Verification log, Verification log -15 – HP Storage Mirroring V5 Software User Manual
Page 104
14
-
15
7.
Specify if you want the verification process to
Use block checksum comparison/delta block transfer
to determine
which blocks are different. If this option is enabled, only those blocks (not the entire files) that are different will be
identified in the log and/or remirrored to the target.
8.
Click
OK
to save the settings.
Verification log
A verification log is created on the source during the verification process. The log identifies what is verified as well as which
files are not synchronized.
1.
Right-click the source server on the left pane of the Management Console and select
Properties
.
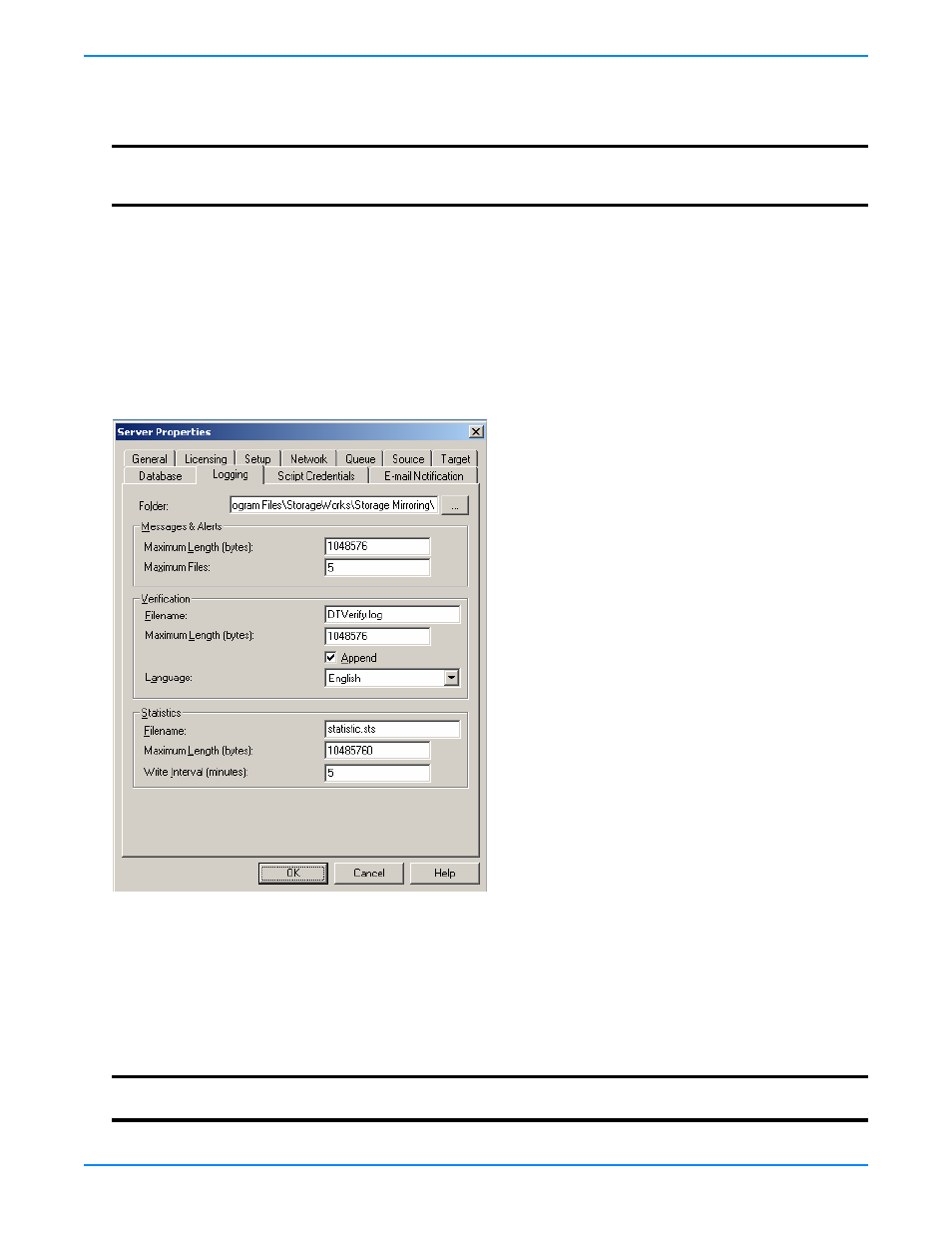
2.
Select the
Logging
tab.
3.
At the top of the window,
Folder
identifies the location where the log files identified on this tab are stored. By default,
the log files are stored in the same directory as the Storage Mirroring program files.
4.
Under the Verification section,
Filename
contains the base log file name for the verification process. The replication set
name will be prepended to the base log file name. For example, since the default is
DTVerify.log
, the verification log
for the replication set called
UserData
would be
UserData DTVerify.log
.
5.
Specify the
Maximum Length
of the log file. The default is
1048576
bytes (
1
MB). When the log file reaches this limit, no
additional data will be logged.
6.
By default, the log is appended to itself each time a verification process is completed. Clear the
Append
check box if you
do not want to append to the previous log file.
NOTE:
Database applications may update files without changing the date, time, or file size. Therefore, if you are
using database applications, you should use the block checksum comparison to ensure proper verification
and remirroring.
NOTE:
Changes made to the verification log in the
Server Properties,
Logging
tab will apply to all connections
from the current source machine.
