Phase 2 advanced options – Fortinet 100A User Manual
Page 252
252
01-28007-0068-20041203
Fortinet Inc.
Phase 2 advanced options
VPN
Phase 2 advanced options
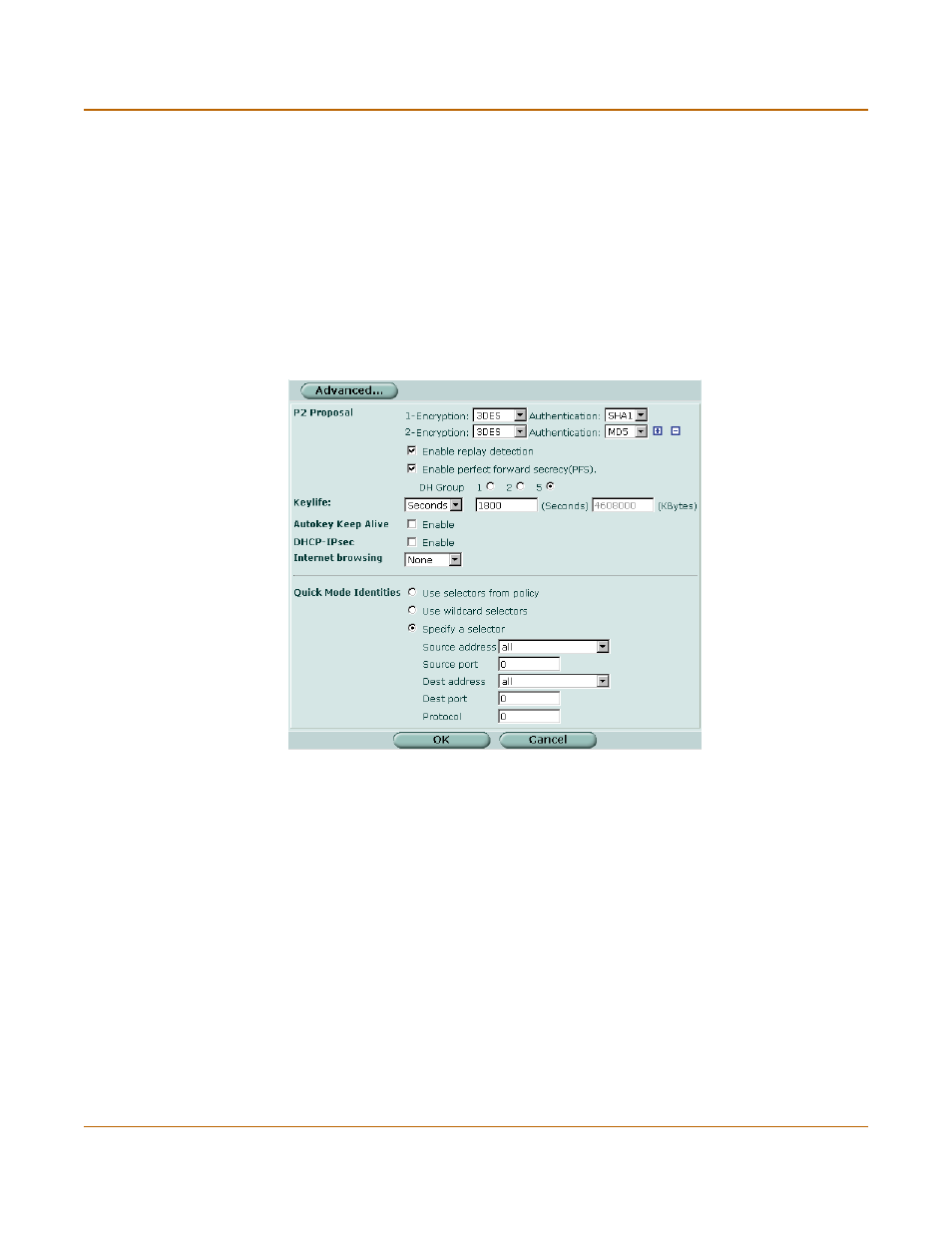
Figure 125:Phase 2 advanced settings
Tunnel Name
Type a name to identify the tunnel configuration.
Remote
Gateway
Select the phase 1 configuration to assign to this tunnel. See
. The phase 1 configuration describes how remote peers or clients
will be authenticated on this tunnel, and how the connection to the remote
peer or client will be secured.
Concentrator
If the tunnel will be included in a hub-and-spoke configuration, you may select
the concentrator from the list. The hub must be added to the FortiGate
configuration before it can be selected here. See
.
P2 Proposal
Select the encryption and authentication algorithms that will be used to
change data into encrypted code.
Add or delete encryption and authentication algorithms as required. Select a
minimum of one and a maximum of three combinations. The remote peer
must be configured to use at least one of the proposals that you define.
You can select any of the following symmetric-key algorithms:
•
NULL-Do not use an encryption algorithm.
•
DES-Digital Encryption Standard, a 64-bit block algorithm that uses a 56-
bit key.
•
3DES-Triple-DES, in which plain text is encrypted three times by three
keys.
•
AES128-A 128-bit block algorithm that uses a 128-bit key.
•
AES192-A 128-bit block algorithm that uses a 192-bit key.
•
AES256-A 128-bit block algorithm that uses a 256-bit key.
