9 ssh – PLANET WGSW-5242 User Manual
Page 110
User’s Manual of WGSW-5242
110
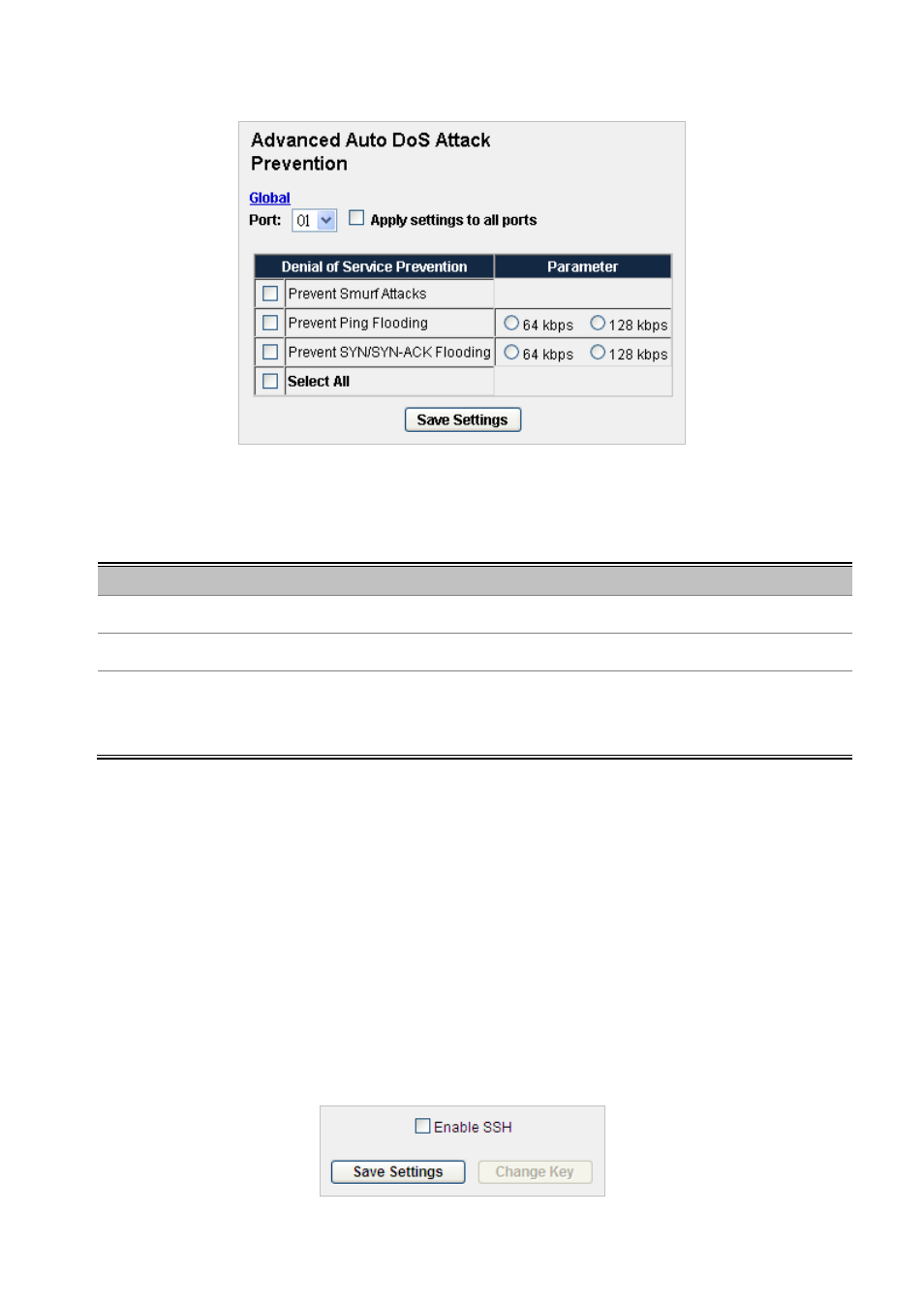
Advanced Auto DoS Attack Prevention
Figure 4-7-21
Advanced Auto DoS Attack Prevention screenshot
The page includes the following fields:
Object
Description
•
Prevent Smurf Attack
Packets with ICMP from broadcast address
•
Prevent Ping Flooding Packets with ICMP
•
Prevent
SYN/SYN-ACK
Flooding
Packets with SYN/SYN-ACK
4.7.9 SSH
SSH ( secure shell)
is a network protocol that allows data to be exchanged using a secure channel between two networked
devices. SSH was designed as a replacement for TELNET and other insecure remote shells, which sent information, notably
passwords, in plaintext, leaving them open for interception. The encryption used by SSH provides confidentiality and integrity of
data over an insecure network, such as the Internet.
SSH uses public-key cryptography to authenticate the remote computer and allow the remote computer to authenticate the user,
if necessary. SSH is typically used to log into a remote machine and execute commands.
An SSH server, by default, listens on the standard TCP port 22.
Figure 4-7-22
SSH page screenshot
