Anomaly, Anomaly list – Fortinet 100A User Manual
Page 284
284
01-28007-0068-20041203
Fortinet Inc.
Custom
IPS
Anomaly
The FortiGate IPS uses anomaly detection to identify network traffic that does not fit
known or preset traffic patterns. The FortiGate IPS identifies the four statistical
anomaly types for the TCP, UDP, and ICMP protocols.
You can enable or disable logging for each anomaly, and you can control the IPS
action in response to detecting an anomaly. In many cases you can also configure the
thresholds that the anomaly uses to detect traffic patterns that could represent an
attack.
You can also use the command line interface (CLI) to configure session control based
on source and destination network address. See
“Anomaly CLI configuration” on
.
The anomaly detection list can be updated only when the FortiGate firmware image is
upgraded.
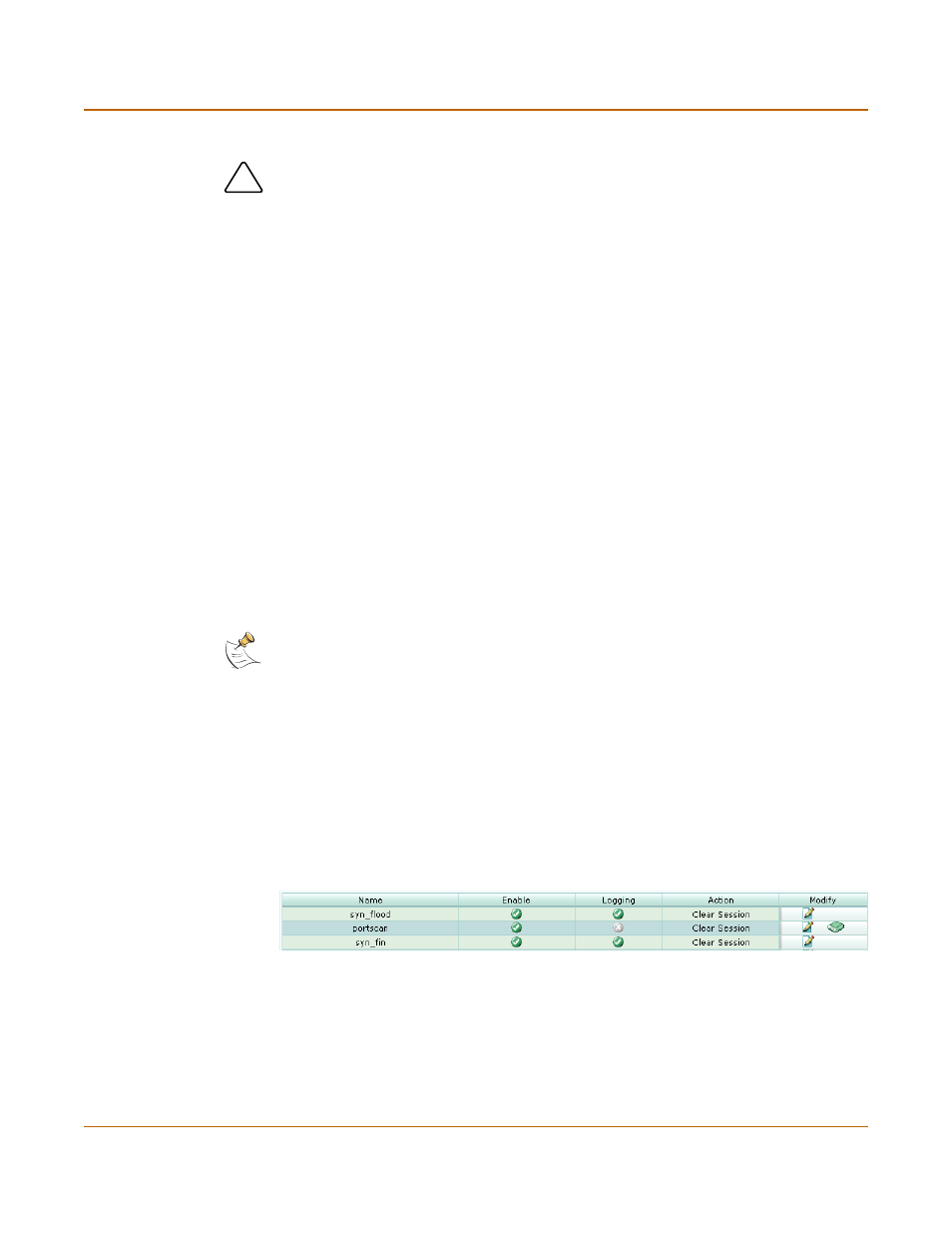
Anomaly list
Figure 149:The Anomaly list
!
Caution: Restoring the custom signature list overwrites the existing file.
Flooding
If the number of sessions targeting a single destination in one second is
over a threshold, the destination is experiencing flooding.
Scan
If the number of sessions from a single source in one second is over a
threshold, the source is scanning.
Source session
limit
If the number of concurrent sessions from a single source is over a
threshold, the source session limit is reached.
Destination
session limit
If the number of concurrent sessions to a single destination is over a
threshold, the destination session limit is reached.
Note: It is important to know the normal and expected traffic on your network before changing
the default anomaly thresholds. Setting the thresholds too low could cause false positives, and
setting the thresholds too high could miss some attacks.
Name
The anomaly names.
Enable
The status of the anomaly. A white check mark in a green circle indicates the
anomaly is enabled. A white X in a grey circle indicates the anomaly is
disabled.
Logging
The logging status for each anomaly. A white check mark in a green circle
indicates logging is enabled for the anomaly. A white X in a grey circle
indicates logging is disabled for the anomaly.
