Configuration considerations, Configuration procedure, N in – H3C Technologies H3C SecPath F1000-E User Manual
Page 29: Figure 21, The in
21
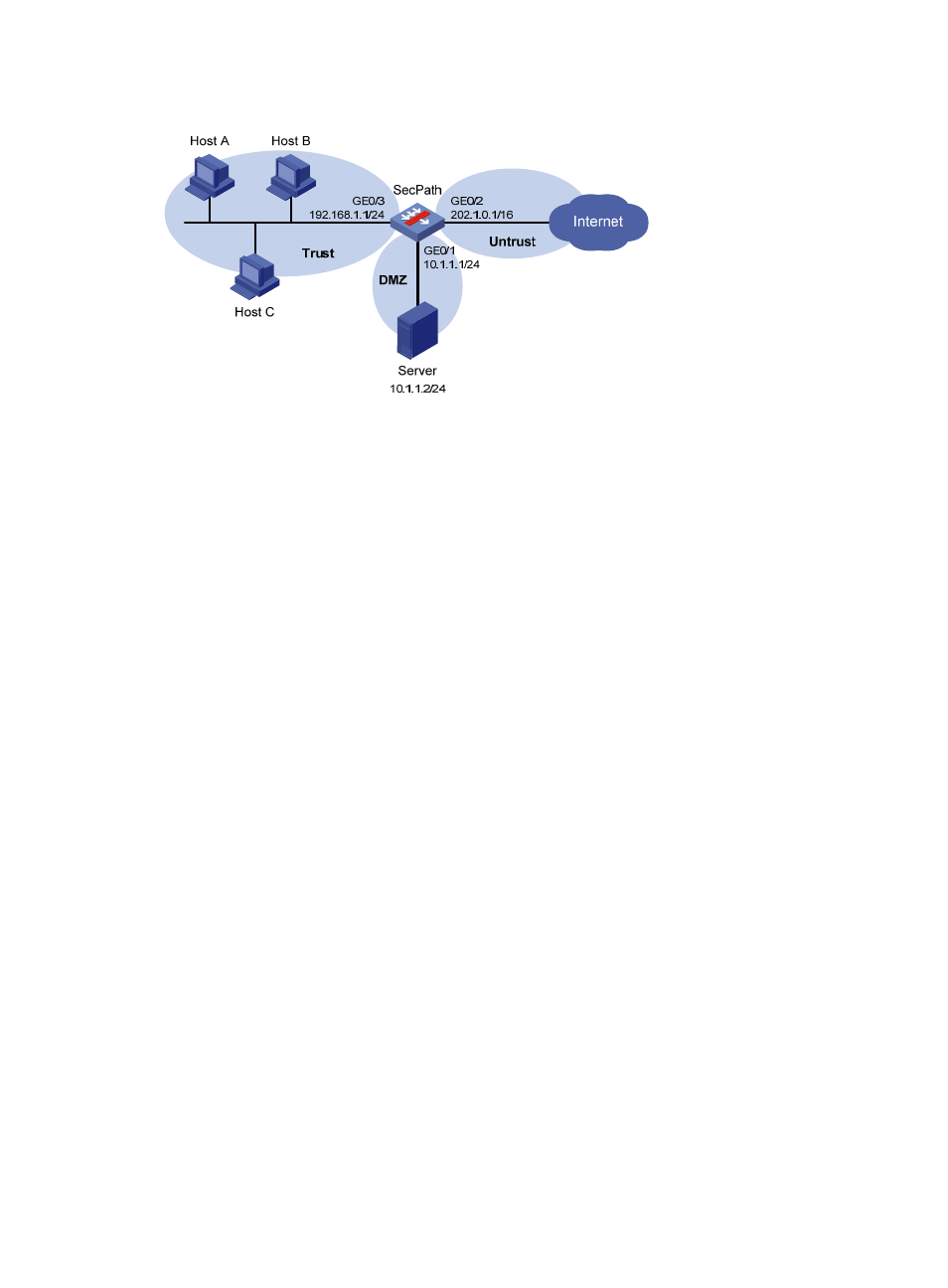
Figure 21 Network diagram
Configuration considerations
To satisfy the requirements, perform the following configurations on the SecPath:
•
Configure scanning detection for the untrusted zone, enable the function to add entries to the
blacklist, and set the scanning threshold to, for example, 4500 connections per second.
•
Configure source IP address-based connection limit for the trusted zone, and set the number of
connections each host can initiate to, for example, 100.
•
Configure destination IP address-based connection limit for the DMZ, and set the number of
connections the server can accommodate to, for example, 10000.
•
Configure SYN flood detection for the DMZ, and set the action threshold for attacks targeting the
internal server (for example, to 5000 packets per second) and the silent threshold (for example, to
1000 packets per second). Set the attack protection action to blocking subsequent packets destined
for the server.
Configuration procedure
# Assign IP addresses to interfaces. (Details not shown.)
# Enable the blacklist feature.
From the navigation tree, select Intrusion Detection > Blacklist. The blacklist management page appears,
as shown in
- H3C SecPath F5000-A5 Firewall H3C SecPath F1000-A-EI H3C SecPath F1000-E-SI H3C SecPath F1000-S-AI H3C SecPath F5000-S Firewall H3C SecPath F5000-C Firewall H3C SecPath F100-C-SI H3C SecPath F1000-C-SI H3C SecPath F100-A-SI H3C SecBlade FW Cards H3C SecBlade FW Enhanced Cards H3C SecPath U200-A U200-M U200-S H3C SecPath U200-CA U200-CM U200-CS
