AirLive WN-300ARM-VPN User Manual
Page 32
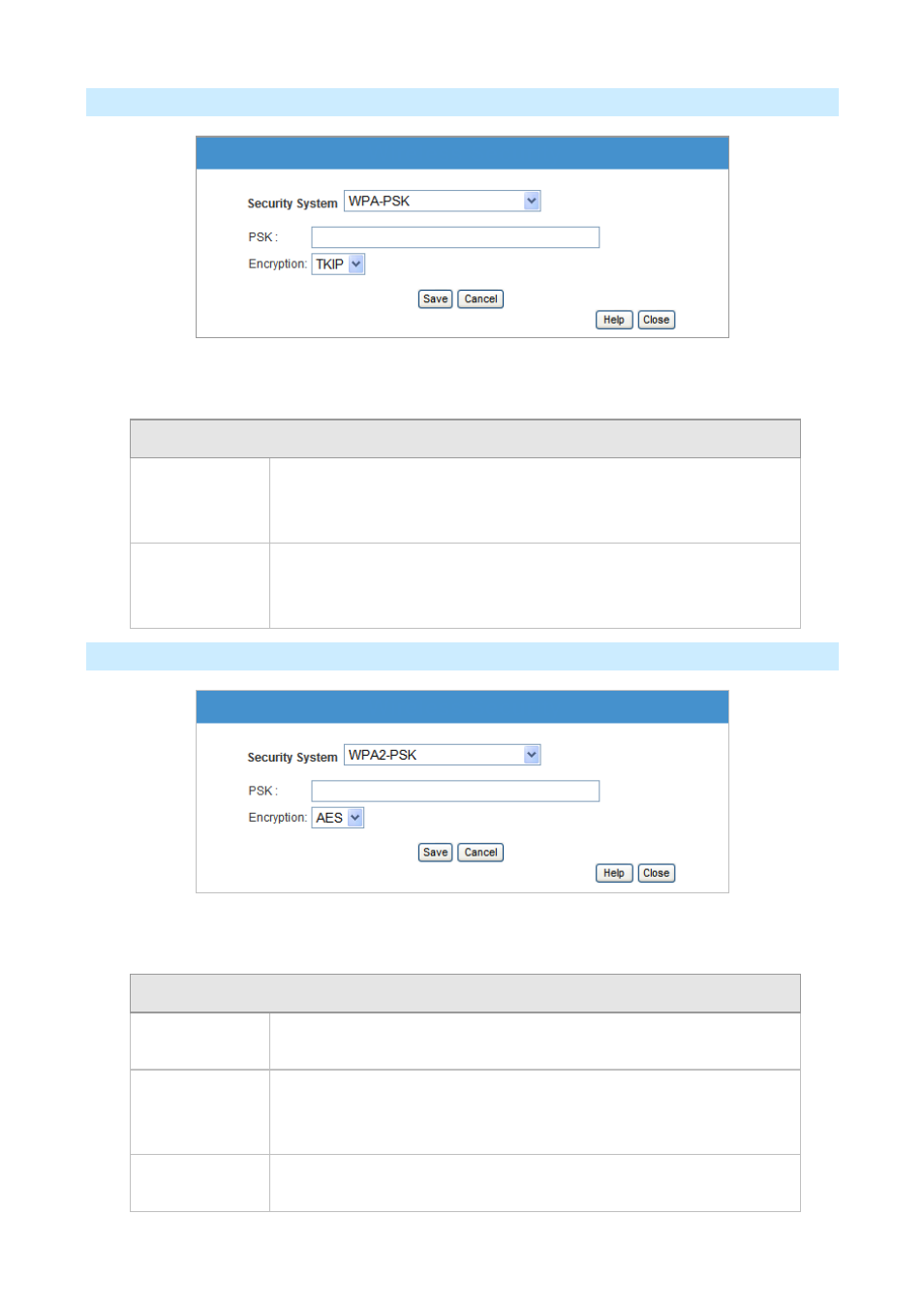
WPA-PSK Wireless Security
Figure: WPA-PSK
-2-
Data - WPA-PSK Screen
WPA-PSK Data Encryption
PSK
Enter the PSK (network key). Data is encrypted using a key derived from
the network key. Other Wireless Stations must use the same network key.
The PSK must be from 8 to 63 characters in length.
Encryption
The WPA-PSK standard allows different encryption methods to be used.
Select the desired option. Wireless Stations must use the same encryption
method.
WPA2-PSK Wireless Security
Figure: WPA2-PSK
-3-
Data - WPA2-PSK Screen
WPA2-PSK Data Encryption
Authentication
This is a further development of WPA-PSK, and offers even greater
security.
PSK
Enter the PSK (network key). Data is encrypted using a key derived from
the network key. Other Wireless Stations must use the same network key.
The PSK must be from 8 to 63 characters in length.
Encryption
The WPA2-PSK standard allows different encryption methods to be used.
Select the desired option. Wireless Stations must use the same encryption.
AirLive WN-300ARM-VPN User’s Manual
30
