to the ZyXEL Device and return to the
VPN-IKE screen.
Cancel
Click Cancel to return to the VPN-IKE screen without saving your changes.
Table 78 Advanced VPN IKE
LABEL
DESCRIPTION
