14 security parameters summary, Figure 40 wpa with radius application example, Table 13 wireless security relational matrix – ZyXEL Communications 802.11g Wireless Access Point ZyXEL G-560 User Manual
Page 73
ZyXEL G-560 User’s Guide
Chapter 6 Wireless Screens
73
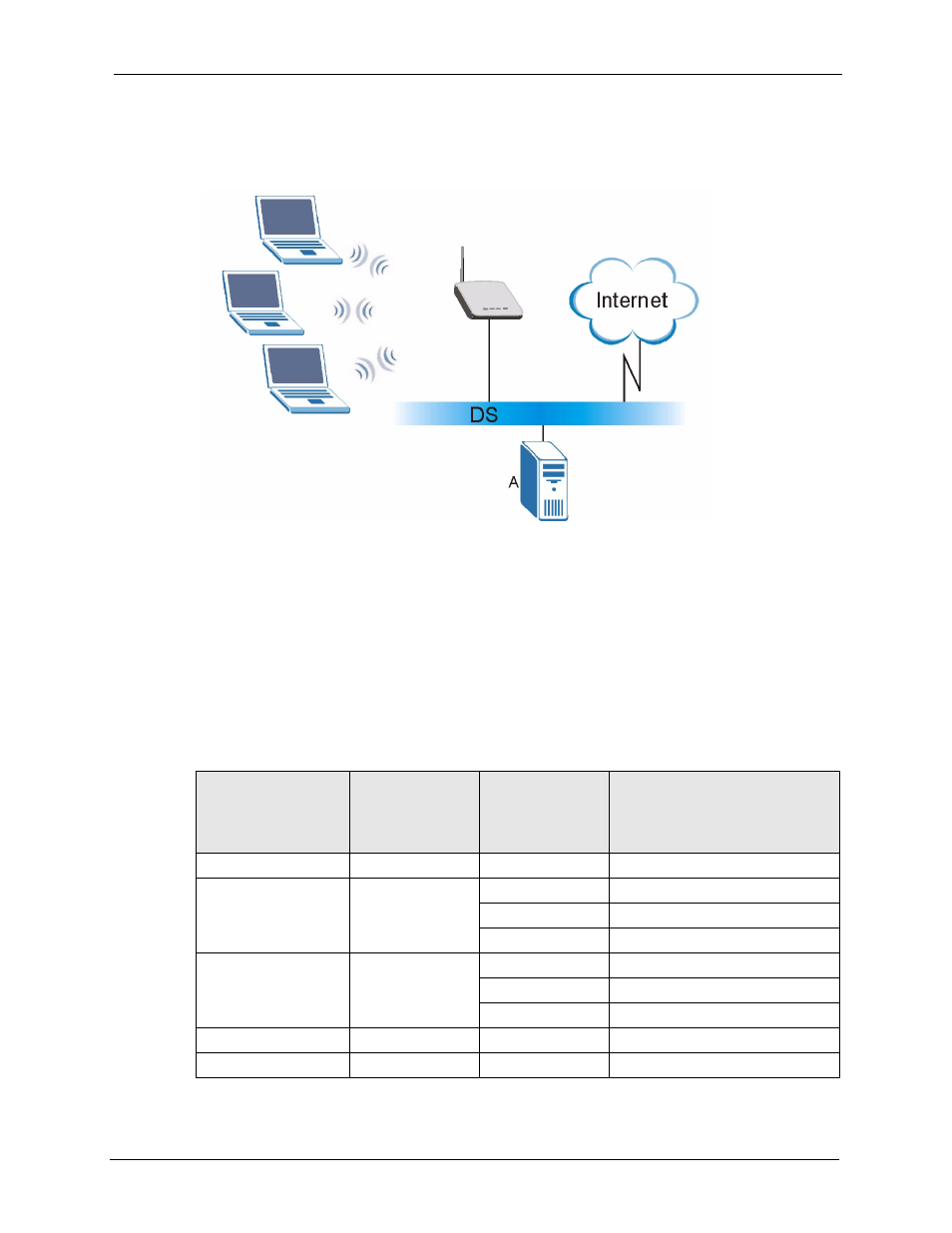
generate unique data encryption keys to encrypt every data packet that is wirelessly
communicated between the AP and the wireless clients.
Figure 40 WPA with RADIUS Application Example
6.14 Security Parameters Summary
Refer to this table to see what other security parameters you should configure for each
authentication method/ key management protocol type. You enter manual keys by first
selecting 64-bit WEP, 128-bit WEP or 256-bit WEP from the WEP Encryption field and
then typing the keys (in ASCII or hexadecimal format) in the key text boxes. MAC address
filters are not dependent on how you configure these security features.
Table 13 Wireless Security Relational Matrix
AUTHENTICATION
METHOD/ KEY
MANAGEMENT
PROTOCOL
ENCRYPTION
METHOD
ENTER MANUAL
KEY
IEEE 802.1X
Open
None
No
Disable
Open
WEP
No
Enable with Dynamic WEP Key
Yes
Enable without Dynamic WEP Key
Yes
Disable
Shared
WEP
No
Enable with Dynamic WEP Key
Yes
Enable without Dynamic WEP Key
Yes
Disable
WPA
TKIP
No
Enable
WPA-PSK
TKIP
Yes
Enable
