Security management – Asante Technologies 8000 User Manual
Page 99
Security Management
Page 4-9
event. For information on configuring trap receivers, see “SNMP
Configuration” in Chapter 3.
Security Management
The IntraCore 8000’s security management options are summarized in
Table 4-2.
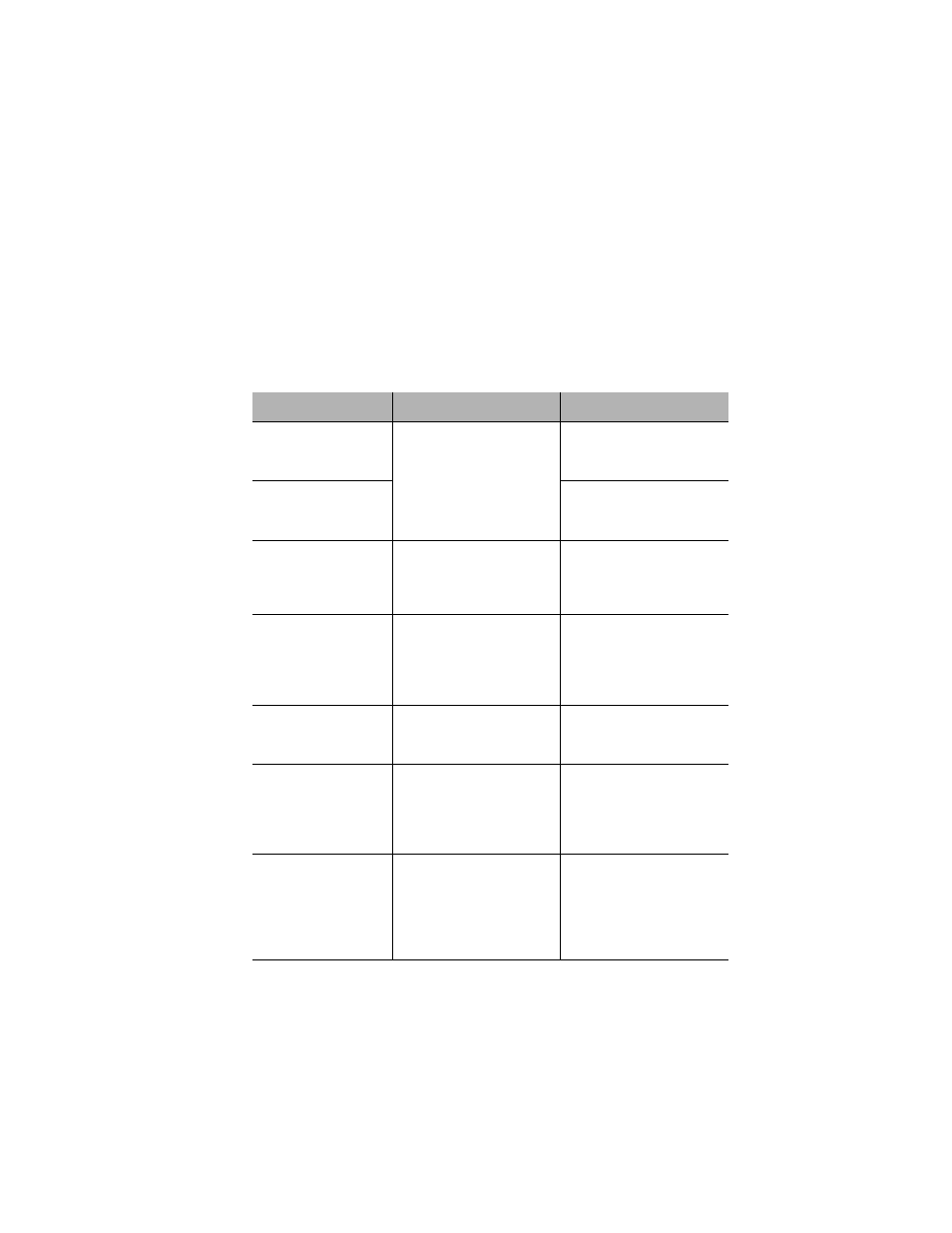
Table 4-2 Security Management Options
Security Option
Description
Action
Duplicated IP Detec-
tion (Monitoring)
Detects the use of a single IP
address by two stations.
Detects and logs MAC
addresses of both stations and
the ports they accessed.
Duplicated IP Trap
Sends trap with MAC
addresses of both stations and
the ports they accessed.
Station Movement Trap
Detects the movement of any
end station from one port to
another.
Sends trap with the station’s
MAC address and IP address
(if available) and the switch’s
port numbers.
Port New Node Trap
Detects the connection of any
new device to the secured
port.
Sends trap with the new
node’s MAC address and IP
address (if available) and the
port to which they are con-
nected.
Port Trusted MAC
Address
Creates a set of port-trusted
MAC addresses for use by
other security measures.
None.
Port Intruder Detection
Trap
Disallows traffic from MAC
addresses not belonging to
the port trusted MAC address
set. Station movement is also
disallowed.
Sends trap with intruder’s
MAC address.
Port Lock
Disallows traffic from MAC
addresses that do not belong
to the port trusted MAC
address set. Station move-
ment is also disallowed.
Disables the port if an
intruder is detected. Sends
trap with the port number, and
the intruder’s MAC address,
VLAN ID, and IP address (if
available).
