Table 89 pki logs – ZyXEL Communications NBG334W User Manual
Page 202
Chapter 20 Logs
NBG334W User’s Guide
202
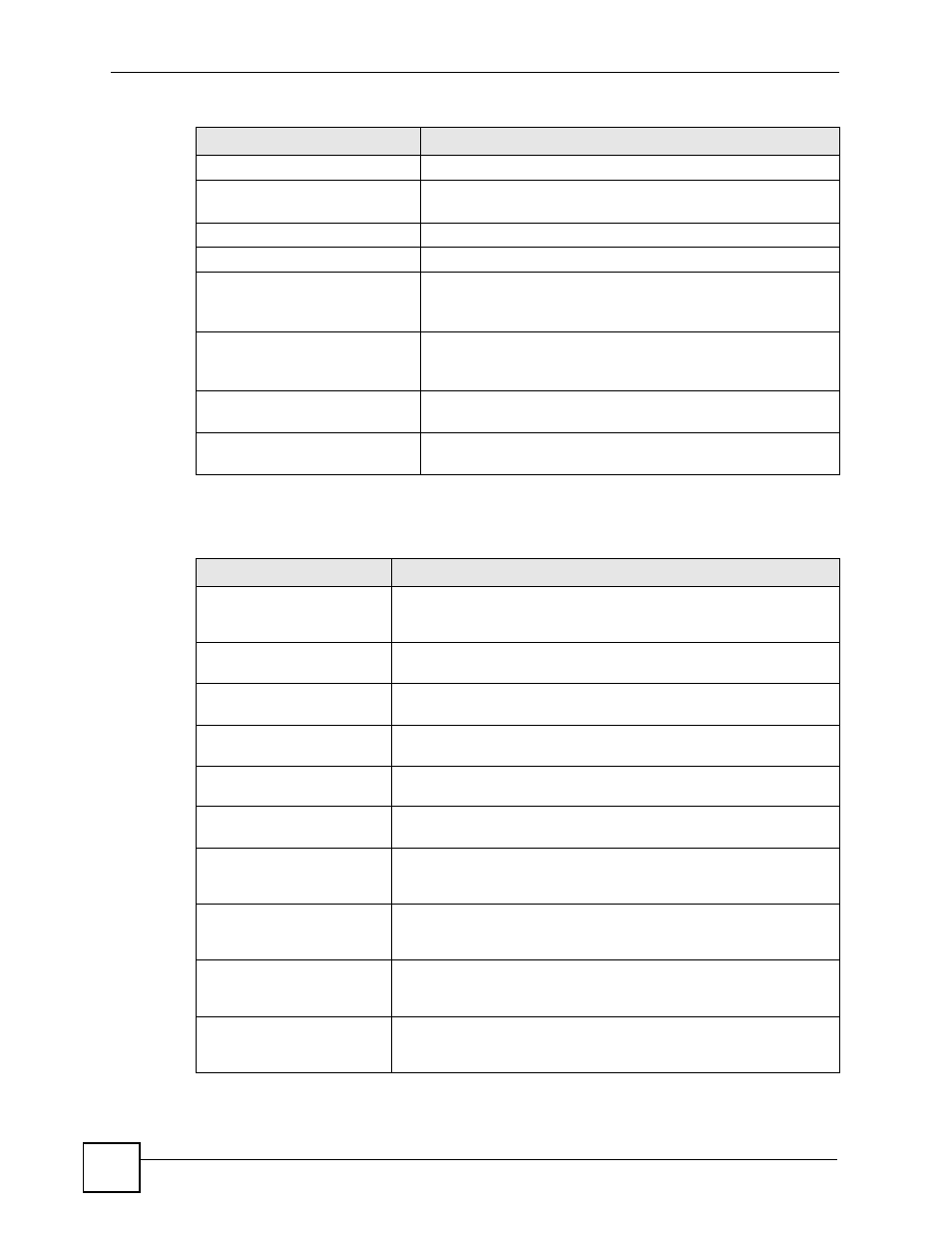
teardrop UDP
The firewall detected an UDP teardrop attack.
teardrop ICMP (type:%d,
code:%d)
The firewall detected an ICMP teardrop attack. For type and code
details, see
.
illegal command TCP
The firewall detected a TCP illegal command attack.
NetBIOS TCP
The firewall detected a TCP NetBIOS attack.
ip spoofing - no routing
entry [TCP | UDP | IGMP |
ESP | GRE | OSPF]
The firewall classified a packet with no source routing entry as an
IP spoofing attack.
ip spoofing - no routing
entry ICMP (type:%d,
code:%d)
The firewall classified an ICMP packet with no source routing
entry as an IP spoofing attack.
vulnerability ICMP
(type:%d, code:%d)
The firewall detected an ICMP vulnerability attack. For type and
.
traceroute ICMP (type:%d,
code:%d)
The firewall detected an ICMP traceroute attack. For type and
.
Table 89 PKI Logs
LOG MESSAGE
DESCRIPTION
Enrollment successful
The SCEP online certificate enrollment was successful. The
Destination field records the certification authority server IP address
and port.
Enrollment failed
The SCEP online certificate enrollment failed. The Destination field
records the certification authority server’s IP address and port.
Failed to resolve
The SCEP online certificate enrollment failed because the certification
authority server’s address cannot be resolved.
Enrollment successful
The CMP online certificate enrollment was successful. The Destination
field records the certification authority server’s IP address and port.
Enrollment failed
The CMP online certificate enrollment failed. The Destination field
records the certification authority server’s IP address and port.
Failed to resolve
The CMP online certificate enrollment failed because the certification
authority server’s IP address cannot be resolved.
Rcvd ca cert:
The router received a certification authority certificate, with subject
name as recorded, from the LDAP server whose IP address and port
are recorded in the Source field.
Rcvd user cert:
The router received a user certificate, with subject name as recorded,
from the LDAP server whose IP address and port are recorded in the
Source field.
Rcvd CRL
The router received a CRL (Certificate Revocation List), with size and
issuer name as recorded, from the LDAP server whose IP address and
port are recorded in the Source field.
Rcvd ARL
The router received an ARL (Authority Revocation List), with size and
issuer name as recorded, from the LDAP server whose address and
port are recorded in the Source field.
Table 88 Attack Logs (continued)
LOG MESSAGE
DESCRIPTION
